Single Sign-On (SSO) for Portal
SSO is an authentication service that allows a user to use single login to access multiple applications. SSO uses Security Assertion Markup language (SAML) for exchanging authentication between the applications.
SAML
Security Assertion Markup Language (SAML) is an open-standard for exchanging authentication and authorization data between two parties ie., Service Provider (SP) and Indentity Provider (IdP).
Service Provider agrees to trust the Identity Provider for authenticating the user. Identity Provider generates authenticating assertion for the user and communicate that with Service Provider.
The most important use case that SAML addresses is web browsers single sign-on (SSO). Single sign-on can be established between different domains.
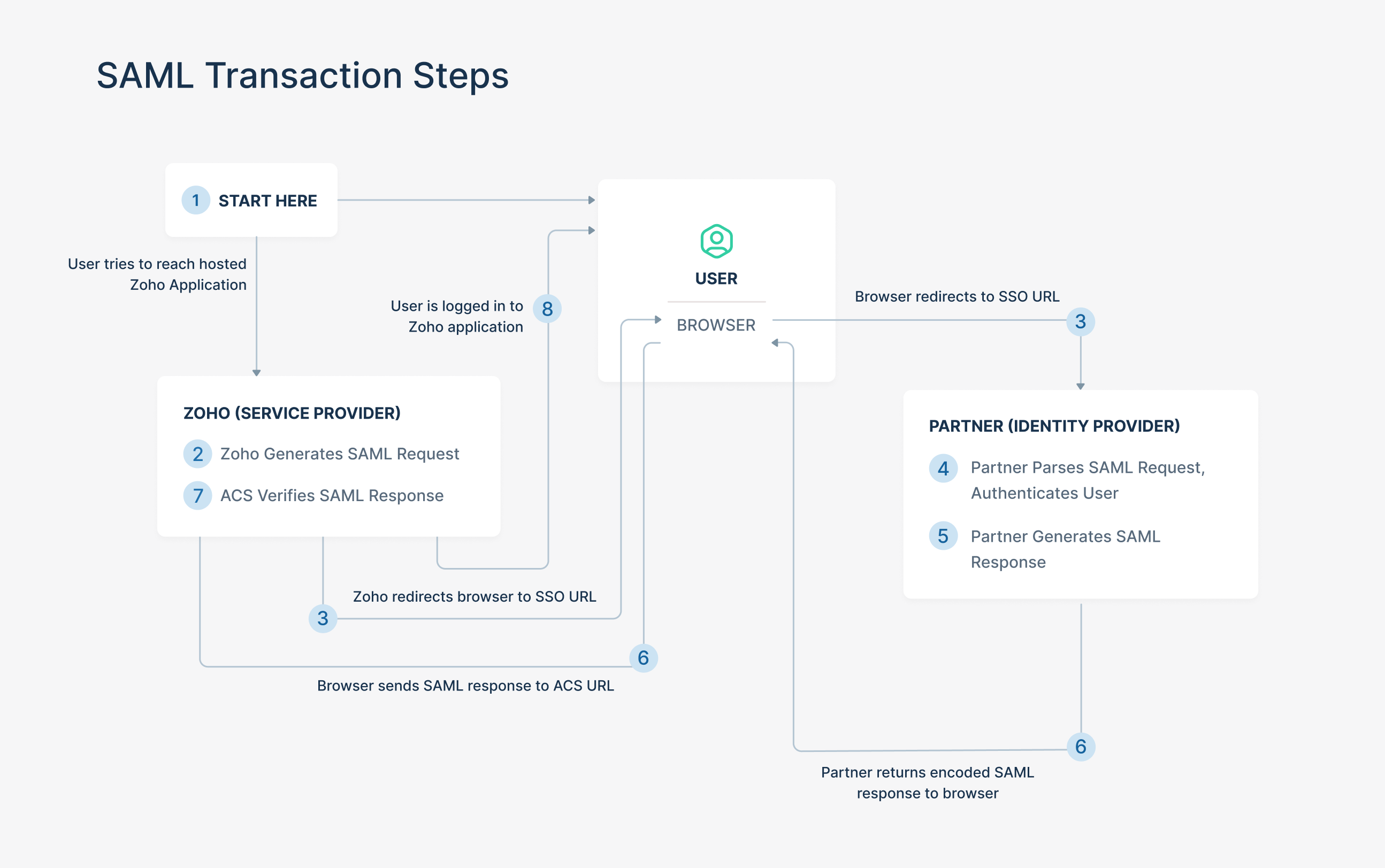
How SSO works?
SSO involves three parties
- User
- Service Provider (Ex: Zoho)
- Identity Provider (Ex: OneLogin, Google etc.,)
Let’s look at the SSO workflow,
User requests a service from the Service Provider.
Service Provider requests authentication assertion from the Identity Provider.
Based on the assertion, Service Provider makes decision to the user’s request.
To whom does this fit?
Merchants who maintain user accounts on their end and still require Zoho Billing’s Customer Portal for billing.
For Example:
Let us consider, a merchant has an online book store (say, www.zylker.com). He maintains user accounts on their end. The user has to login to www.zylker.com to make a purchase. To ease the work, the merchant decides to use Zoho Billing’s Customer Portal for billing and payments, i.e., to make payment, update credit card and verify past transactions.
- www.zylker.com is to maintain their account and checkout
- www.billing.zoho.com/portal/zylker is for billing and payments.
But wait, should the user login to both the accounts?
That’s right. User needs to login both the servers.
Thus, the merchant's requirement is,
1. Customer will be using both the accounts.
2. Customer who logs in to www.zylker.com, will be automatically logged in to
www.billing.zoho.com/portal/zylker (Zoho Billing's Portal)
Well, enabling SSO between two systems can do that.
Enable SSO for the Customer portal
I. Decide your IdP
An Identity Provider (IdP) is a service that verifies and manages user identities for secure access to websites or applications. It can be:
- Third party vendor (Ex: Google, OneLogin)
- Your own application
II. Configure SSO
Here’s how you can enable SSO configuration:
- Go to Settings in the top-right corner of the page.
- Select General under Customer Portal.
- Go to Portal Login and select SSO(Single Sign-On)
- Click Configure and enter the required fields.
| Field | Description |
|---|---|
| Login URL | The URL of your Identity Provider (IdP) to which Zoho Billing will redirect your end users when they attempt to log in to the Customer Portal. |
| Logout URL | The URL where Zoho Billing will redirect end users when they initiate the logout process from the Customer Portal to ensure they are properly logged out of both the Customer Portal and the IdP. |
| Password Reset URL | The URL where Zoho Billing will redirect end users who want to change their portal account’s password. This allows users to securely update their password within the IdP’s system. |
| Public Key | Upload the Public X.509 certificate in text format. This certificate contains the public key that Zoho Billing uses to verify SAML authentication requests from your IdP, ensuring secure communication. |
- Click Configure Now.
- Click Save at the bottom of the page. The SSO will be enabled. To complete the set up, copy the ACS URL from the Portal SSO configuration page and configure it in your IdP.
Disable SSO for the Customer portal
Here’s how you can disable the SSO configuration:
- Go to Settings in the top-right corner of the page.
- Select General under Customer Portal.
- Click the More icon next to Portal SSO (Single Sign-On).
- Select Disable.
- Click Disable SSO to confirm.
Once disabled, your existing IdP’s configuration data will be removed and your customers will no longer be able to use a single set of credentials for signing in.


 Yes
Yes