SAML - Overview
What is SAML?
SAML stands for Security Assertion Markup
Language. It is an XML based open standard protocol used for Single Sign On (SSO). SAML lets users gain access to
multiple applications without the need for entering credentials everytime.What is Single Sign-on?
What is Single Sign-on?
Before understanding what Single Sign-On (SSO) is, we must go through how traditional authentication works.
- A
service will present the user with a login page where the user must
submit a set of login credentials i.e., username and passwords. Some
services might ask for more authentication information such as a
one-time password.
- The credentials submitted by the user are validated against the ones present in the database at the service.
Traditional
authentication is quite intuitive; everything is managed within the
service, providing a simple way for users to authenticate. However, if a
user needs to access multiple applications with a different set of
login credentials for each application, it quickly turns cumbersome for
the user. The user must remember multiple credentials and comply with
different password policies.
Single Sign-On is a feature which lets you access Zoho as well as third-party applications with one user credential. Users aren't required to remember an array of usernames and passwords for each application they need access to. Zoho uses SAML to achieve SSO with third-party applications.
Single Sign-On is a feature which lets you access Zoho as well as third-party applications with one user credential. Users aren't required to remember an array of usernames and passwords for each application they need access to. Zoho uses SAML to achieve SSO with third-party applications.
How does it work?
IdP initiated flow
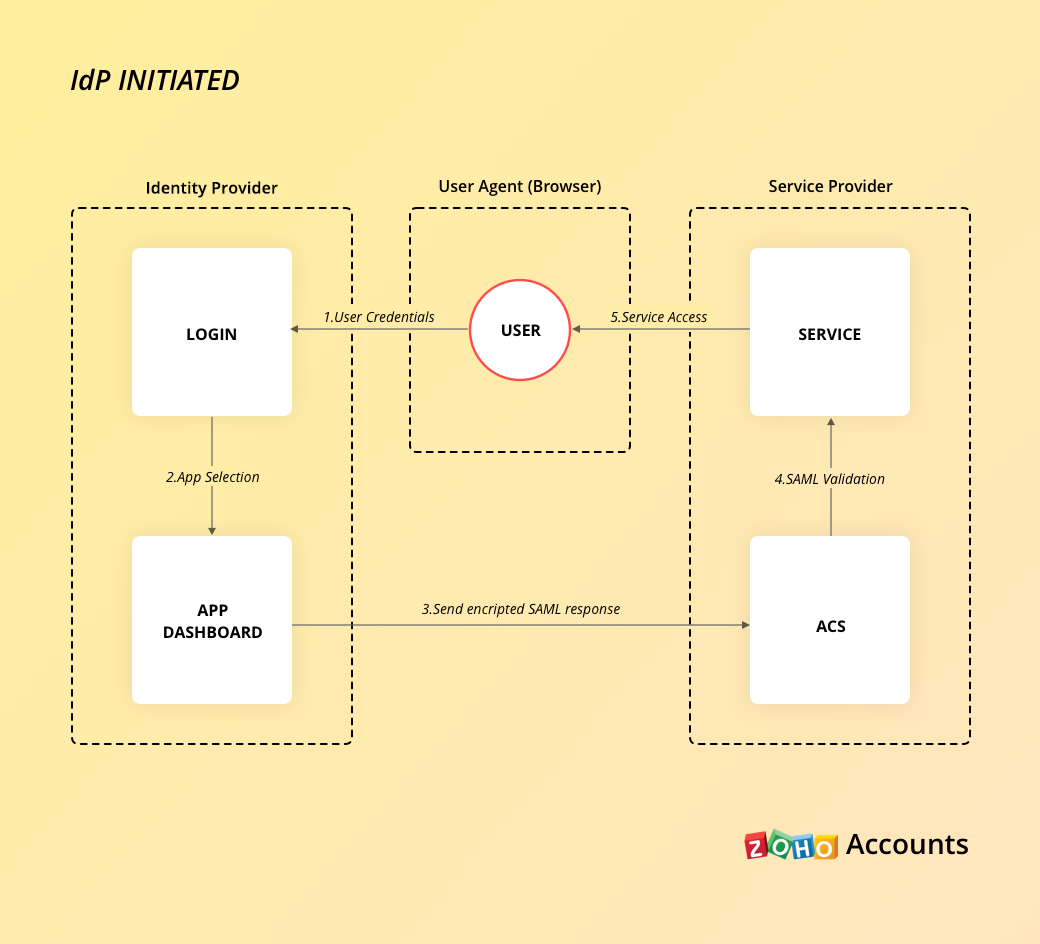
- The user wants to access a Zoho service.
- The user logs in to their Identity Provider (IdP )and chooses the Zoho application.
- IdP will create a signed SAML assertion response, which is sent to the ACS (Assertion Consumer Service) URL endpoint at Zoho.
- Zoho
will validate the SAML assertion response. Upon successful
validation, the user will be granted access to any Zoho services they
are authorized for.
SP initated flow
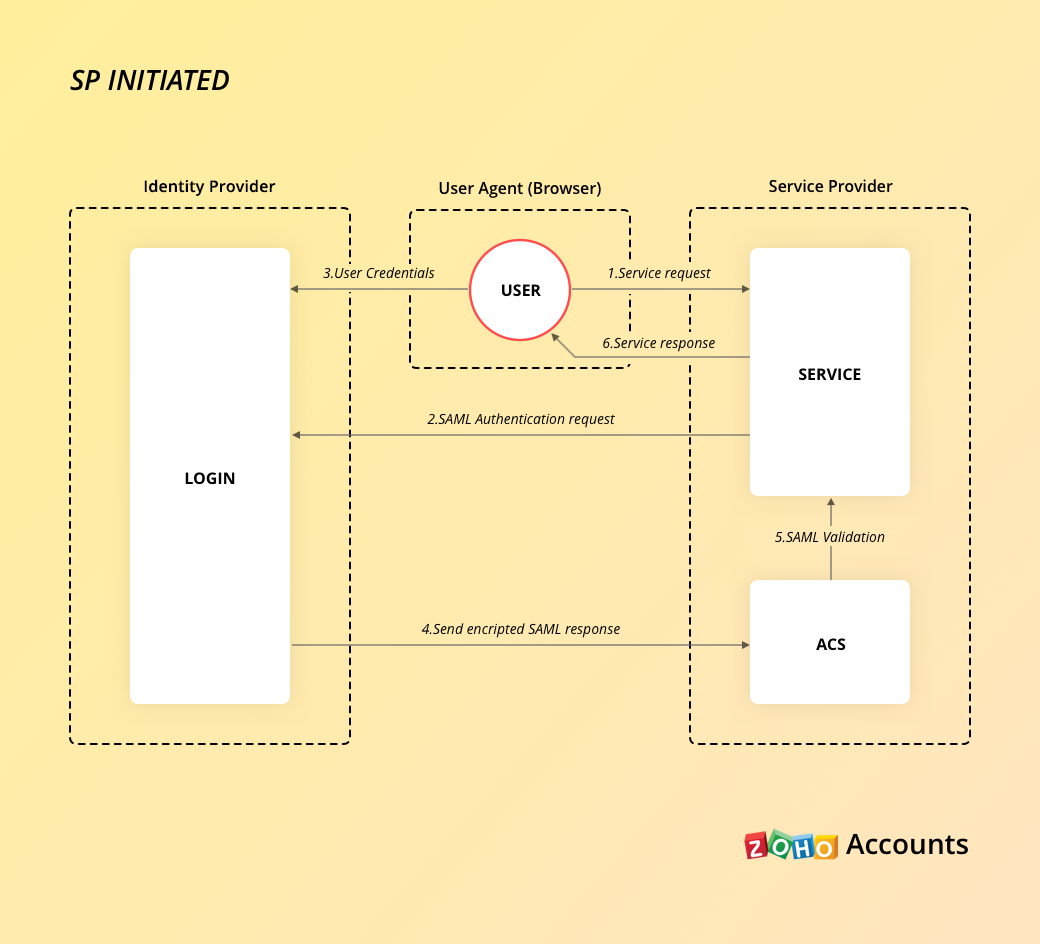
- The user wants to sign in to a Zoho service.
- Zoho generates an SAML authentication request and sends it to IdP via HTTP-Redirect binding.
- IdP will authenticate the user and form a signed SAML assertion response, which is sent to the ACS URL endpoint at Zoho.
- Zoho will validate the SAML assertion response. If the user is authorized to use the Zoho service, they will be granted access.
Check out how to configure SAML in Zoho Accounts and use various IdP's such as Google, Okta, OneLogin, Microsoft Entra ID, Auth0, ADFS to access Zoho applications using SAML
Zoho CRM Training Programs
Learn how to use the best tools for sales force automation and better customer engagement from Zoho's implementation specialists.
Zoho DataPrep Personalized Demo
If you'd like a personalized walk-through of our data preparation tool, please request a demo and we'll be happy to show you how to get the best out of Zoho DataPrep.
You are currently viewing the help pages of Qntrl’s earlier version. Click here to view our latest version—Qntrl 3.0's help articles.
Zoho Sheet Resources
Zoho Forms Resources
New to Zoho Sign?
Zoho Sign Resources
New to Zoho TeamInbox?
Zoho TeamInbox Resources
New to Zoho ZeptoMail?
Zoho DataPrep Resources
New to Zoho Workerly?
New to Zoho Recruit?
New to Zoho CRM?
New to Zoho Projects?
New to Zoho Sprints?
New to Zoho Assist?
New to Bigin?
Related Articles
SAML terminology
General terminology Single Sign-On (SSO) Single Sign-On (SSO) is the process of signing in to multiple services using a single set of credentials (as opposed to having separate credentials for different services). Using SSO, you can sign in to your ...Troubleshoot SAML related errors
Error Message Reason Solution Your organization has configured SAML authentication, please sign in via SAML credentials You cannot sign in to your Zoho account via any linked account, if your organization has mandated you to sign in only through SAML ...Configure SAML in Zoho Accounts
Note: If you want to configure SAML for Zoho One/ Zoho Directory, you can refer to their respective help documents: Zoho One | Zoho Directory To create a SAML connection between Zoho and your identity provider (IdP), you will need to provide some ...Accessing Zoho via AWS using SAML
By configuring SAML-based SSO with AWS, you can let your users sign in to Zoho using their AWS credentials. Required items from AWS: You will need the following items from AWS to configure SAML in Zoho. You can follow the configuration steps to get ...Accessing Zoho via Google using SAML
You can use Google as an identity provider (IdP) to access Zoho applications. Google IdP is a user management platform for Google Apps and services. Required items from Google You will need the following items from Google to configure SAML in Zoho. ...
New to Zoho LandingPage?
Zoho LandingPage Resources













