A workforce password manager built for
Essential Eight
The Essential Eight, developed by the Australian government, is a strategic cybersecurity framework designed to help organizations defend against a wide range of cyber threats.
WPM aligns seamlessly with these security priorities by offering a robust, encrypted vault for storing credentials, enforcing strict role-based access controls, and automating secure, regular backups. Even in the event of a breach, sensitive data remains protected—helping businesses stay resilient, compliant, and confidently secure in a constantly evolving threat landscape.
LGPD
The Lei Geral de Proteção de Dados (LGPD) is Brazil's data protection law, designed to regulate the collection, use, and storage of personal data.
WPM supports compliance with the LGPD by securing sensitive information, enforcing strict access controls, implementing multi-factor authentication, and providing comprehensive audit trails, ensuring both data protection and transparency.
DORA
The European Union has introduced the Digital Operational Resilience Act (DORA), which establishes a higher standard for how financial institutions handle and endure disruptions related to ICT. At its core, DORA is about building stronger, smarter defenses against digital risks—ensuring that even in the face of cyberattacks or system failures, financial services remain secure and operational.
WPM empowers institutions to rise to this challenge with confidence. By consolidating sensitive data under one secure platform, enforcing advanced authentication measures, and continuously monitoring for emerging threats—including those lurking on the dark web—WPM helps safeguard critical systems and information. Every action is logged with detailed audit trails, offering full visibility into who accessed what and when. This not only simplifies compliance efforts but also significantly reduces the chances of unauthorized activities slipping through the cracks. With WPM, meeting DORA requirements becomes a seamless part of a stronger digital resilience strategy.
NIS2
The Network and Information Security Directive 2 (NIS2) sets a new benchmark for cybersecurity across the EU, mandating that operators of critical infrastructure and essential services take proactive steps to safeguard their digital environments. At its core, NIS2 is about more than just compliance—it's about building resilience against evolving cyber threats.
WPM empowers organizations to align with NIS2 requirements effortlessly. With built-in support for real-time monitoring, SIEM integration, and a dynamic security dashboard, WPM offers complete visibility into your password health and system vulnerabilities. These intelligent features help you detect threats early, respond faster, and maintain the high level of protection NIS2 demands. From identifying weak credentials to surfacing actionable insights, WPM transforms security from a checkbox into a strategic advantage.
RBI Master Directions
The Reserve Bank of India (RBI) Master Directions lay the foundation for a secure and resilient financial ecosystem in the country. These comprehensive guidelines are crafted to help regulated entities strengthen their cybersecurity posture and manage digital risks effectively. More than just a regulatory mandate, the Master Directions represent a forward-thinking approach to safeguarding financial data and infrastructure in an era of rising cyber threats and regulatory scrutiny.
WPM plays a pivotal role in meeting these requirements. By providing granular control over user access to critical systems and sensitive data, WPM ensures that only the right individuals have the right access at the right time. It enforces the principle of least privilege, continuously monitors user activities, and flags anomalies in real time—creating a secure environment that deters insider threats and unauthorized actions.
SEBI CSCRF
The Cyber Security and Cyber Resilience Framework (CSCRF) introduced by the Securities and Exchange Board of India (SEBI) sets a strong foundation for financial market intermediaries to build secure and resilient systems. In alignment with these guidelines, WPM empowers organizations to stay compliant while enhancing their overall security posture.
By offering a centralized way to define user roles and access privileges, WPM ensures that sensitive systems are accessible only to authorized individuals. Its intelligent access control capabilities help prevent privilege misuse by granting users only what they need—nothing more. Every action within the system is meticulously logged, with comprehensive activity reports and audit trials enabling financial institutions to monitor user behavior, detect anomalies early, and take proactive measures before threats escalate.
Explore how Zoho Vault can help with SEBI CSCRF compliance.RMiT
Introduced in 2020 by Bank Negara Malaysia, the Risk Management in Technology (RMiT) policy outlines a comprehensive framework to help financial institutions strengthen their cybersecurity posture. With a focus on risk governance, security controls, incident response, and operational resilience, RMiT ensures that organizations are better equipped to safeguard critical systems and sensitive data.
WPM plays a key role in supporting RMiT compliance by enforcing strict access controls that limit user privileges based on specific roles. This minimizes the chances of unauthorized access while enabling continuous oversight through real-time monitoring and regular audits. By aligning with RMiT's expectations for account management, WPM helps institutions build a more secure, resilient, and compliant IT environment.
Essential Cybersecurity Controls
The National Cybersecurity Authority (NCA) of Saudi Arabia introduced the Essential Cybersecurity Controls to guide organizations on their journey toward secure digital transformation. These controls are rooted in a deep analysis of global cybersecurity standards, real-world incident patterns, and the collective insights of various organizations. Tailored specifically for Saudi Arabia, they define the foundational security practices every organization must follow to safeguard their digital assets.
At the core of this initiative lies a simple truth—every digital advancement depends on the security of sensitive information. In today's landscape, a single compromised password can open the door to devastating consequences. That's why strong, proactive credential management is no longer optional. A well-rounded workforce management strategy not only protects confidential data but also tracks how it's accessed and by whom—pinpointing threats before they escalate.
Cyber Essentials
Cyber Essentials, a UK government-backed certification, helps organizations strengthen their defenses against common cyber threats by encouraging the implementation of essential security controls. One crucial aspect of meeting these standards is securing access to sensitive systems and data—and that's where WPM comes in.
WPM simplifies the path to certification by securing sensitive credentials behind layers of encryption, enforcing strict access policies, and keeping a close watch on user activity. It helps organizations minimize risk, prevent unauthorized access, and maintain tighter control over who gets to do what. More than just a tool, WPM reflects a proactive approach to cybersecurity—empowering businesses to not only meet compliance standards but to build a culture of digital trust and accountability.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) sets important standards in the United States for protecting confidential patient health information. At its core, HIPAA ensures that electronic Protected Health Information (ePHI) remains confidential, secure, and accessible only to authorized personnel.
WPM supports healthcare organizations in meeting these strict requirements by enabling secure, role-based access to sensitive data. From the moment ePHI is created to its final archival, WPM ensures it remains shielded through advanced security controls and real-time monitoring. This comprehensive approach not only helps healthcare providers maintain compliance but also reinforces trust by safeguarding patient privacy every step of the way.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is essential for protecting payment card information and preventing fraud. With WPM, achieving PCI DSS compliance becomes easier.
WPM strengthens your organization's security by tightly controlling access to sensitive cardholder data, managing credentials with advanced encryption, and maintaining detailed audit trails. Its built-in reporting and monitoring tools provide clear visibility into who accessed what and when—helping you stay compliant, reduce risk, and build trust with every transaction.
CIS Controls
The CIS Controls, created by the Center for Internet Security, are a widely accepted set of 18 top practices aimed at assisting organizations in enhancing their cybersecurity defenses. These controls span critical areas such as asset management, access control, and continuous monitoring—providing a roadmap to reduce vulnerabilities and defend against the most prevalent cyber threats.
WPM plays a critical role in supporting several of the CIS Controls. By securing and streamlining how access is granted across sensitive data, WPM reinforces the principle of least privilege. It minimizes the risk of unauthorized access by ensuring that only the authorized users have the right level of access at the right time. Additionally, WPM provides deep visibility into account usage, helping teams monitor user activity and respond swiftly to anomalies.
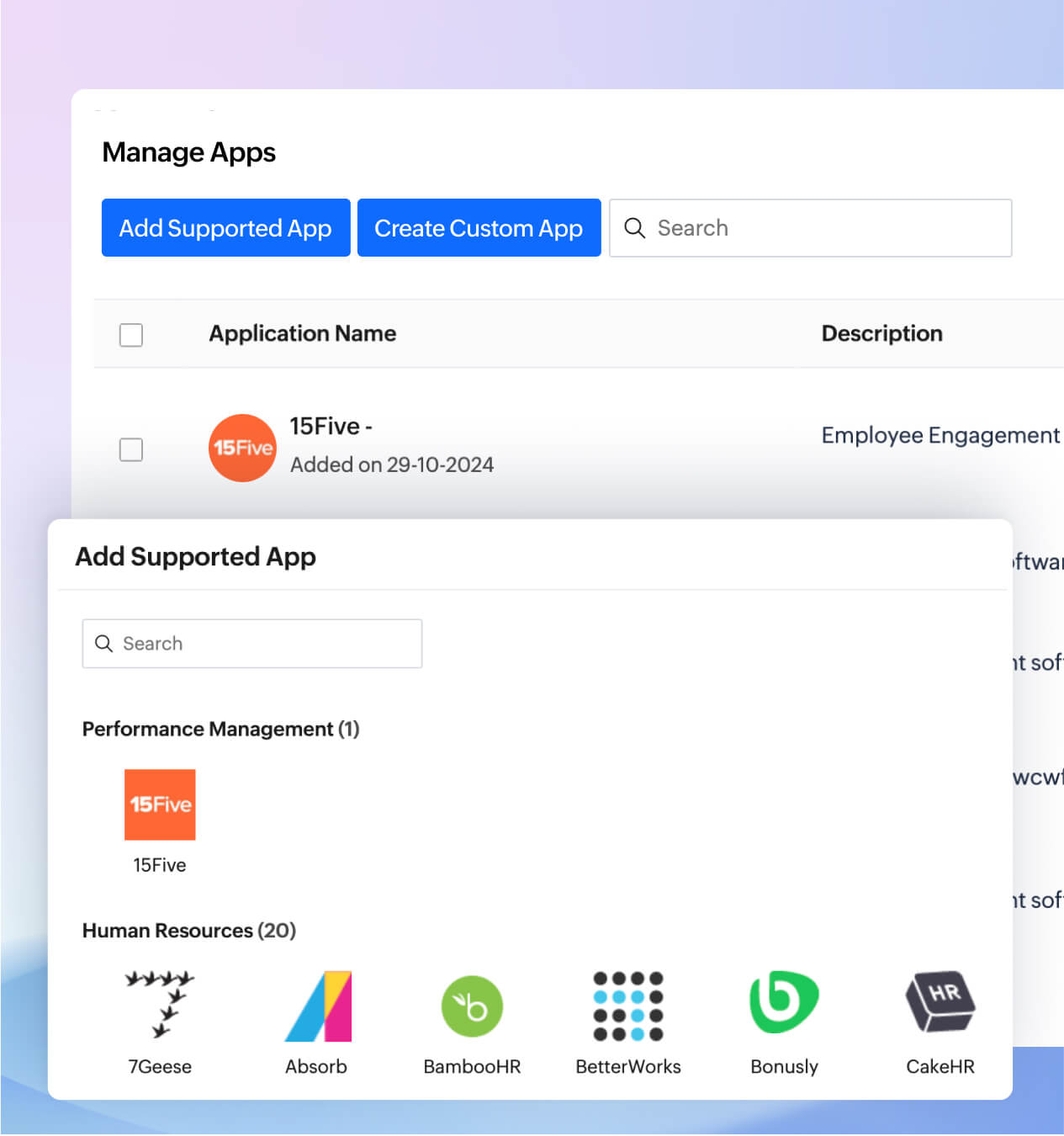
Key Zoho Vault features that support your compliance goals
- Unified IAM and SSO
- Role-based access control
- Request-release workflow
- Password policy
- Dark web monitoring
- Audits and reports
Unified identity management and passwordless access
Zoho Vault brings together workforce password management and single sign-on (SSO) under one secure roof. With passwordless SSO and passkeys, your team can log in once and instantly access all business apps and websites—no juggling passwords, no friction. This seamless experience boosts productivity while reinforcing your security posture.
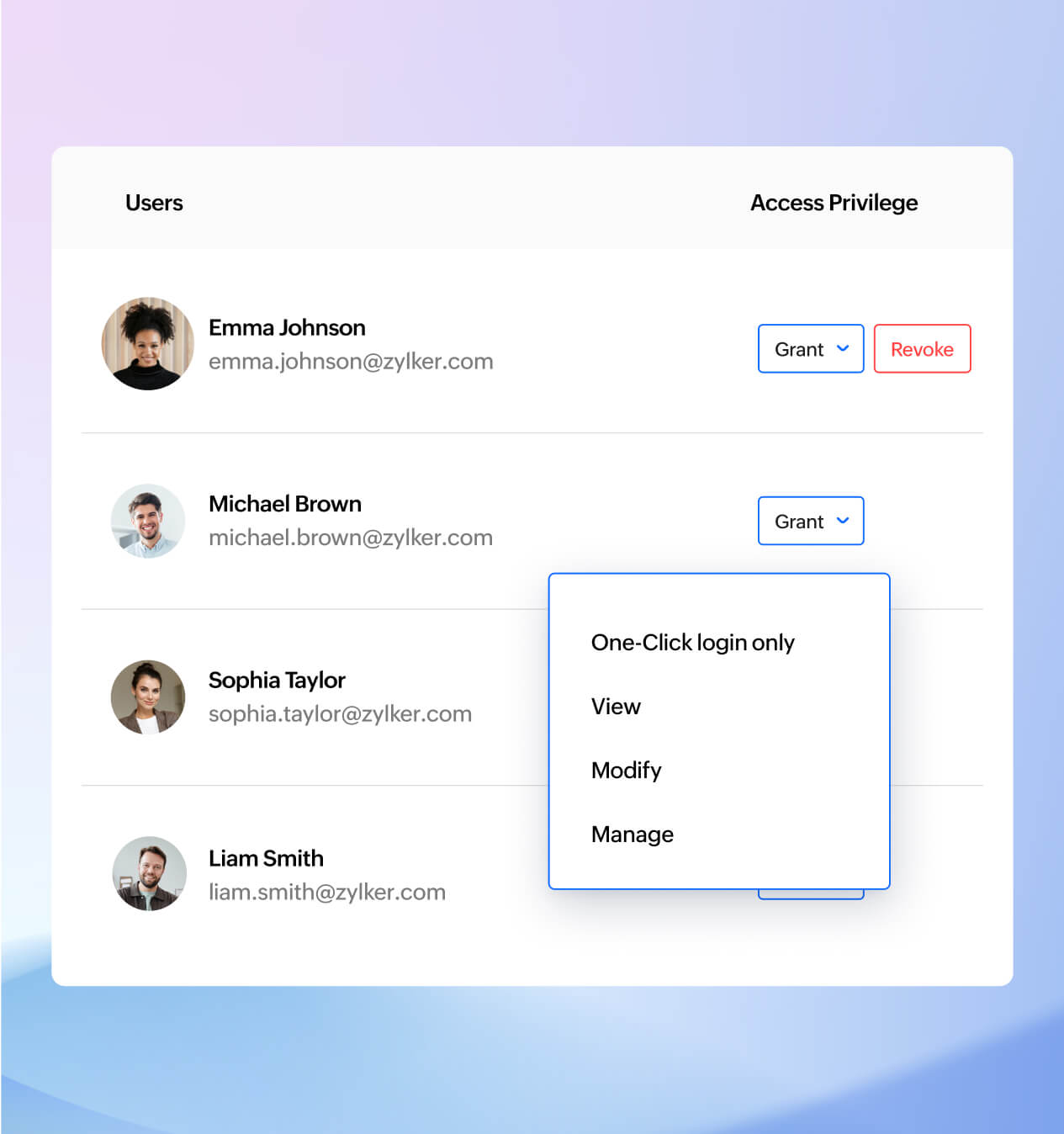
Enforce least privilege by design
Compliance begins with access control. Zoho Vault helps you implement the principle of least privilege using built-in roles and granular permissions. This means employees only get access to the tools they need—nothing more, nothing less—reducing exposure to potential threats and ensuring tighter compliance across departments.
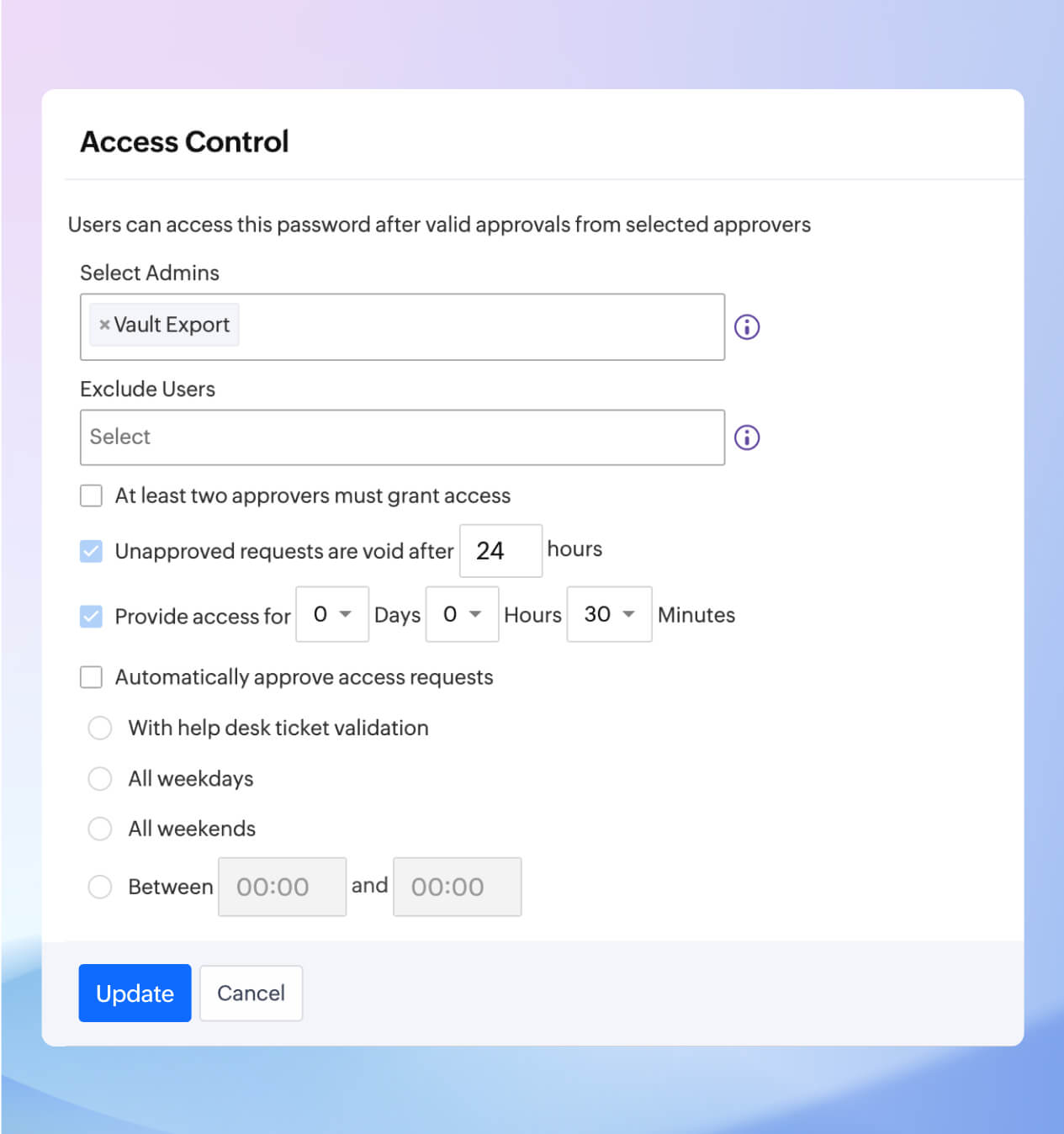
Need-based access with request-release workflows
Not every user needs full access, all the time. Zoho Vault's request-release mechanism lets admins approve temporary access to sensitive credentials only when necessary—based on a valid reason or ticket. This controlled provisioning supports access-related requirements across many compliance standards.
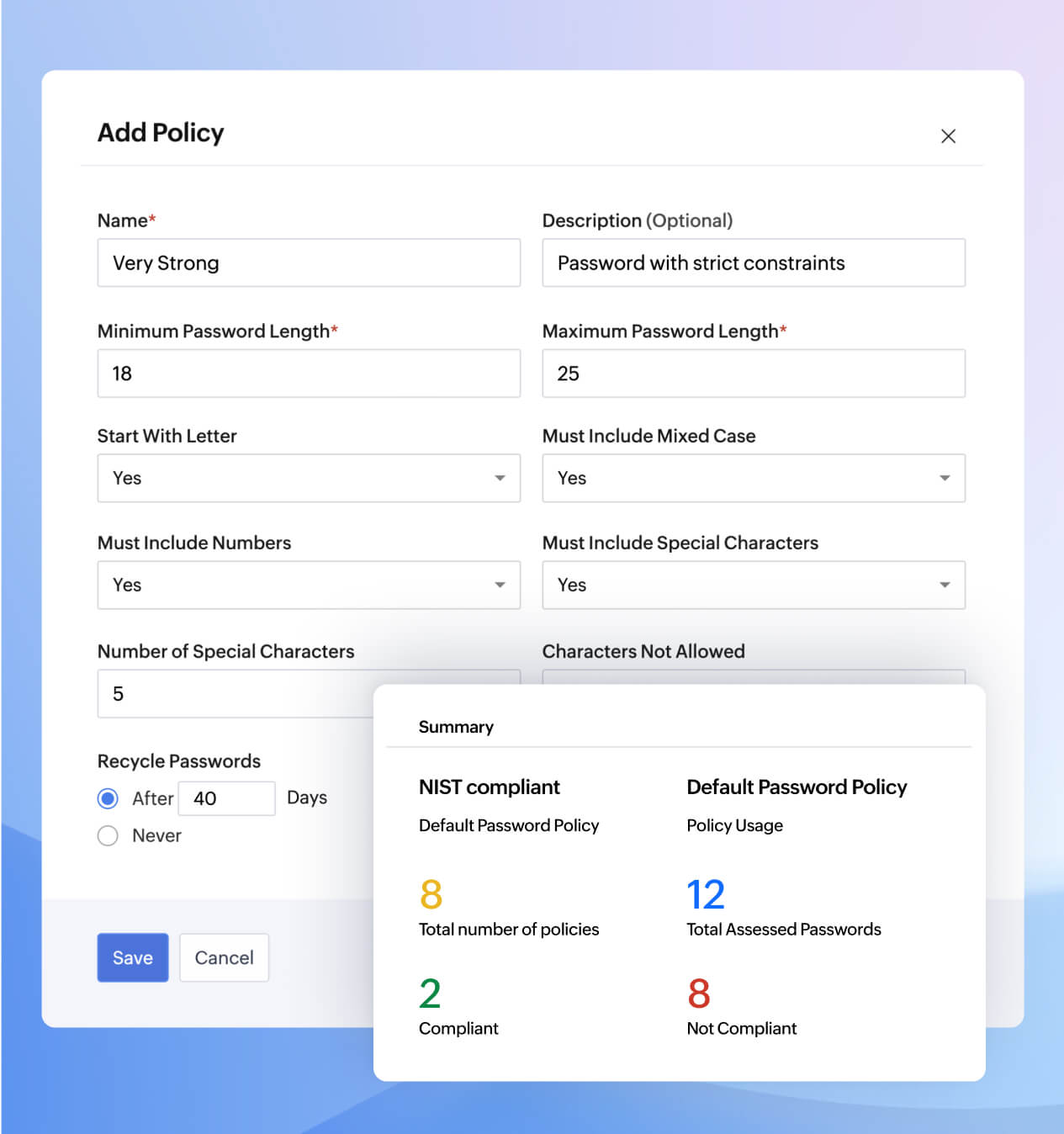
Custom password policies that meet compliance standards
Define and enforce strong password rules from day one. With Zoho Vault, you can set organization-wide policies for password complexity, length, and uniqueness. The built-in password generator ensures that compliant credentials are easy to create and manage. Set custom expiration dates, track password hygiene, and generate compliance reports to stay audit-ready.
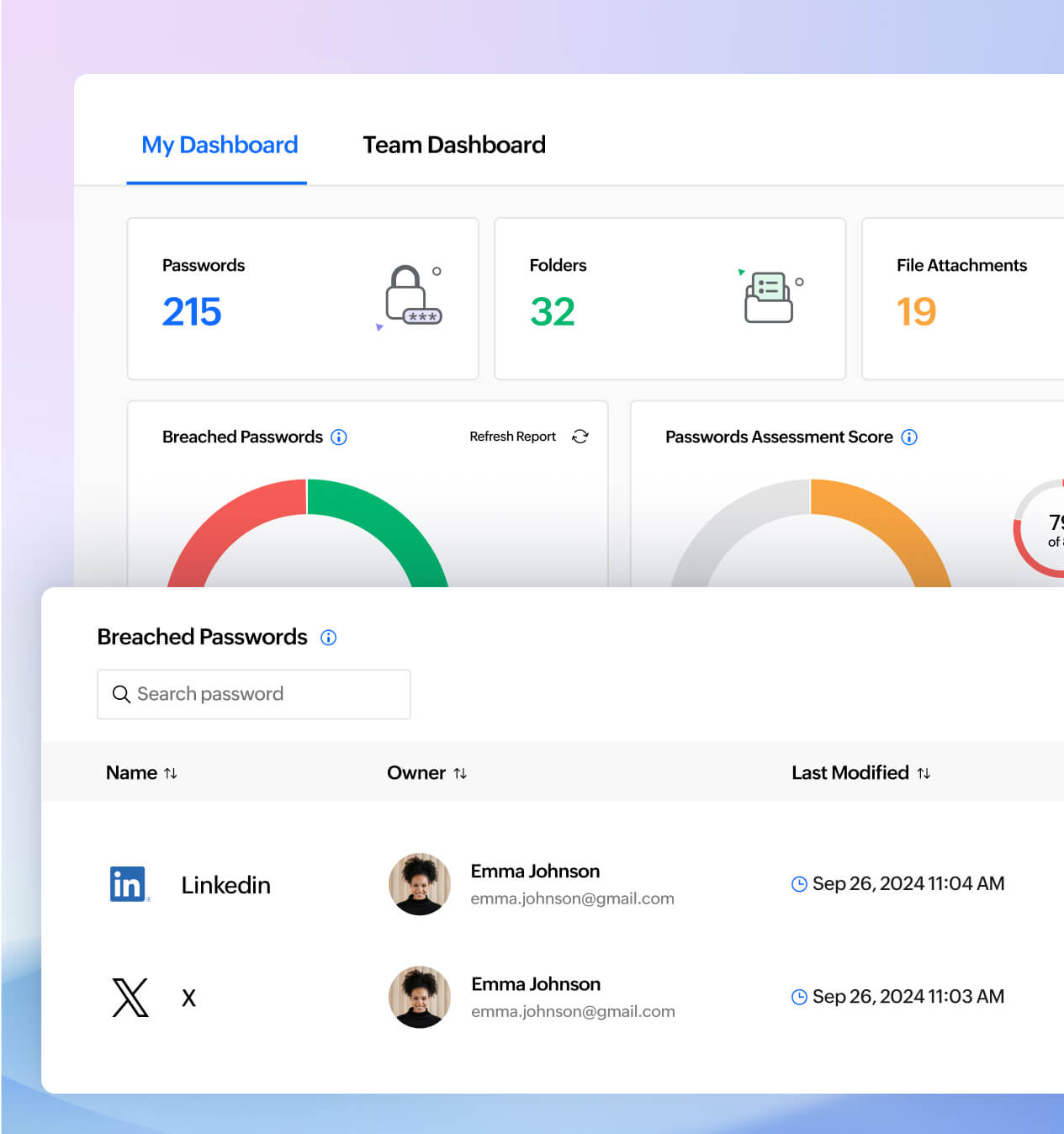
Security insights and dark web monitoring
Your security status at a glance—Zoho Vault's security dashboard gives you real-time visibility into weak or reused passwords and potential risks. Enable dark web monitoring to detect compromised credentials early. Need extra control? Implement approval-based access, or set up emergency access for trusted contacts when time is of the essence.
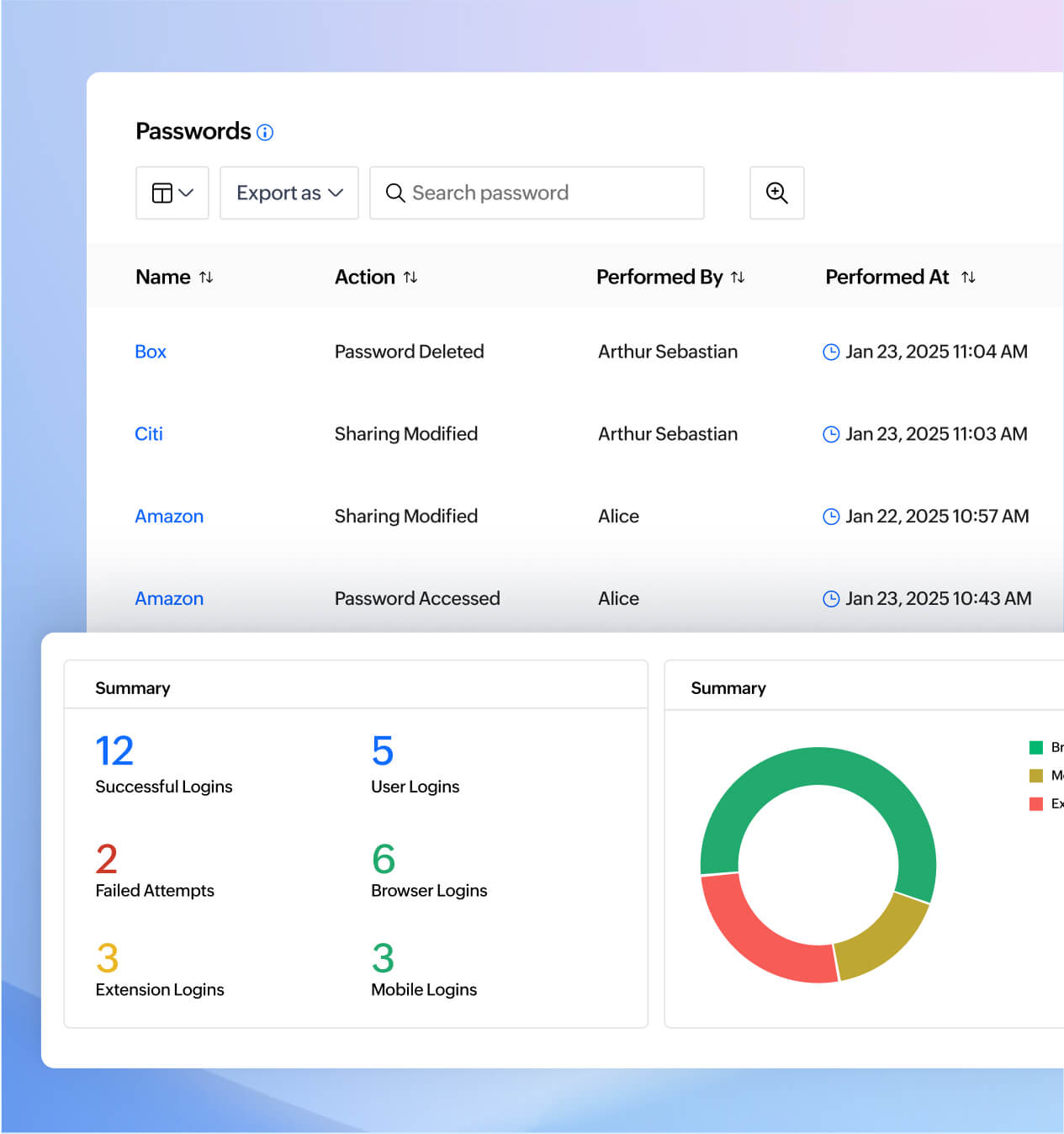
Real-time audits and compliance-ready reports
Never miss a beat with Zoho Vault's real-time audit logs and visual activity reports. Admins can track everything—from login attempts to password changes—and receive instant alerts for critical actions. This transparent oversight helps you stay compliant, informed, and always in control.
Why does cybersecurity compliance matter?
Protect sensitive data.
Zoho Vault gives you a smarter way to sign in, combining SSO, passkeys, and password management into one powerful platform. One login, endless access-because security should be simple.
Build customer trust.
Reinforce your password security with Zoho Vault's real-time dashboard. Monitor your passwords' strengths and usage trends, while dark web alerts ensure compromised credentials never catch you off guard. From workflow requests to emergency access, Zoho Vault has your back, 24/7.
Mitigate legal risks.
Never miss a beat when it comes to security and compliance. Our realtime audit logs and comprehensive reports keep you informed about every access attempt, password change, and admin action-so you can track, review, and ace every audit with confidence.
Get cyber insurance.
Qualify faster for cyber insurance and lower your premiums with strong workforce password management.
Compliance-ready, so you can be too
Zoho Vault meets leading privacy and compliance standards, giving you the confidence to meet yours. Our industry-recognized certifications reflect our unwavering commitment to security and data protection.






Frequently Asked Questions
Cyber insurance is a type of coverage that helps businesses protect themselves from the financial fallout of cyberattacks and data breaches. Whether it's ransomware, malware, DDoS attacks, or other forms of cybercrime, cyber insurance—also known as cyber risk or cybersecurity insurance—offers tailored protection to help organizations manage and recover from these digital threats.
Zoho Vault is a workforce password manager that securely stores and manages passwords, credit cards, certificates, secrets, and other sensitive data. It offers advanced security features like passwordless single sign-on (SSO), multi-factor authentication, and passkeys management for secure access to your applications. Zoho Vault integrates with directory services for centralized access control and simplified user management. It also supports API and CLI access for easy integration with existing IT systems and automated security workflows.
Yes, Zoho Vault offers a free plan with unlimited storage, security dashboard, built-in password and passphrase generator, and more. Learn more about our plans and features on our pricing page.
Beyond its workforce password manager (Zoho Vault), Zoho offers a comprehensive suite of security solutions designed to protect various aspects of your digital operations. These include Ulaa, a privacy-first secure browser that emphasizes data protection and blocks web tracking; Zoho Directory, an Identity and Access Management (IAM) platform for centralized user, app, device, and network management; Zoho Mail, providing secure and encrypted email collaboration; Zoho OneAuth, a robust multi-factor authentication (MFA) solution for enhanced login security; and ManageEngine's Log360, a cloud SIEM (Security Information and Event Management) solution that helps detect, investigate, and neutralize security threats.
For technical assistance, contact us at support@zohovault.com. Our support team is here to help!
