Accounts receivable process template
Here's the blueprint we created in Orchestly for a generic accounts receivable process. Yours can be much simpler or more complex, depending on your needs.
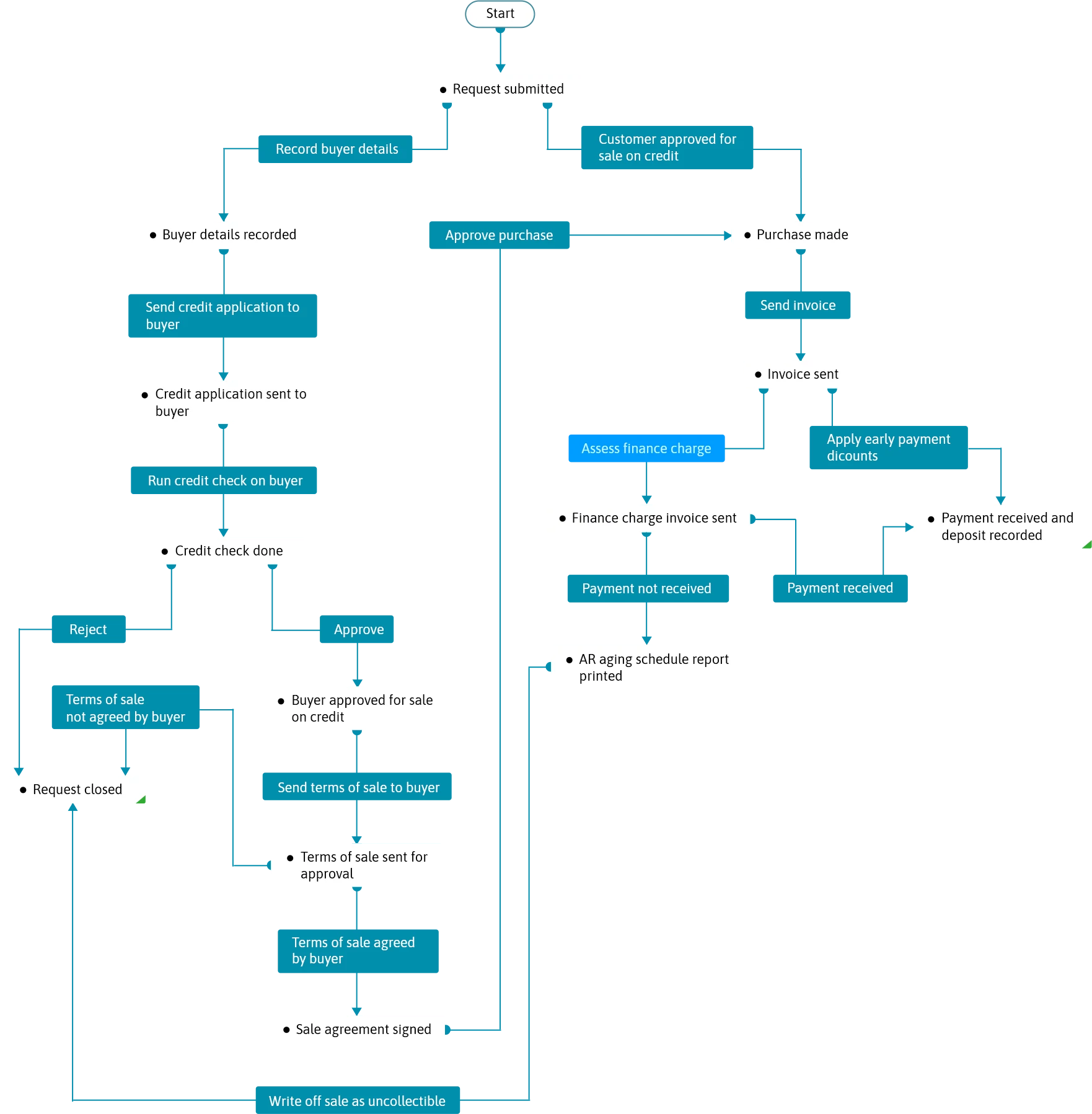
In this blueprint, if it's a first-time buyer, routine credit risk assessments are done, and the terms of sale are agreed upon before selling anything to the buyer. In the case of buyers who've been buying regularly on credit, the credit risk assessment report on record is verified and the process moves forward.
Once the purchase is done, an invoice is sent to the buyer. Any early payment discounts are applied, and the payment is received and recorded if it's made on time.
In the case of late payments, late-fee charges are applied (if any) and a new invoice is sent to the buyer. And if the payment is still not made, even after multiple collection attempts, the AR aging schedule report is analyzed—at which point either collection attempts are continued, or the sale is written off as uncollectible.
Benefits of managing your accounts receivable process with Orchestly
- 01
Streamline the process
Automate approvals and checks based on condition or time, instead of relying on employees to do them manually.
- 02
Get things done on time
Cut down on communication chaos by letting employees know exactly what they should be doing, and when.
- 03
Access contextual information
Access relevant, unified information from your other accounting tools by connecting to them through APIs.
- 04
Ensure on-time payments
Prevent overdue payment and nonpayment by automating reminder emails for collection attempts with SLAs.
- 05
Centralize control
Manage all accounts receivable from one place. Know the exact status of every account, and ensure a steady flow of cash.
- 06
Optimize the process
Identify reasons for payment delays with both built-in and tailor-made reports, so you can focus on finding a solution to the problems.
- 07
Protect sensitive data
Let employees access information only when and if they need them. Encrypt important data and protect personally identifiable information.