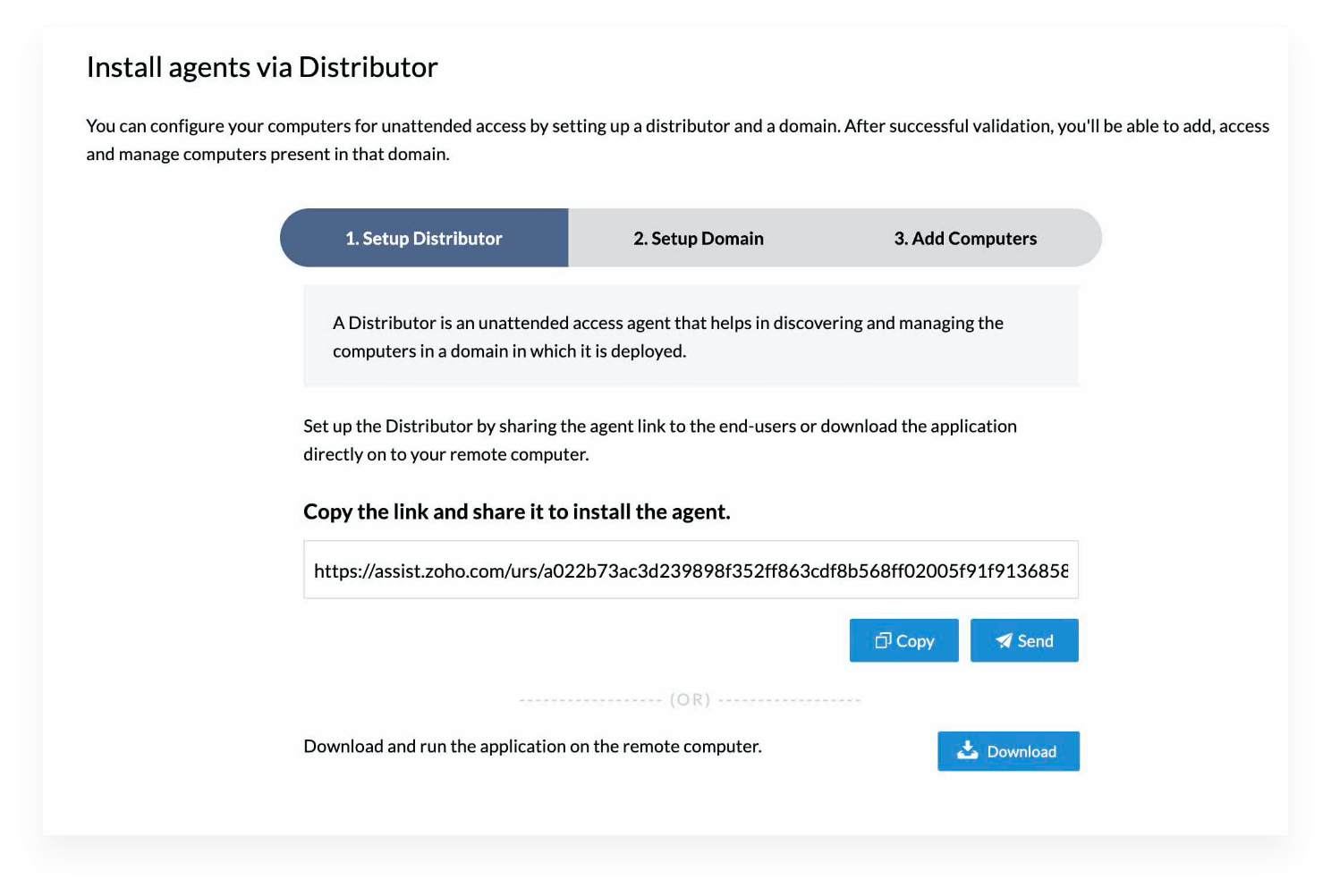
Bulk deployment for configuring unattended access.
Configure unattended remote access for a large group of devices using Zoho Assist's bulk deployment process. You can use the Distributor or Start-up script to install the unattended remote agent onto your remote devices. Read more.
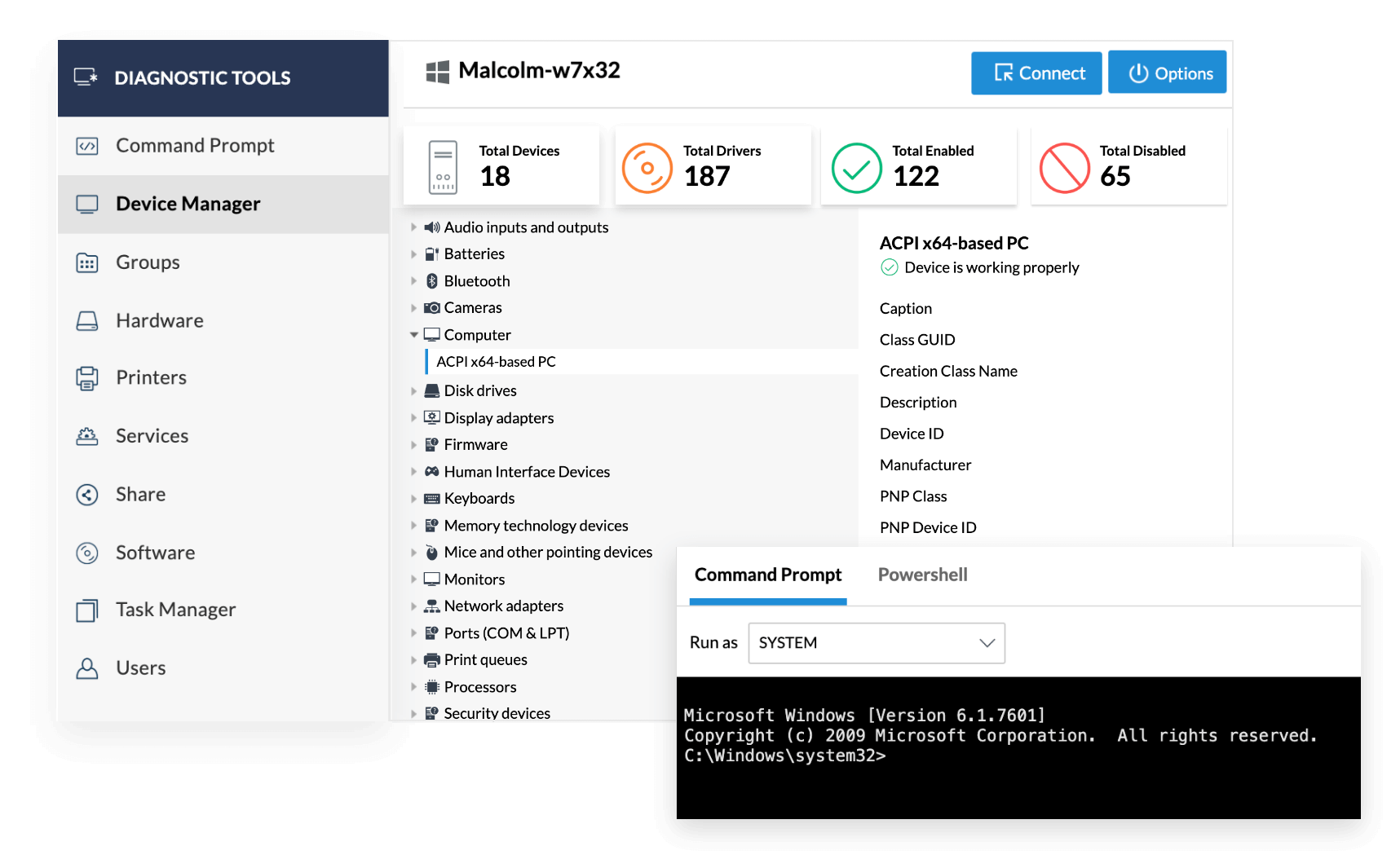
Diagnostic tools
Perform native system diagnostic operations, such as looking at active tasks using Task manager, opening the command prompt, and analyzing the status of groups, hardware, printers, services, software, and users associated with each computer using Zoho Assist - Remote desktop software.
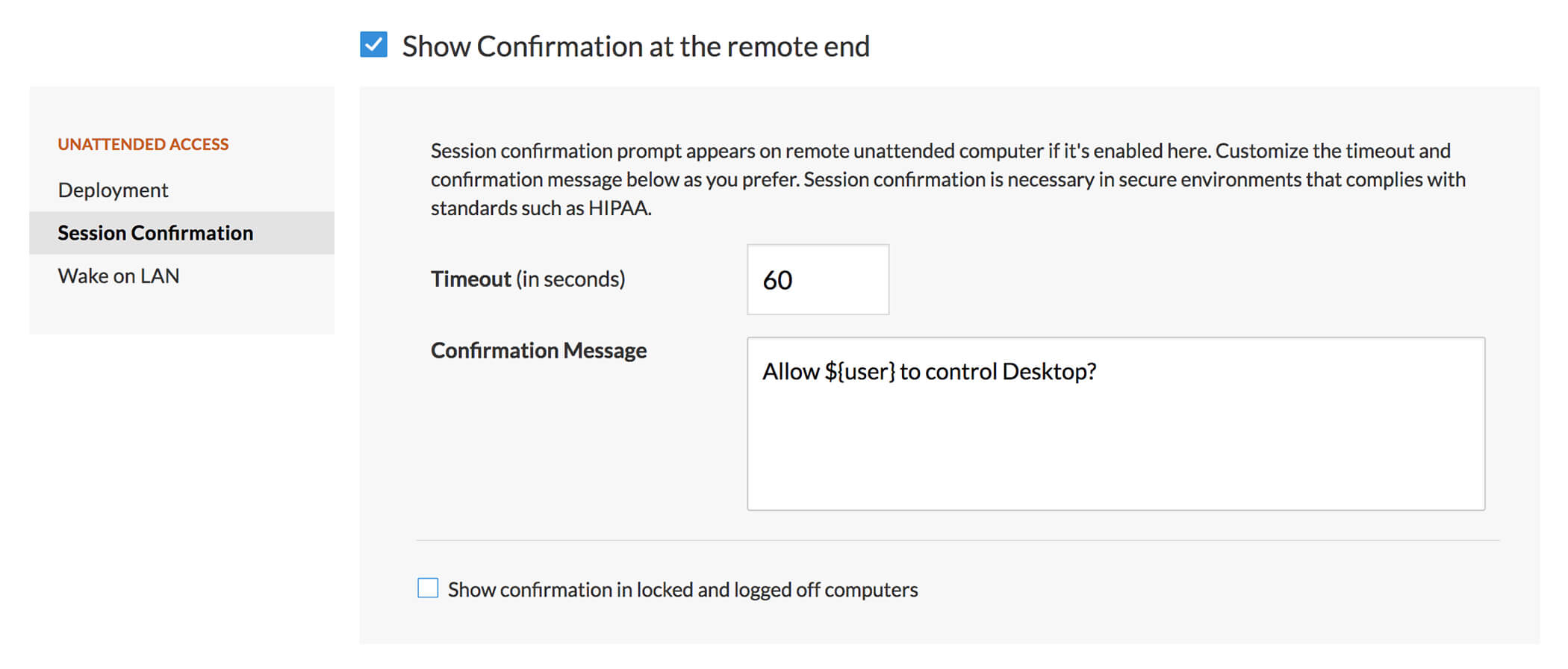
Consent-based unattended remote access with session confirmation.
Protecting user privacy is an important aspect of becoming HIPAA compliant. With session confirmation, allow your customer to consent to initiate unattended remote support sessions via the remote support tool for IT. You can even customize the time-out limit and confirmation message.
Wake on LAN
Have trouble accessing offline computers? With Wake on LAN, you can turn on sleeping or powered-off computers with a single click. The Wake on LAN feature goes a long way toward helping you reach computers which are otherwise unreachable.
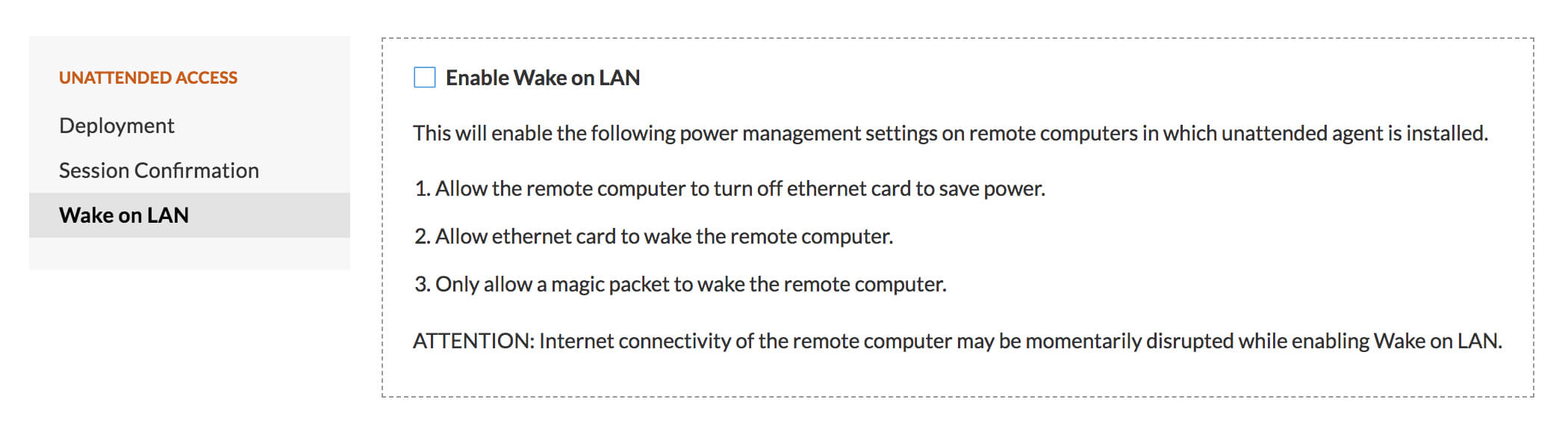
Shutdown & restart unattended computers
Have to start a session every time you want to turn off a remote desktop? With remote power options, you can execute power actions like shutdown, restart, log off, lock, hibernate, or standby, without even accessing a unattended access desktop.
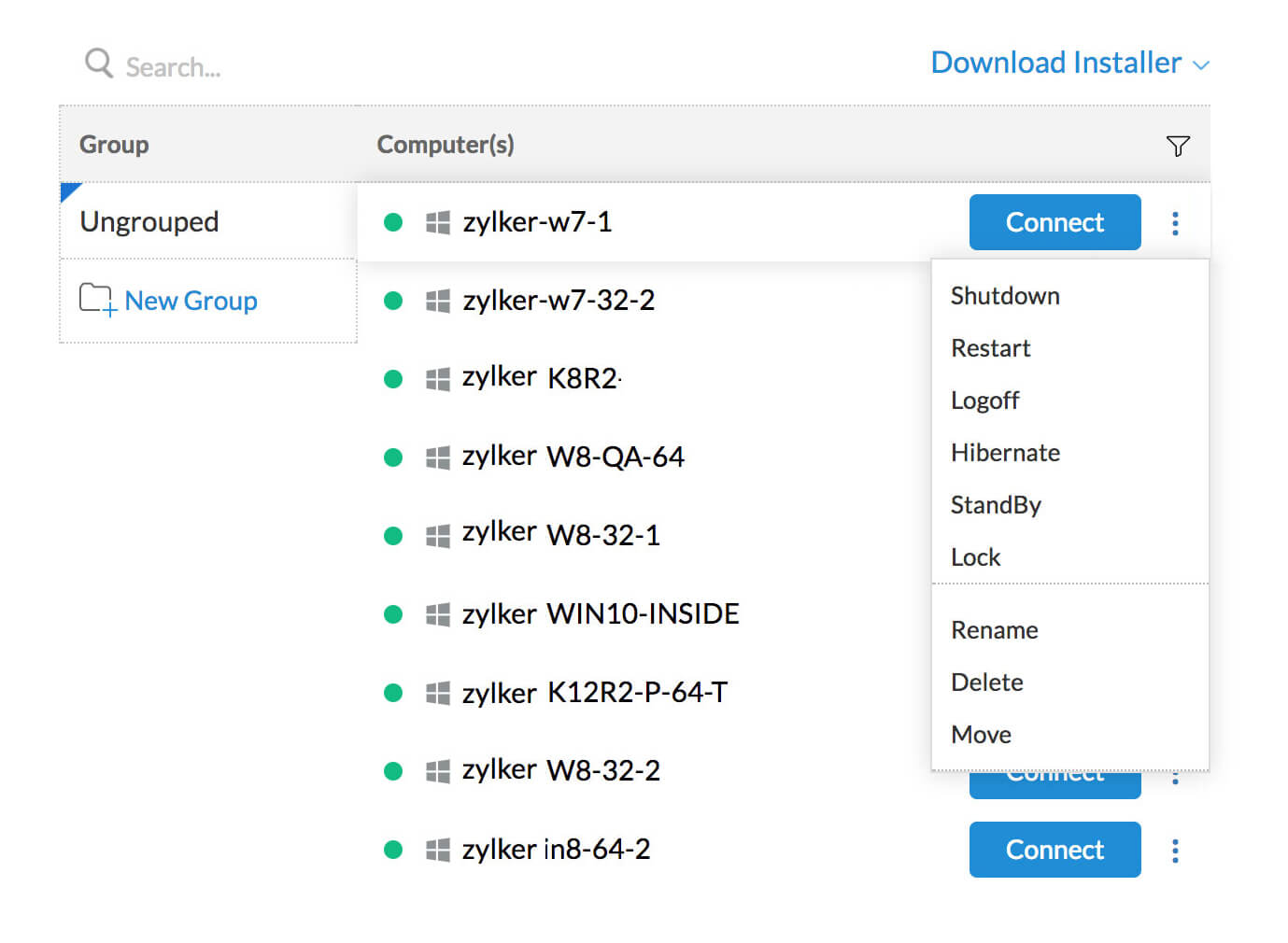
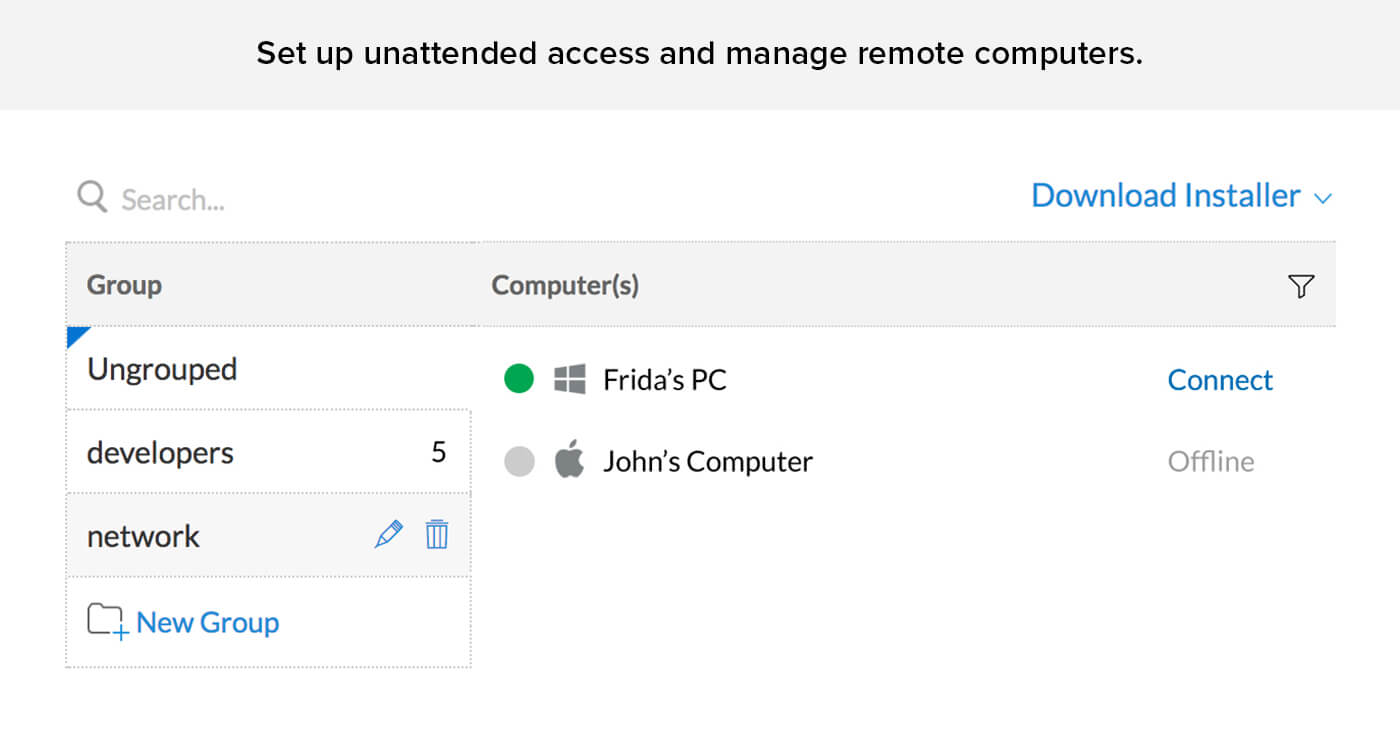
Setup unattended remote access & manage devices
Keeping things in order is always a good call. Zoho Assist, unattended remote access software offers you an easy way to organize computers configured in your organization account—group, sort, and name them however you want.
Define group permissions, authorize remote access
Managing multiple technicians and a large number of computers is a recipe for chaos. Use group permissions to reduce confusion by defining the computer groups that each technician is permitted to access.
Frequently Asked Questions
Unattended remote access allows you to connect to and control a remote computer or device without a user present at the other end to grant permission. It's ideal for managing servers, updating software, and performing maintenance tasks.
Unattended remote access streamlines IT tasks by allowing technicians to access devices anytime, even outside of regular business hours. It's particularly useful for resolving issues promptly and performing routine maintenance.
Zoho Assist - best remote desktop software employs industry-standard SSL and 256-bit AES encryption and authentication protocols to ensure that only authorized users can access remote devices, making it safe to connect to unattended devices through the application.
Zoho Assist allows you to configure unattended access for multiple devices, so you can easily manage a group of computers or servers.
Remote support is typically initiated by an end user seeking assistance, while unattended access is preconfigured and allows technicians to connect without user intervention. Unattended access is more suitable for tasks that don't require user participation.
Yes, as an administrator or device owner, you can revoke unattended access permissions at any time, ensuring complete control over who accesses your devices.
Zoho Assist supports unattended access on a wide range of platforms, including Windows, macOS, and various Linux distributions.
Unattended access is suitable for personal use as well. It's beneficial for accessing your home computer or assisting family and friends with technical issues.
Yes, it is a free, quick Assist unattended remote access software. The free plan of Zoho Assist - unattended remote access solution lets you initiate remote support and unattended access sessions. With the free plan, organizations can configure upto 5 devices for unattended access.