- HOME
- All Topics
- Collaboration and Digital Workplace
- Migrating from Microsoft 365 to Zoho Workplace: Directory coexistence patterns and flows
Migrating from Microsoft 365 to Zoho Workplace: Directory coexistence patterns and flows
- Published : September 24, 2025
- Last Updated : November 18, 2025
- 775 Views
- 6 Min Read
A directory is the control plane for identity across mail, chat, files, meetings, and admin. It's the source of truth for users and groups and, when used as the IdP, it authenticates users and enforces sign-in policy. It also provisions accounts and maps groups to app roles so the right access appears on day one and is removed on exit.
Directory essentials for workplace integration
Single source of truth
Establishes the source of truth for users, attributes, and lifecycle; decides account existence for mail, chat, files, and meetings; sets primary identifiers (login, email, aliases); is the upstream for group membership; sets default ownership; 'disable' or 'delete' here blocks access everywhere.
Identity Provider (IdP)
Authenticates users via SAML or OIDC; enforces MFA and conditional access with optional device posture; controls sign-in success, session lifetime, and where users can log in; issues token and group claims that apps use for authorization; supports step-up for sensitive actions.
Provisioning (SCIM)
Automates, creates, updates, and deletes users and groups in apps; delivers day-one access and licenses; syncs roles and profile updates; handles leavers by removing memberships, revoking access, and transferring ownership of mail, files, and meetings.
Groups and authorization
Map directory groups to app roles; drive distribution lists and shared mailboxes or delegate rights; set channel membership in chat; assign file and folder roles; control room booking and delegate scheduling; target intranet audiences; scope delegated admin access.
Directory data and lookup (Global Address List)
Maintains a single, accurate company address book so people and resources are easy to find. Enables email auto-complete, people search (name, title, department), org chart viewing, selecting delegates for calendars and mailboxes, and picking rooms or equipment when booking.
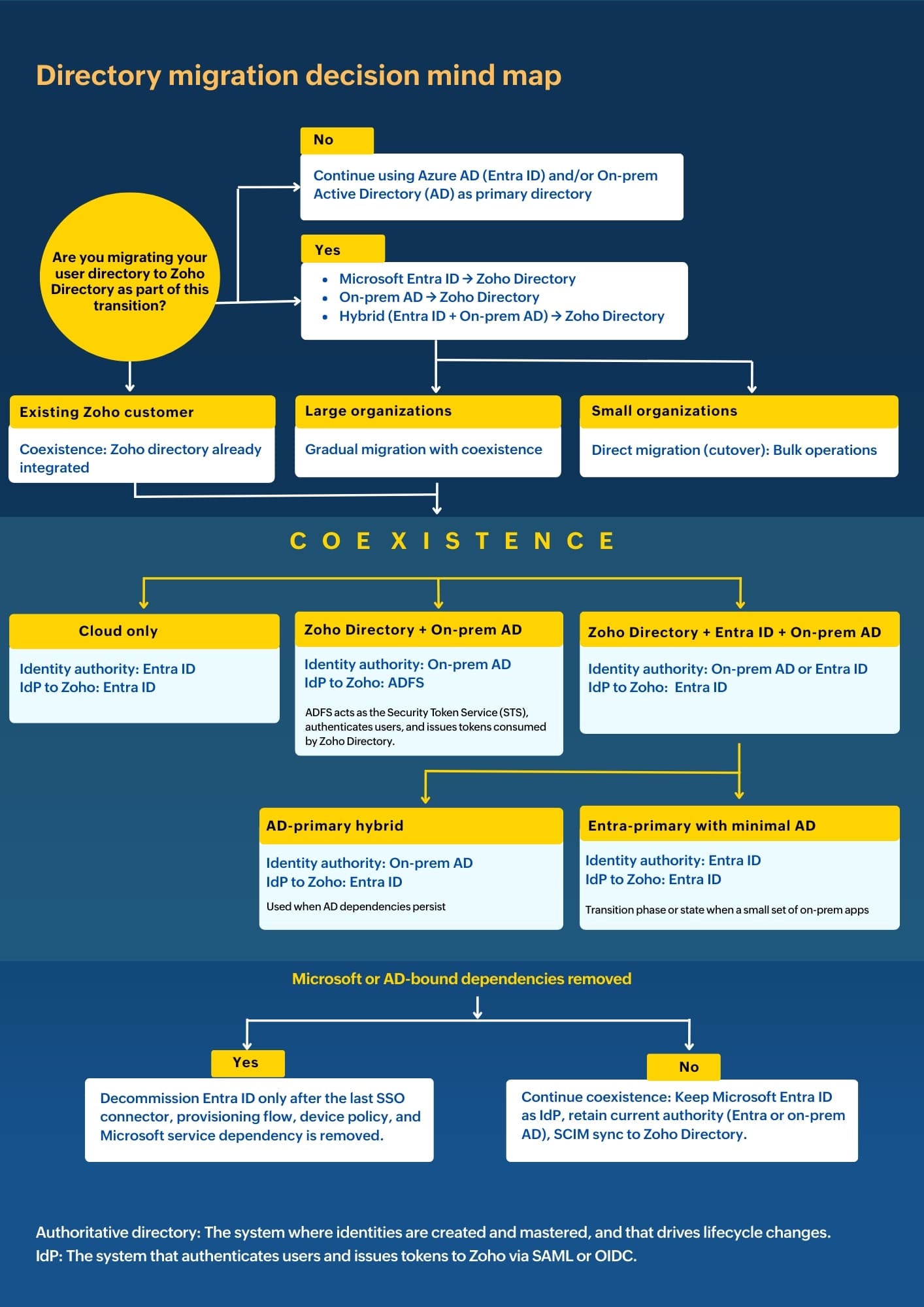
Azure Entra ID in coexistence: SCIM provisioning + SAML SSO to Zoho Directory
Use Microsoft Entra ID as the single source of truth and IdP. Zoho Directory acts as the service provider and SCIM target, so users, groups, and access flow from Entra while sign-in happens with Entra credentials.
Admin one-time setup
Zoho Directory
- SSO: Upload Entra signing certificate (or import metadata).
- Copy ACS URL and Entity ID for Entra; verify they match.
- Generate SCIM token for Entra.
Microsoft Entra ID
- Add the Zoho enterprise app.
- SCIM:Paste Zoho SCIM endpoint and token, set Provisioning to Automatic, assign users and groups.
- SAML: Enter ACS URL and Entity ID from Zoho, download the signing certificate.
- Authority: Admin creates/updates/disables in Entra. That is the single source of truth.
- Provisioning: Entra SCIM pushes Users, Groups, Memberships to Zoho Directory (create/update/delete). One way Entra → Zoho. No writeback.
- Authentication: User opens a Zoho app → SSO starts at Zoho Directory → Zoho Directory sends AuthnRequest to Entra → Entra returns signed assertion → Zoho Directory issues the Zoho session.
- Authorization: Provisioned groups map to app roles/scopes in Zoho; apps may also read claims from the assertion for fine-grained rules.
- Offboarding: Disable in Entra blocks SSO immediately; SCIM soon removes memberships and access in Zoho.
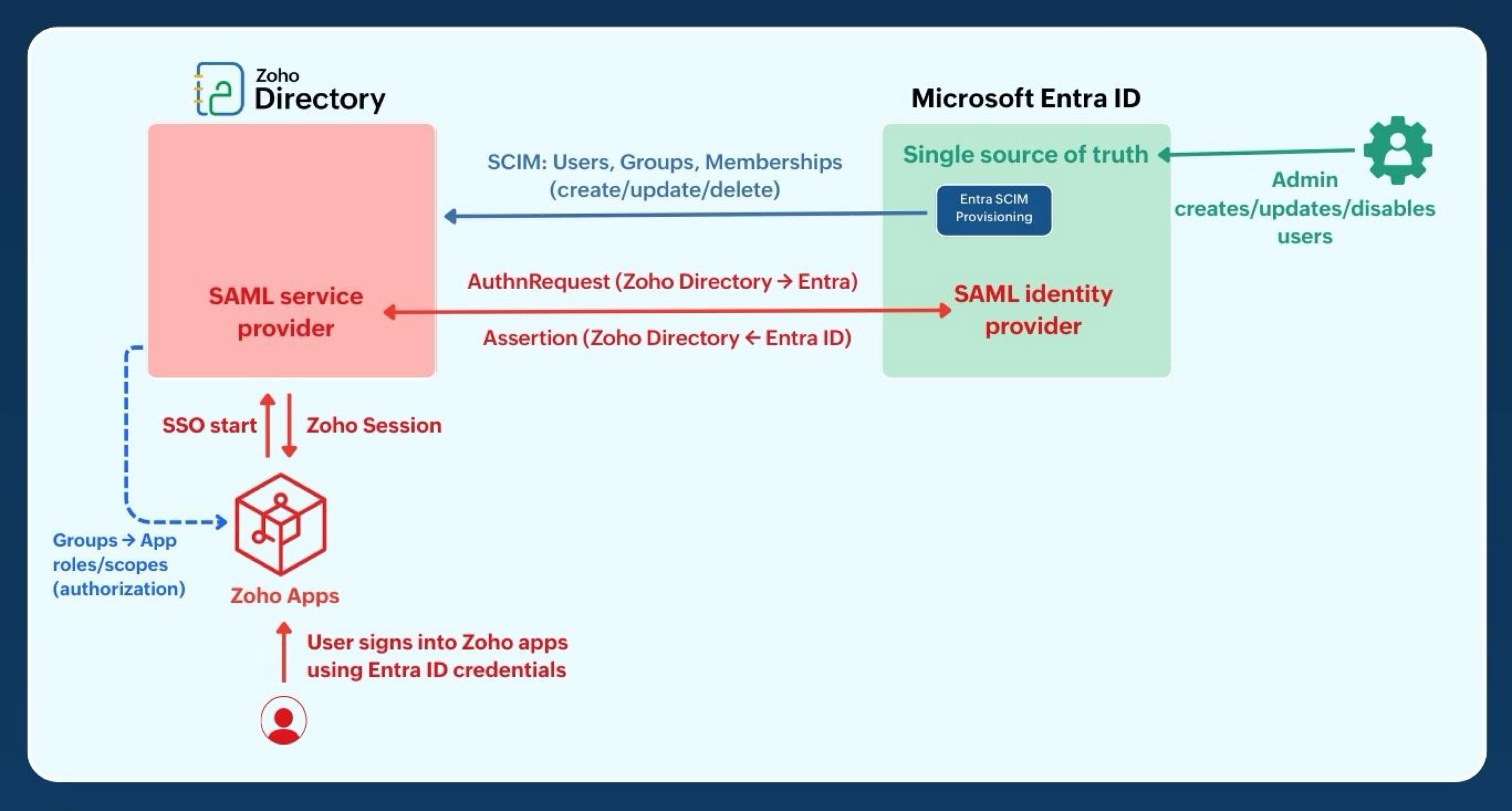
On-premise AD in coexistence: AD Sync provisioning + ADFS SAML SSO to Zoho Directory
Use on-premise Active Directory as the single source of truth and ADFS as the IdP. Zoho Directory acts as the service provider and AD Sync target, so users, groups, and access flow from AD while sign-in happens with ADFS credentials.
Admin one-time setup
Zoho Directory
- SSO: Upload the ADFS token signing certificate (or import metadata).
- Copy ACS URL and Entity ID for ADFS and verify they match.
- Create an AD Sync connection and generate the sync token.
Microsoft Active Directory/ADFS
- AD Sync: Install the Zoho AD Sync tool on a domain-joined server, sign in with the Zoho token, map sAMAccountName, mail, displayName, department, memberOf, and enable continuous sync.
- ADFS: Add Zoho Directory as a Relying Party Trust, import metadata or enter Entity ID and ACS URL, set NameID (UPN or email), add issuance rules, and confirm the token signing certificate is active.
- Authority: Create, update, or disable users and groups in Active Directory. AD remains the single source of truth.
- Provisioning: The AD Sync tool pushes Users, Groups, and Memberships to Zoho Directory (create/update/delete).One way AD → Zoho. No writeback. Near real time.
- Authentication: User opens a Zoho app → SSO starts at Zoho Directory → Zoho Directory sends SAML AuthnRequest to ADFS → ADFS authenticates against AD and returns a signed assertion → Zoho Directory issues the Zoho session used by apps.
- Authorization: Provisioned groups in Zoho Directory map to app roles/scopes. You can also emit group/role claims from ADFS for finer rules if needed.
- Offboarding: Disable in AD blocks ADFS sign-in immediately; AD Sync removes memberships and access in Zoho.
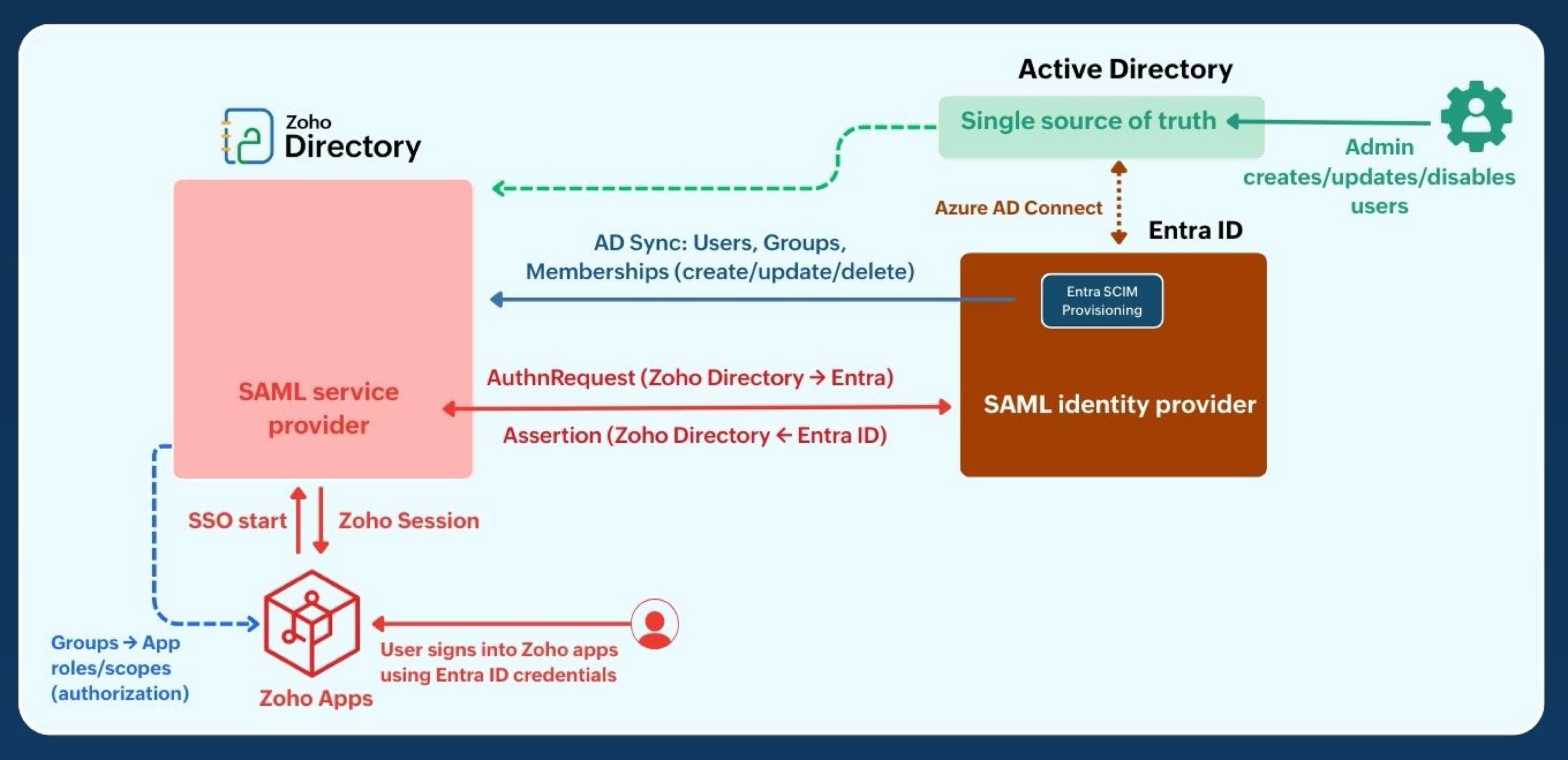
Hybrid coexistence (AD + Entra): parallel directory sync and SSO to Zoho Directory
If you run both on-premise Active Directory and Microsoft Entra ID, you can provision users into Zoho Directory and enable SSO via either path below. AD stays the authority; the difference is which system is the IdP and which one pushes lifecycle changes to Zoho.
Admin one-time setup
Zoho Directory
- SSO: Upload Entra’s token-signing certificate (or import metadata).
- Copy ACS URL and Entity ID for Entra and verify they match.
- Create an AD Sync connection and generate the sync token.
Microsoft Active Directory
- Install the Zoho AD Sync tool on a domain-joined server, sign in with the Zoho token.
- Map attributes (sAMAccountName, mail, displayName, department, memberOf) and enable continuous sync.
Microsoft Entra ID
- Ensure Azure AD Connect is syncing AD to Entra.
- In Entra, add the Zoho app, set ACS URL and Entity ID from Zoho, download the signing certificate, assign users and groups.
- Authority: AD is the single source of truth. All lifecycle changes happen in AD.
- Provisioning: AD Sync → Zoho Directory, one way. Users, groups, and memberships (create, update, delete). No writeback.
- Authentication: App → Zoho Directory → Entra (AuthnRequest) → signed assertion → Zoho session.
- Authorization: Zoho groups map to app roles and scopes. Apps can also read Entra claims.
- Offboarding: Disable in AD. Entra sign-in is blocked via AD Connect; AD Sync removes Zoho access shortly after.
Identity control plan for Zoho Workplace cutover
- Establish one authoritative directory (AD or Entra ID) and one IdP (ADFS or Entra ID). Perform all create, update, and disable actions only in the authoritative directory.
- Use exactly one provisioning path into Zoho Directory (Entra SCIM or AD Sync). Provision one way; do not enable writeback.
- Treat Zoho Directory as the SP. The IdP issues the token; Zoho Directory issues the Zoho session.
- Drive authorization via provisioned groups → app roles/scopes. Avoid local, per-app role drift.
- Time-box coexistence. Keep it only while Microsoft/AD dependencies exist. Operate to defined exit criteria and a documented rollback.
Recommended default in hybrid - If AD is authority and Entra is IdP, prefer Entra SCIM → Zoho Directory (with AD Connect). This unifies assignment for SSO and lifecycle, reduces on-premise components, and simplifies operations.
- Use AD Sync → Zoho Directory only if you must keep ADFS or you are not using Entra for cloud assignment.
Exit criteria to end coexistence - No Zoho app authentications observed at ADFS/Entra for a defined cooling period.
- All required users and groups are provisioned in Zoho Directory and access is enforced correctly.
- Disabling at the source immediately blocks SSO; provisioning removes roles within the agreed SLA.
- Device and access controls are enforceable without AD/Entra.
- Decommission plan, rollback, and break-glass IdP are documented and tested.
When full migration to Zoho Directory is sensible - Minimal reliance on AD/Entra features or on-premise LDAP/Kerberos apps.
- Majority of work is in Zoho apps or SaaS that can federate with Zoho Directory.
Desire to consolidate identity admin, reduce agents/federation, and lower platform cost.
This article is co-authored by Sandeep Kotla and Vignesh S.
Sandeep is an accomplished inbound marketer at Zoho Corporation, specializing in digital workplace strategies, digital transformation initiatives, and enhancing employee experiences. Previously, he handled analyst relations and corporate marketing for Manage Engine (a division of Zoho Corp) and its suite of IT management products. He currently spends most of his time re-imagining and writing about how work gets done in large organizations, reading numerous newsletters, and Marie Kondo-ing his inbox.
Vignesh works as a Marketing Analyst at Zoho Corporation, specializing in content initiatives and digital workplace strategies. He's a passionate creator with a penchant for marketing and growth. In his free time, you can see him shuffling between books, movies, music, sports, and traveling, not necessarily in the same order.



