Security Reports
Data security is critical to any organization that uses email as their business communication. To prevent your organization's data from being misused, Security reports play an important role. Zoho Mail provides various reports related to security, allowing you to monitor the phishing attempts made against your organization's users and ensure take proactive steps to ensure each user's data is safe and secure.
Login Reports
The login reports section provides an overview of the following reports:
Login activity Report
The Login Activity report provides comprehensive insights into user access within your system, such as who accessed the system, what actions were performed, when these actions occurred, and where the access originated from. This allows Administrators to track individual user activities and detect any suspicious or unauthorized access attempts. To view the Login activity reports, follow these steps:
- Log in to Zoho Mail Admin Console and click Reports on the left pane.
- Navigate to Security and select Login activity.
- Below are the details available in the report :
- Name/Email - Name and email address of the user.
- Service name - Name of the service accessed by the user.
- Device info - Displays information about the device used, such as Windows, Chrome, or Mac.
- IP address - The IP address from which the login was performed.
- Location - Displays the location from where the user has logged in.
- Access type - Specifies the type of access from which the login was performed.
- Click the Date filter to select the time period for which you want to see the report.
- Select the filter option to filter reports based on the Access type (Web/Mobile) or Operation type (Sign in/Sign out).
- Use the Search option to quickly find the details by entering the name/ email of the user.
- To download the report as a CSV file to your local device for analysis or share it via Zoho Cliq, click the Share option in the top pane. You can also encrypt the file with a password to prevent unauthorized access to you data. Learn more about sharing reports.
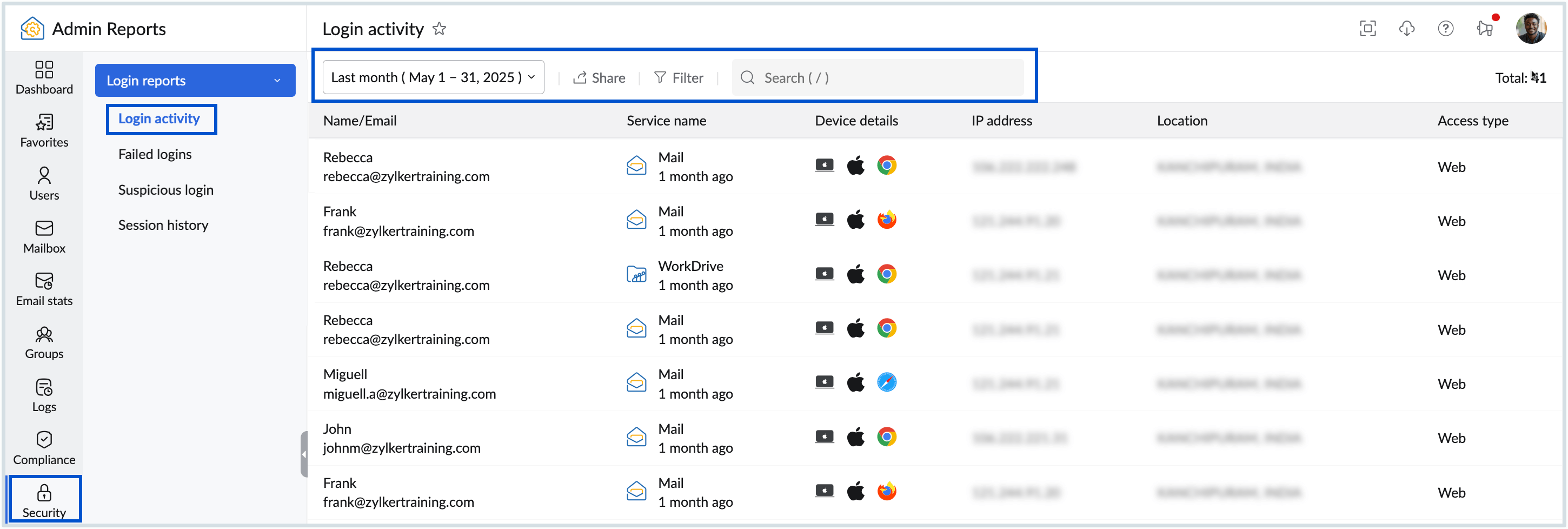
- By clicking on any user, you can view detailed information about their login activity, including the login time, logout time, login URL, IP address, login location, device, operating system, browser, and recent login history.
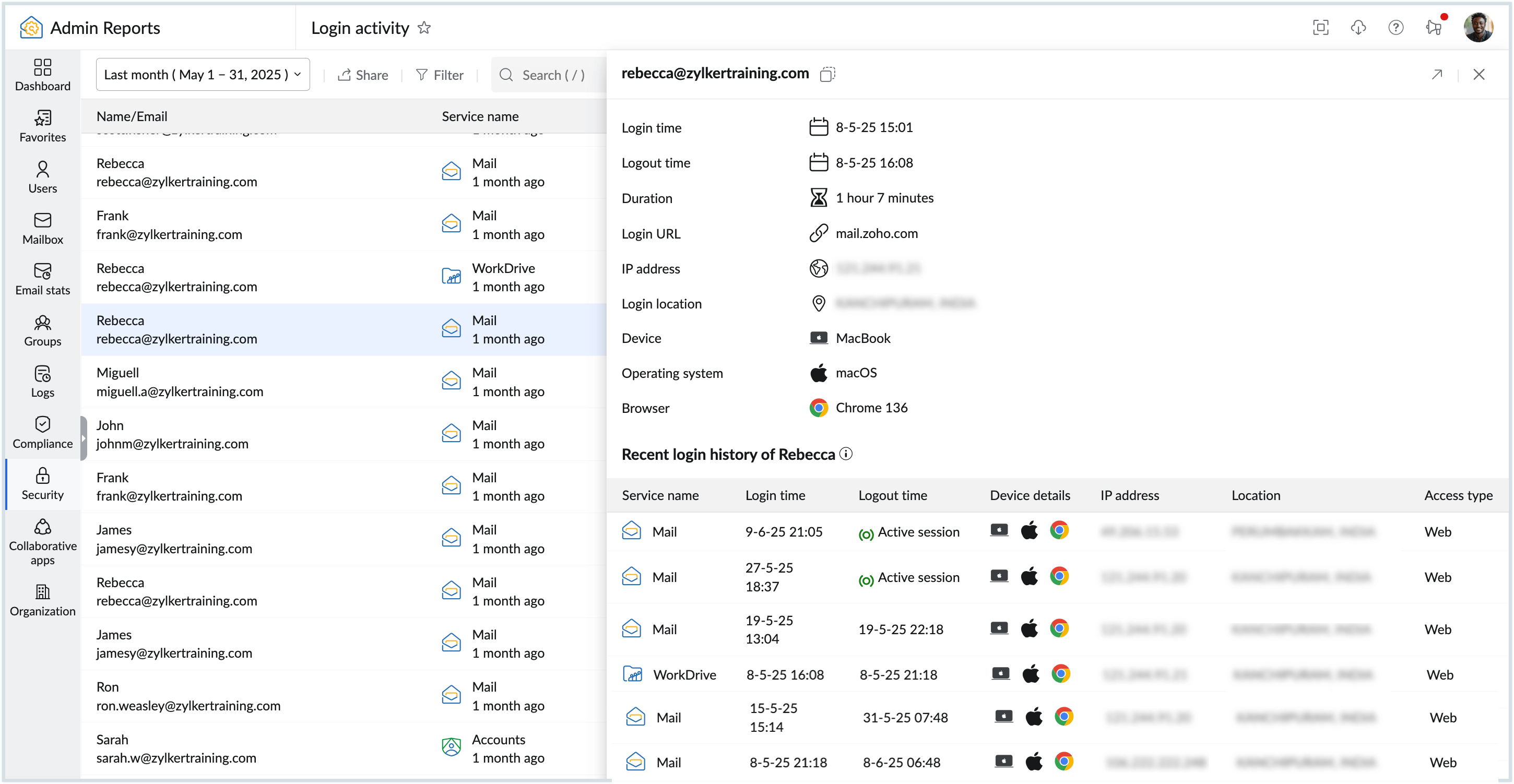
Failed login Report
The Failed Login Reports display a detailed list of each failed login attempt made by the organization's users. This helps administrators safeguard the organization from potential security threats, enabling proactive measures to prevent data breaches and unauthorized access. To access Failed login reports:
- Log in toZoho Mail Admin Console and click Reports on the left pane.
- Navigate to Security and select Failed login report.
- Below are the details available in the report :
- Name/Email - Name and email address of the user.
- Login time - Displays the exact time and date of the login attempt.
- Device info - Displays information about the device used, such as Windows, Chrome, or Mac.
- IP address - The IP address from which the login was performed.
- Failure reason - Displays the reason why the login was marked as failed login.
- Login URL - Displays the login url used during the login attempt.
- Click the Date filter to select the time period for which you want to see the report.
- To download the report as a CSV file to your local device for analysis or share it via Zoho Cliq, click the Share option in the top pane. You can also encrypt the file with a password to prevent unauthorized access to your data. Learn more about sharing reports.
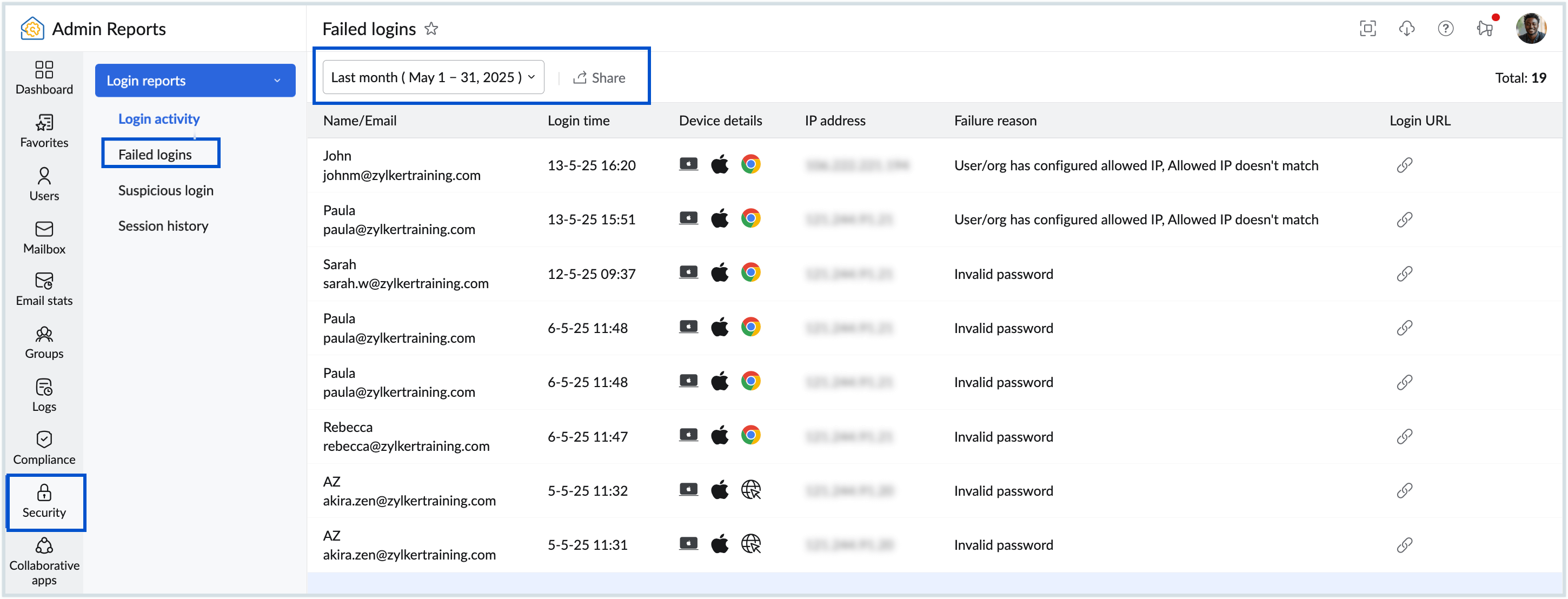
Suspicious Login Report
Based on a user's previous login behaviour, Zoho Mail alerts if there is any suspicious login activity. Administrators can view the list of suspicious login activities based on the selected duration. To view the suspicious logins, follow these steps:
- Log in to Zoho Mail Admin Console and select Reports on the left pane.
- Navigate to Security and select Suspicious login.
- Select the desired date range from the drop-down. Below are the details available in the report :
- Name/Email - Name and email address of the user.
- Login time - Mentions the time that the user logged in to the account.
- Location - Displays the location from where the user has logged in.
- Login source - Mentions the source of login (protocol types), such as POP, IMAP, WEB, SMTP_IN, and SMTP_OUT.
- Client IP address - The IP address from which the login was performed.
- Use the Seach bar to filter the report based on the email address, client IP address, location or login source. The suspicious login report appears for the selected filter criteria.
- To download the report as a CSV file to your local device for analysis or share it via Zoho Cliq or Zoho Workdrive, click the Share option in the top pane. You can also encrypt the file with a password to prevent unauthorized access to your data. Learn more about sharing reports.
Session History
The session history report displays the number of live sessions for the selected user. The report displays the Client IP address and Session start time. Navigate to Session history under the Security section in Admin Reports. Enter a user name in the Search Bar to view the corresponding session history. You can expand or add the chart to your dashboard based on your preference. 
To download the chart to your local device for analysis or share it, click the Share button. Learn more about sharing reports.
Threat Activity
Threat activity report lists the malicious activities targeted against your organization's users, which can end up as a threat to your organization's data security. This report aids you to identify and understand cyberattack attempts and address them in a timely manner.
Note:
- The Threat Activity report will be rolled out in a phased manner and be available only for organizations that use one of our paid plans.
- If you want the option enabled for your organization, please reach out to us at support@zohomail.com.
The Threat activity report in Zoho Mail Admin Reports is grouped into different categories based on the nature of the threat. The table given below provides an overview of each threat type:
Accessing Threat Activity Reports
Follow these steps to view the threat activity reports:
- Log in to Zoho Mail Admin Console and select Reports on the left pane.
- Navigate to Security and select Alert center. The threat activity report appears with the following details:
- Threat type - Mentions the threat type. Refer to the table given above for details about each threat type.
- Description - Provides a brief description of the threat. For example, if a user marks an email as phishing, the description displays "Email was marked as phishing by the user username@domain.com".
- Details - Contents of the Details column differ based on the threat type. Some of the details are - From email address (spam marking), count of emails (anomaly), Location (login activity), etc.
- Time - Displays the date and time at which the threat was detected.
- Select the preset duration or a custom date range for which you want to view the report. By default, All will be selected.
- Use the Search bar and Filter options to narrow down the report based on your requirement.
- To download the report as a CSV file to your local device for analysis or share it, click the Share option in the top pane. You can also encrypt the file with a password to prevent unauthorized access to your data. Learn more about sharing reports.
- If required, click Filter on the top menu, hover over a threat and choose the sub-category from the available list:
- User reported - As spam, As spam (bulk) and As phishing
- Mail moved - As attachment in spam and As mail is spam
- Spam actions - URL clicked, Attachment downloaded and User replied
- Mail rejected - Virus attachment and Blocked attachment
- Spam detected - Marked as spam
- Anomaly - By incoming and By outgoing mail
- Login - Suspicious login and Failed login
The threat activity report appears for the selected filter criteria.



