- HOME
- Threat types
- Malware 101—the most common malware threats via email
Malware 101—the most common malware threats via email
- Last Updated : March 6, 2026
- 416 Views
- 10 Min Read
Every business runs on three important factors—trustworthy employees, data, and systems. It's a combination of all these factors that makes a business work without any hiccups. A common hazard to all three of these factors is cyber threats. When human-targeted cyber threats strike, employees tend to fall prey to the attack, endangering sensitive organizational data and the systems used by the organization.
While this holds true for all types of cyberattacks, it’s especially relevant when it comes to malware threats. Cybercriminals are increasingly leveraging different types of malware to wreak havoc across organizations for financial and other means. While most email security systems and anti-virus software deployed on users' machines capture certain malware attacks, newer types of malware keep coming up and traditional security systems are struggling to keep up with these threats.
In this article, we'll explore what malware really is, the different types of malware and their propagation mechanisms, and the mitigation measures of malware infection in your systems.

What is malware?
Malware refers to any malicious software that's propagated with the intention to destroy, corrupt, or deny access to sensitive data on a system. In these attacks, the user whose system is being infected most likely has no idea about the infection. Cybercriminals plan their attack in such a way that their file or URL containing malware evades the security filters set up by organizations and silently makes its way to the users' systems to infect them without detection.
Malware threats can spread through various means, such as SMS, USB drives, QR code scans, and other common means. However, email continues to be a common mode of delivery for malware-infected files and URLs. In fact, according to Verizon's 2024 DBIR, 94% of malware is delivered through emails. Most cybercriminals target business email addresses for malware delivery because it opens a gateway to infect multiple devices across a network and to extract money or sensitive data from employees.
How does malware spread?
Malware spreads through an organization's systems in five crucial steps.
1. Creating the malware
In the first step, the threat actor decides the intention of their attack. This could range from anything such as stealing passwords, locking users out of their systems, silently monitoring sensitive data, making a copy of files, and more. Based on their intent, they create software that can help achieve their goal. In some cases, if the threat actors aren’t technologically advanced, they even make use of ransomware-as-a-service (RaaS) models. In these models, certain cybercriminals sell malicious software or code to threat actors, for use in other attacks.
2. Dissipating the malware
Once the malware is created, the threat actor decides how to deliver the malware to their targets. In this step, they choose whether the malware will be used to target businesses or individuals. Typically with low-effort attacks, threat actors don't target specific people and deliver the malware at large. But with high-effort malware, they target organizations for a better return.
They distribute the malware through emails, instant messages, USB drives, or QR codes that lead to the malicious software. In a business-context, email is the most-used form of malware delivery.
3. User engagement
Malware can be delivered in different ways. In some cases, the threat actor delivers it in the form of files. Certain file extensions, such as .exe, .dll, .js, or sometimes even .zip or .rar files, could be harboring malware. When the recipient downloads the attachment, the malware is downloaded onto the system.
In some cases, the threat actor also embeds or hosts the malware file on a website and sends the website link in the email. Redirection to the link leads to a file download, or in some cases, the user clicks on a genuine download link in the website, unaware of its malicious nature.
4. System or file infection
Depending on the type and intention of the malware, infection of certain files or the entire system begins. In some cases, the malware simply monitors all of the activities that take place on the system. In some cases, the user is locked out of their system; other times, the keystrokes are recorded; and some display malicious, unwarranted ads on the system. While some types are more of an inconvenience, some cause serious damage, such as corruption or deletion of sensitive data.
5. Spread of infection
If the threat actor has picked a business as their target, it's highly probable that they're aiming to infect other users on the same network. Certain malware types spread through the network, affecting files and systems at a large scale. If the threat actor is trying to infect without causing any disruption, the users won’t be able to identify that they've been infected. This gives the threat actor leverage to gather data over a large period and use it as part of a bigger attack or even sell it on the dark web.
Types of malware
Malware is a widely prevalent cyber threat. The AV-TEST institute registers 450,000 malware programs every day. All of these are malicious software that causes disruption in some form. But the mechanism of spread and the activity performed by each type of malware varies across. Let's discuss the most common types and how they function.
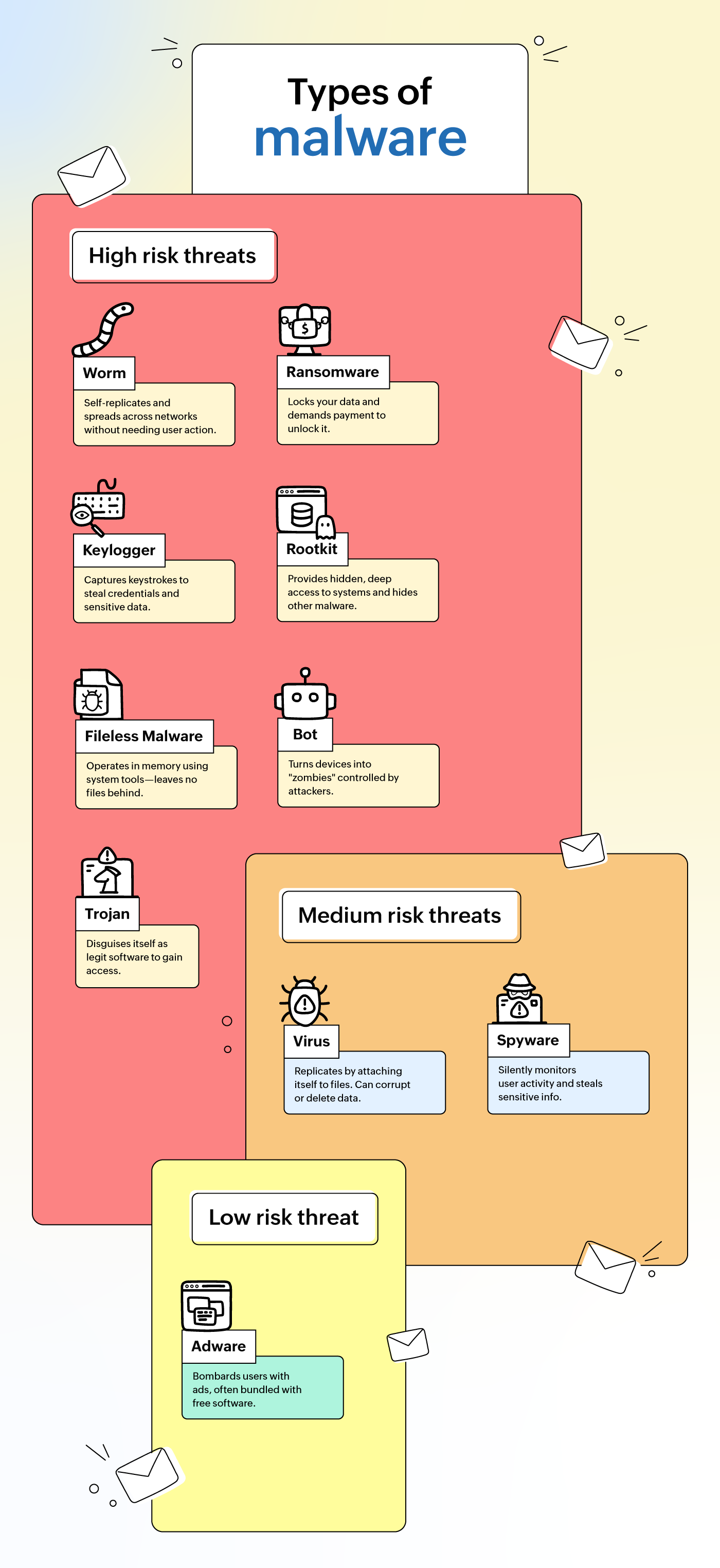
Viruses
Viruses are the most common types of malware. Viruses are typically snippets of code that attach themselves to a legitimate program or application. Whenever the original program runs, the virus is executed too, corrupting, deleting, or modifying sensitive information. Usually, viruses need some sort of human interaction to be activated. In cases where the virus is shared through email, downloading the attachment with the virus has to be done manually; only if the program that's run is opened or executed will the virus be activated and cause damage.
Mitigation tip: Keep all of your software up to date and download any security fixes or patches as soon as you're notified of the update. Even if an infected attachment is downloaded by mistake, this reduces the number of entry points the virus can infect, alleviating the damage caused.
Ransomware
Ransomware refers to a type of malware in which the threat actor locks down the system they've infected and demands a ransom to unlock it. Cybercriminals design the malware code in such a way that the entire system or the sensitive files are encrypted and the owner is locked out. They display a ransom note that the user is expected to pay in cryptocurrency, assuring the target that the decryption key will be shared once the ransom is paid. Ransomware is one of the most financially devastating malware types due to the payment involved, the operational disruption, and the negative impact it causes businesses.
Some cybercriminals also provide ransomware-as-a-service to improve their revenue streams and enable less-proficient threat actors with toolkits. Popular RaaS actors include REvil, Hive, LockBit, among many others.
Mitigation tip: Ransomware attackers often follow a double or multiple extortion approach. Even after the ransom is paid, they threaten to expose the data or demand additional payment. Ensure you backup and archive your data regularly and retrieve data from your archives in case an attacker strikes.
Bots
Bots are a set of interconnected computers, often on the same network, that are infected with malware and controlled by a hacker. Because multiple devices are under the attacker’s control, they have the power to perform operations on a larger scale, such as sending out spam, mining cryptocurrency, or launching DDoS attacks. The combined processing power of the infected systems contributes to these attacks, making them extremely dangerous. While bots can also be used for legitimate purposes, they're widely used by threat actors.
An infamous example is the Mirai botnet, which infected thousands of IoT devices and launched massive DDoS attacks, temporarily taking down major websites like Twitter and Netflix.
Mitigation tip: Use network monitoring to detect abnormal traffic patterns in your systems and network. Detecting anomalies before they spread can prevent one compromised device from endangering your entire network.
Worms
Worms are a type of self-replicating malware that spreads across networks and systems by exploiting any open ports or connections. Unlike viruses, they don't need user interaction to be activated. This makes them a dangerous kind of malware because, by simply connecting to the infected network, users’ machines can be infected as well. Worms are used as part of ransomware attacks, DDoS attacks, or to steal sensitive data. Due to the rapidly spreading nature of this malware, it can bring down entire infrastructures.
The WannaCry ransomware attack affected Windows computers by exploiting a vulnerability without any users having to interact with it. The attack combined the use of worms and ransomware.
Mitigation tip: Segment your network and use strong access controls. Isolating systems and networks can stop worms from propagating across your entire environment. This way, the impact of such attacks can be minimized, and preventive measures can be taken once the initial attack has been identified.
Spyware
As the name suggests, spyware is a type of malware that secretly spies on all the activities that are performed on a system. These applications or scripts silently stay active on the machine and monitor the data being entered and the programs that are run; they can also read the documents that are present. This is useful for hackers who are interested in stealing critical information such as credit card numbers, sensitive documents, account credentials, financial statements, and more.
This is one of the less dangerous types of malware because it doesn't cause direct harm. However, in an organizational context, it can lead to data leaks and breaches.
Mitigation tip: Use behavior-based detection tools that flag unusual data access or exfiltration attempts. Monitor systems for slowness or increased usage of storage space than usual.
Adware
Adware refers to pop-up advertisements that are displayed on users' screens without any sign-up or prompt. These are mostly displayed on web browsers, but there are also instances in which the ads are displayed in offline Windows machines. While this type of malware is considered the least harmful, some variations of adware may cause damage. These ads work in the background, collecting information about user behavior. This data could prove useful in social engineering attacks. In some cases, the ads may also redirect the users to malicious websites.
Mitigation tip: Adware is mostly installed through free software installations. When you download free software, adware may be downloaded alongside without your knowledge. When you download software, always check the files that are downloaded and deselect any files that seem unnecessary.
Trojans
Trojans are malware disguised as legitimate applications or software. When you download an attachment that seems legitimate—most commonly, a link to a software application or a security patch—the malicious file is downloaded with it. Trojan viruses are named after the Greek Trojan Horse because it seems innocuous at first, but masks its malicious nature. Once downloaded, Trojans are activated in the system, taking control of it. They create backdoors in the infected device, stealing credentials or other data, and even granting remote access to the hacker.
Mitigation tip: Trojans are most commonly circulated through pirated versions of legitimate software. Steer clear of such software, and ensure that you only download such applications from the original developer's website. Even if a website looks legitimate, it could spread malicious software.
Keyloggers
Keyloggers are software that capture the keystrokes entered by a user on their system. Keyloggers are also used in legitimate cases, such as in a business context or as a form of parental control, but these tools are being increasingly exploited by hackers for their benefit. Most keyloggers capture the information entered by the system's owner and share it to a hacker who's operating from a remote site. These tools can monitor passwords, financial information, social security numbers, credit card numbers, and other such sensitive information.
Mitigation tip: Most anti-virus solutions come equipped with keylogger detection tools that can help identify and remove these software. Use multifactor authentication to ensure that threat actors are denied access to your accounts, even if they identify your account passwords.
Rootkits
Rootkits are software packages that run at the root level of an operating system, making changes at the base. This masks the ability of software to detect other malware or keyloggers that are running in the machine. Because these packages have privileges to perform administrator-level operations, they alter the machine in the way an admin would while remaining unidentified. This gives them access to add or remove users, install applications, and remove software that could help identify anomalies. This makes them one of the most dangerous kinds of malware.
Mitigation tip: Rootkits are often tough to detect and uninstall. In most cases, the best practice if a rootkit is identified is to wipe the machine completely and reboot it. Additionally, it helps to use trusted boot mechanisms and system integrity checks.
Fileless malware
Fileless malware is malicious code that resides in a system's RAM instead of working based on a file download. These files are mostly dispersed through phishing websites or emails containing malicious links. Because it's present in the system's memory, it manipulates legitimate files to carry out desired actions instead of acting by itself. Because there's no file to identify and remove, fileless malware attacks are difficult to detect and eradicate. This malware uses various exploitation techniques to modify its native tools to serve the desired purpose.
Mitigation tip: Typical anti-virus solutions often fail to detect fileless malware as they work based on signatures. Implement an Endpoint Detection and Response (EDR) solution that tracks script execution, memory usage, and unusual PowerShell or WMI activity.
Wrapping up
Malware takes many forms, from stealthy spyware and destructive ransomware to elusive fileless threats, but the aim is often to exploit, disrupt, or control. As cybercriminals become more innovative, businesses and individuals must stay ahead of the curve. This can be attained by adopting layered security measures, staying informed about evolving threats, and building a culture of cyber awareness within your organization.
By combining smart technology, employee training, and vigilant monitoring, you can significantly reduce risk and build a resilient defense against today’s most dangerous cyber threats.


