Email Protection
Zoho eProtect has a spam control system that provides multiple options to customize the email protection settings to suit your organization's needs. You can customize the actions to be taken on unverified emails, set up allowed or blocked lists, define the quarantine controls for outgoing and incoming emails, and so much more.
Anti-Spam in Zoho eProtect
Spam Processing
The Spam Processing settings get configured when you set up your organization in Zoho eProtect. However, you can customize the settings that best suit your organization's requirements at any point of time from the Email Protection section. Follow these steps to modify the Spam processing settings:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Anti-spam and select Spam Processing. The configuration you chose while setting up your organization appears.
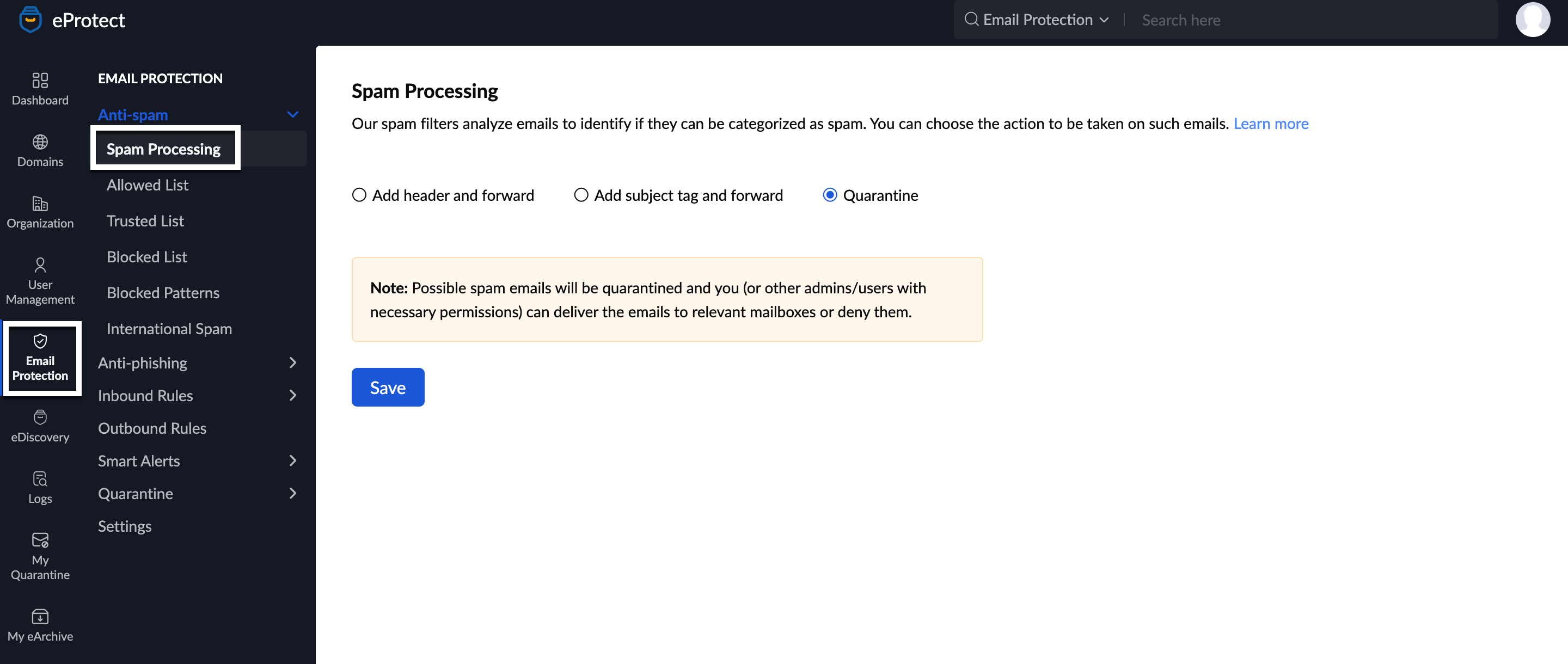
- Select the type of spam processing that you want to set up:
- Add header and forward - eProtect updates the email header with the content provided by admins and then forwards the email to the intended recipient.
- Add subject tag and forward - eProtect appends the subject with the content provided by admins and then forwards the email to the intended recipient.
- Quarantine - eProtect quarantines the email which can then be scrutinized by admins.
- If you choose Add header and forward, follow these sub-steps:
- Enter a Header Name and Header Value.
- Click the + icon to add multiple headers as per your requirements.
- To delete a header row, click the delete icon.
- If you select Add subject tag and forward, enter a Subject Tag.
- If you choose Quarantine, eProtect quarantines the email. Admins can moderate these emails from the Quarantine section.
- Click Save.
You have successfully configured the Spam Processing settings.
Spam Control Lists
Zoho eProtect lets you set up spam control lists specific to your organization. You can configure allowed lists, trusted lists, and blocked lists. To each of these lists, you can add domains, email addresses, IP addresses, etc.
Allowed List
As an administrator, if you do not want certain emails to be marked as spam, you can add the domain and specific email addresses to the Allowed List. However, in case there is an SPF failure, and there is no action set for SPF failure, the emails from allowed list domains or addresses will not be marked as 'Not Spam'. In the case of SPF failure, the email may be a possible spoofed email, and hence the email address/domain added to the allowed list will not be effective in that case.
Follow these instructions to configure Allowed List:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Anti-spam and select Allowed List. The Emails tab appears with a list of email addresses that you have already configured.
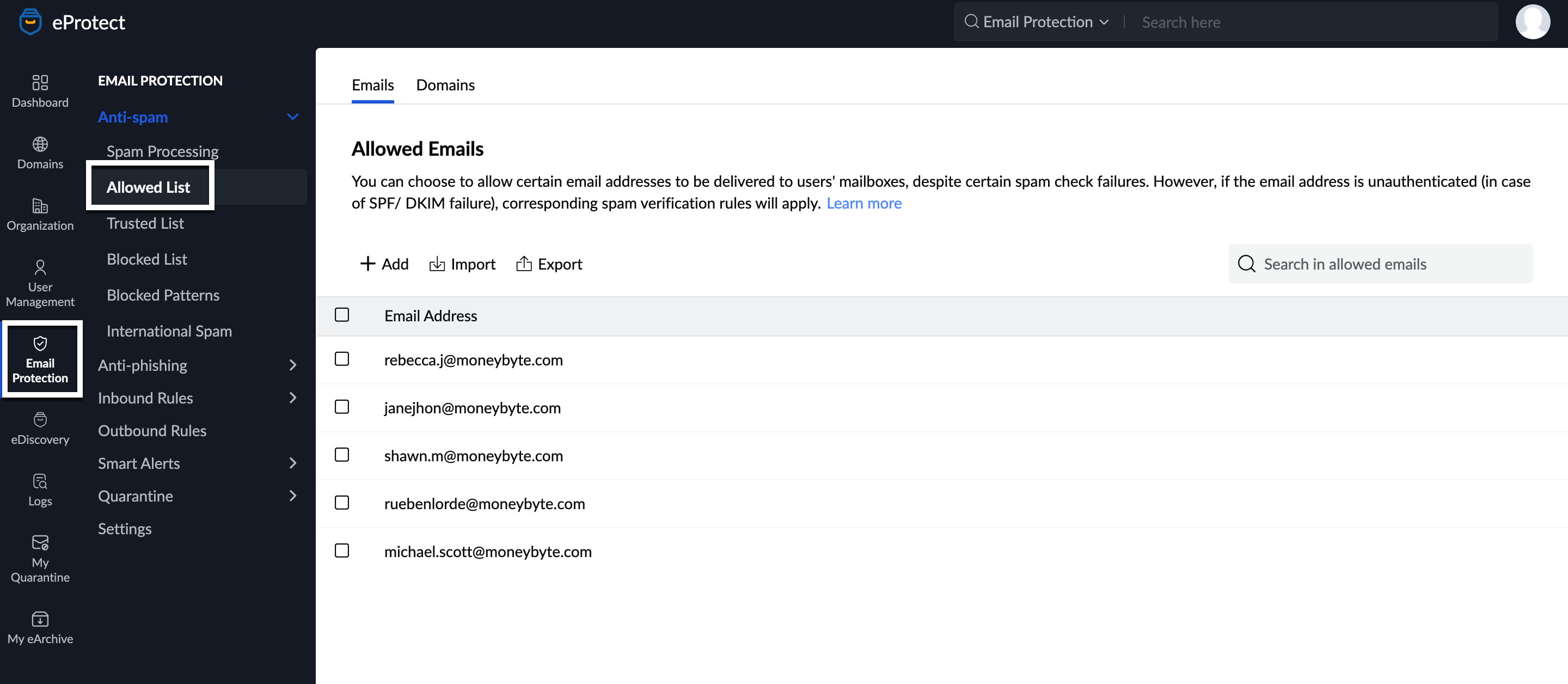
- To add a new email address to the list, follow these steps:
- Click the Add button in the Emails tab.
- Add one or more email addresses separated by a comma.
- Click Add email address.
- Alternatively, you can add email addresses in bulk by selecting the Import button on the top pane.
- Click Browse CSV Files, and select the file containing the email addresses. The email addresses in the CSV file get added to the allowed list.
- To add a new Domain to the Allowed List, navigate to the Domains tab and follow these steps:
- Click Add and enter one or more domain names separated by a comma.
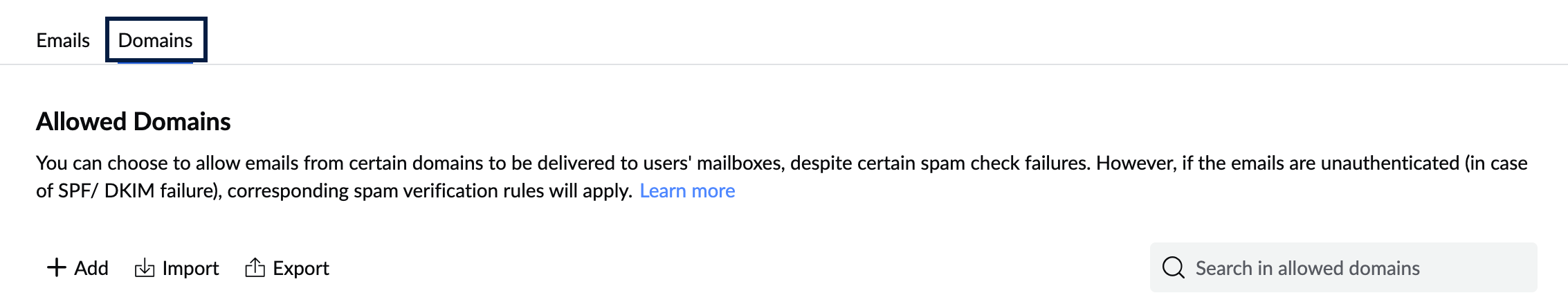
- Click the Add domain button.
- Alternatively, you can also import domains by clicking on Import.
- Click Browse CSV Files, and select the file containing the domain names. The domain names in the CSV file will get added to the allowed list.
- Click Add and enter one or more domain names separated by a comma.
- To allow emails from a certain IP address range, navigate to the IP Addresses tab and do these steps:
- Click on Add to enter the IP addresses.
- Enter the IP addresses and select the IP mask, depending on the IP range that you'd like to add. Refer here to know more about IP masks.
- Finally, click Add IP Address.
- Alternatively, you can also import IP addresses by clicking on Import.
- Click Browse CSV Files, and select the file containing the IP addresses. The IP addresses in the CSV file will get added to the allowed list.
Note:
- You can use the sample CSV file for bulk Importing email addresses or Domains.
- When you add a domain to the allowed list, any emails from its associated sub-domains won't be marked as spam.
TIP:
This option to add addresses to the Allowed List is particularly handy when you know that the sending domain has incorrect SPF/ DKIM settings and you want to allow only these domains from your otherwise strict SPF/ DKIM policies for Spam Control.
Trusted List
The trusted list is where you can add any email addresses, domains, or IP addresses that you want to exclude from any sort of spam processing. None of the usual spam checks will be conducted on emails that are received from the entities added to the trusted list and they will not be validated for SPF, DKIM, or block list checks. While adding values to the trusted list, be cautious since the organization could be exposed to spam or phishing attacks, as there is no spam check.
Follow the below instructions to define the trusted list for your organization:
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Navigate to the Trusted List section under Anti-spam. You will land in the Emails tab.
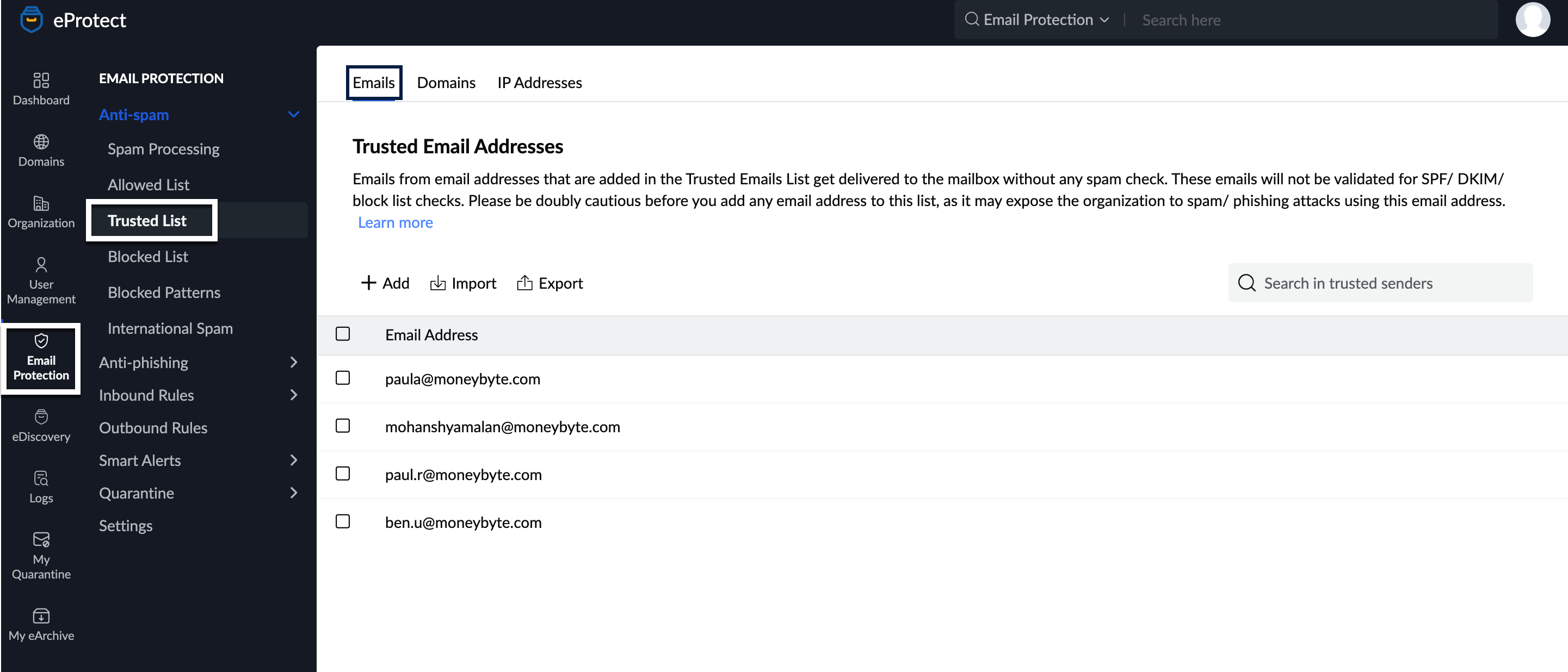
- To add specific email addresses to the trusted list, follow these steps:
- Click Add and enter one or more email addresses separated by a comma and click Add email address.
- Alternatively, you can also import email addresses by clicking on Import.
- Click Browse CSV Files, and select the file containing the email addresses. The email addresses in the CSV file will get added to the trusted list.
- To add one or more domains to the trusted list, click on the Domains tab and follow these steps:
- Click Add and enter one or more domain names separated by a comma and click Add.
- Alternatively, you can also import domains by clicking on Import.
- Click Browse CSV Files, and select the file containing the domain names. The domain names in the CSV file will get added to the trusted list.
- You can export the list of trusted domains to your local server by selecting the Export button. The list will automatically be downloaded to your device.
- Click Add and enter one or more domain names separated by a comma and click Add.
- To add one or more IP addresses to the trusted list, click on the IP Addresses tab. Follow the steps below to add to the list :
- Click on the Add button and enter the trusted IP address.
- Click Import to import the IP addresses to the list. Browse from CSV files to import the data.
- You can also export the list of trusted IPs to your local server using the Export button.
- Click on the Add button and enter the trusted IP address.
Blocked List
A Blocked list can also be defined commonly for the entire organization. The administrators can add entire domains, TLDs, specific email addresses, IP addresses, or recipient email addresses to the blocked list. In these cases, even if the domain passes the SPF test, the email from that domain will be marked as spam.
Additionally, while defining the blocked list, the admin can also choose the action to be taken on the blocked emails. They can either:
- Mark it as spam - The email will be moved to the respective user's spam folder.
- Move it to quarantine - The email will be quarantined from where the admin will have to process the email further.
- Reject the email - The email will be permanently rejected.
Follow the below instructions to define the blocked list for your organization:
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Select Anti-spam, and select Blocked List. You will land in Emails tab.
- To add specific email addresses to the blocked list, do these steps:
- Click Add and enter one or more email addresses separated by a comma.
- Select the action to be taken on these emails and click Add email address.
- Alternatively, you can also import email addresses by clicking on Import.
- Select the action to be taken on these emails.
- Click Browse CSV Files, and select the file containing the email addresses. The email addresses in the CSV file will get added to the blocked list.
- You can export the list of blocked email addresses using the Export option.
- You can further filter the email addresses in the list based on the parameters available in the Filter option.
- To add one or more domains to the blocked list, click the Domains tab and follow these steps:
- Click Add and enter one or more domain names separated by a comma.
- Select the action to be taken on these emails and click Add Domain.
- Alternatively, you can also import domains by clicking on Import.
- Select the action to be taken on these emails.
- Click Browse CSV Files, and select the file containing the domain names. The domain names in the CSV file will get added to the blocked list.
- You can export the blocked domains to your local server using the Export button.
- You can further filter out the contents to view specific data using the conditions available in the Filter option.
- Click Add and enter one or more domain names separated by a comma.
- To block emails from a certain IP address range, select the IP Addresses tab and follow these instructions:
- Click Add to enter the IP addresses.
- Enter the IP addresses and select the IP mask, depending on the IP range that you'd like to add. Click here to know more about IP masks.
- Select the action to be taken on these emails and click Add IP Address.
- Alternatively, you can also import IP addresses by clicking on Import. Select the action to be taken on these emails.
- Click Browse CSV Files, and select the file containing the IP addresses. The IP addresses in the CSV file will get added to the blocked list.
- You can export the blocked IP addresses to your local server using the Export button.
- You can further filter out the contents to view specific data using the conditions available in the Filter option.
- Click Add to enter the IP addresses.
- A Top-level Domain (TLD) is the last segment of a domain name. For example, in the domain name zylker.com, .com is the TLD. To block a TLD, click the TLDs tab and do these steps:
- Click Add and enter one or more TLDs separated by a comma.
- Select the action to be taken on these emails and click Add TLD.
- Alternatively, you can also import domains by clicking on Import.
- Select the action to be taken on these emails.
- Click Browse CSV Files, and select the file containing the TLDs. The TLDs in the CSV file will get added to the blocked list.
- You can further filter out the contents to view specific data using the conditions available in the Filter option.
- Click Add and enter one or more TLDs separated by a comma.
- If you want to block emails addressed to certain org members, click the Recipient Emails tab and do these steps:
- Click Add and enter one or more email addresses separated by a comma.
- Select the action to be taken on these emails and click Add recipient email address.
- Alternatively, you can also import email addresses by clicking on Import. Select the action to be taken on these emails.
- Click Browse CSV Files, and select the file containing the email addresses. The email addresses in the CSV file will get added to the blocked list.
- You can export the blocked recipient email addresses to your local server using the Export button.
- You can further filter out the contents to view specific data using the conditions available in the Filter option
- Click Add and enter one or more email addresses separated by a comma.
IP Addresses and IP Masks
If you are entering the entire IP address that denotes a specific machine, you will have to select the subnet as 32 from the dropdown list. If you mention just the network to denote all the computers that come under that network, enter the network part of the IP address and select the subnet depending on the number of bits that you have used in the IP address.
For example, if you are entering 172.20.0.0 and select 30 from the dropdown list, it will refer to IP addresses in the range 172.20.0.0 - 172.20.0.3. This will denote a total of 4 IP addresses. This can be derived by calculating 2(32-n). In this case, the value of n will be 30, and by performing the calculation we derive at 22, which will be 4. Hence the 4 IP addresses will be added to the respective List. Similarly, you can add a consecutive range of IP addresses by selecting the relevant value from the dropdown list.
Note:
- You will not be allowed to include your domain's TLD in your organization's Blocked List.
- The IP Address options for the allowed list and the blocked list will not be available for organizations in the free plan.
- When you add a domain to the blocked list, any emails from its associated sub-domains will be blocked too.
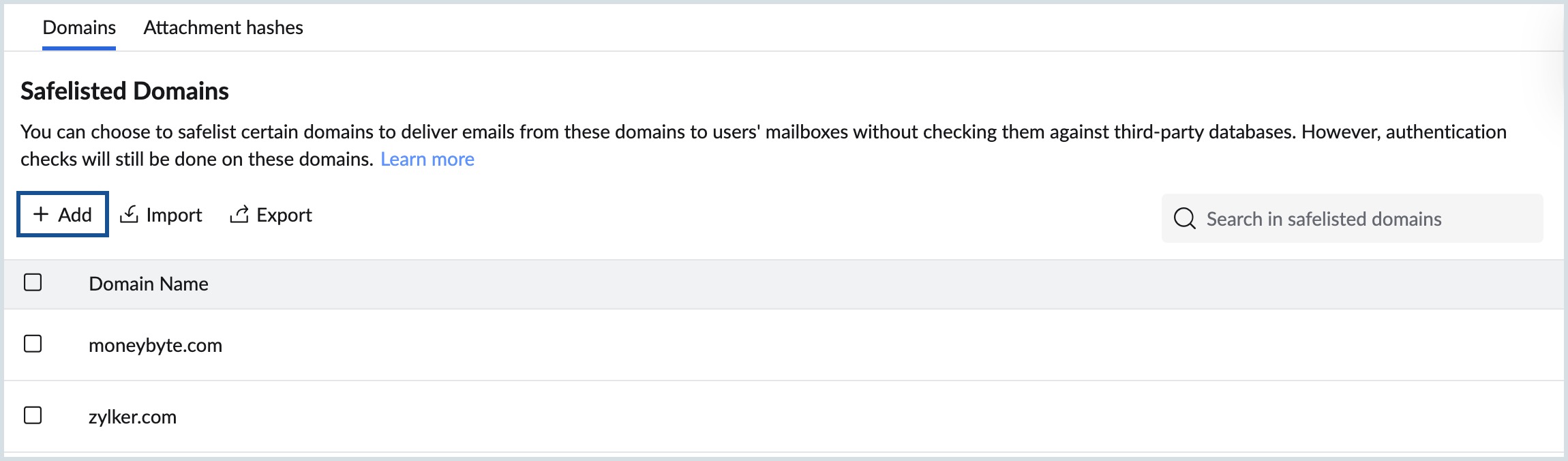
Safelist
The Safelist in Zoho eProtect will allow administrators to add trusted domains or attachment hashes to ensure that emails from these sources are delivered directly to users’ inboxes without being filtered by third-party spam or threat detection databases. However, authentication checks such as SPF, DKIM, and DMARC will still be applied.
Follow the below instructions to define the safelist for your organization:
- Log in to Zoho eProtect.
- From the left-hand pane, select Email Protection .
- Navigate to the Anti-spam section and click on Safelist.
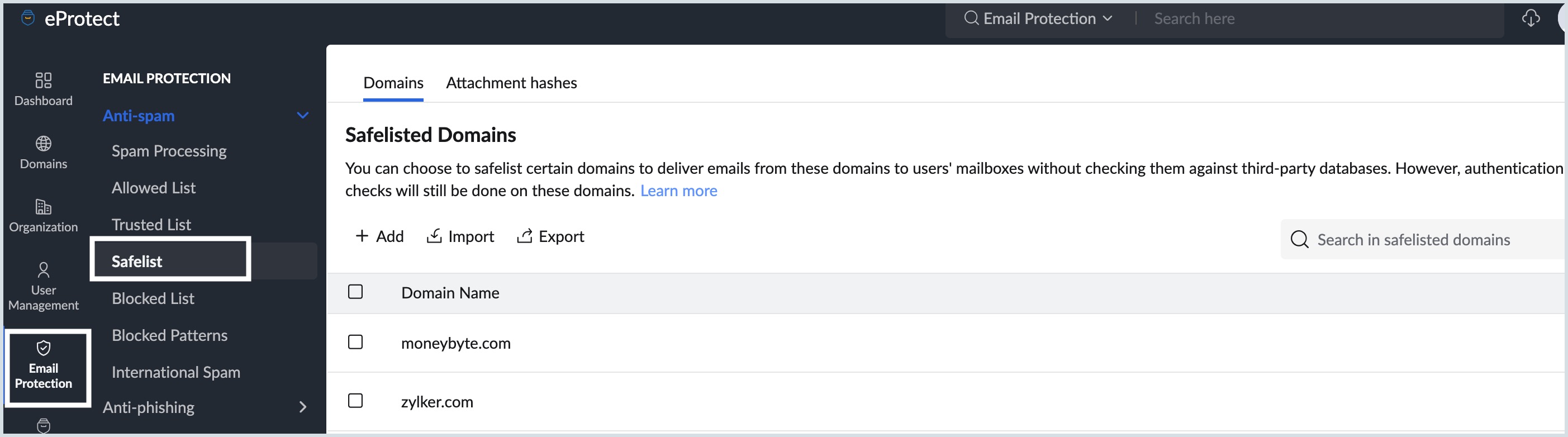
- You can safelist entries based on:
- Domains (trusted email domains)
- Attachment Hashes (trusted file identifiers)
- Use the tabs at the top to switch between Domains and Attachment hashes.
- To add entries manually:
- In the selected tab (Domains or Attachment hashes ), click Add.
- Enter one or more entries (separated by commas, up to 100 at a time).
- Click Add domains or Add attachment hashes, as applicable.
- The entries will now appear in the respective safelist table.
- To import entries from a file:
- Click Import.
- Select Browse CSV files, and select the file containing domain names or attachment hashes.
- The entries from the file will be added to the safelist.
- To export entries:
- Click Export to download the safelisted entries as a CSV file to your local system.
- To search entries:
- Use the Search bar within the selected tab to quickly locate a specific entry.
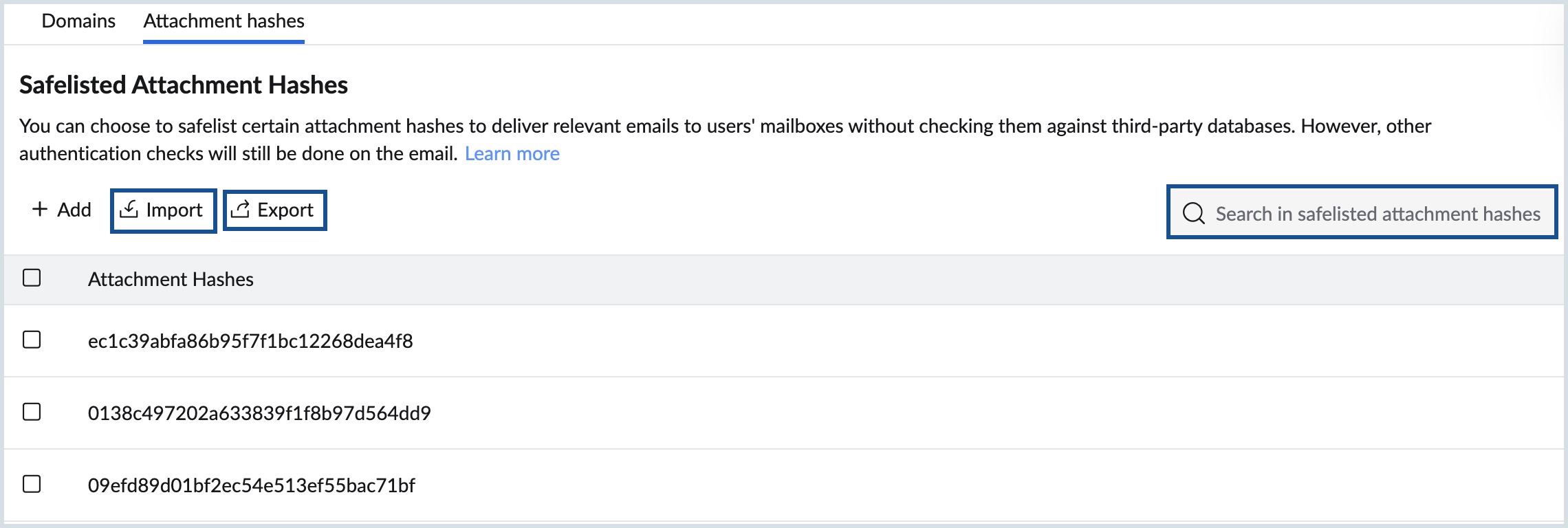
- Use the Search bar within the selected tab to quickly locate a specific entry.
Note:
- You can use the sample CSV file for bulk importing domains or attachment hashes.
- When you add a domain to the safelist, any emails from its associated sub-domains won't be marked as spam.
- Each attachment hash is 32 characters in length.
Blocked Patterns
Blocked List Patterns in Zoho eProtect will allow the administrator to add the usual patterns in which the spam emails get delivered to the users in the organization. The patterns that can be added are:
Sender Pattern
You can add texts or regular expression patterns to this list to make sure that the emails containing these patterns in the sender's email address are marked as spam. You can set the Email delivery action to mark the email as spam or move the emails to quarantine.
To configure a pattern click on Add and provide any text/regex as the pattern value. You can set an expiry date for the pattern. You can also choose to add the pattern as a regular expression. Click Add to save the pattern.
You can also Edit/ Delete a pattern using the icons provided over the saved patterns.
Subject Pattern
You can add text or regular expression patterns to this list to make sure that the emails containing these patterns in the subject of the email are marked as spam. You can set the Email delivery action to mark the email as spam or move the emails to quarantine.
To configure a pattern click on Add and provide any text/regex as the pattern value. You can set an expiry date for the pattern. You can also choose to add the pattern as a regular expression. Click Add to save the pattern.
You can also Edit/ Delete a pattern using the icons provided over the saved patterns.
Content Pattern
You can add text or regular expression patterns to this list to make sure that the emails containing these patterns in the content of the email are marked as spam. You can set the Email delivery action to mark the email as spam or move the emails to quarantine. You also have the option to Mark blank emails as spam.
To configure a pattern click on Add and provide any text/ regex as the pattern value. You can set an expiry date for the pattern. You can also choose to add the pattern as a regular expression. Click Add to save the pattern.
You can also Edit/ Delete a pattern using the icons provided over the saved patterns.
International Spam
Language-based spam
You can allow or reject emails based on the language of the email. You can set the languages according to your preference in the Zoho eProtect.
Follow these steps to add languages:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Select Anti-spam, and navigate to International Spam. You will land in the Language tab.
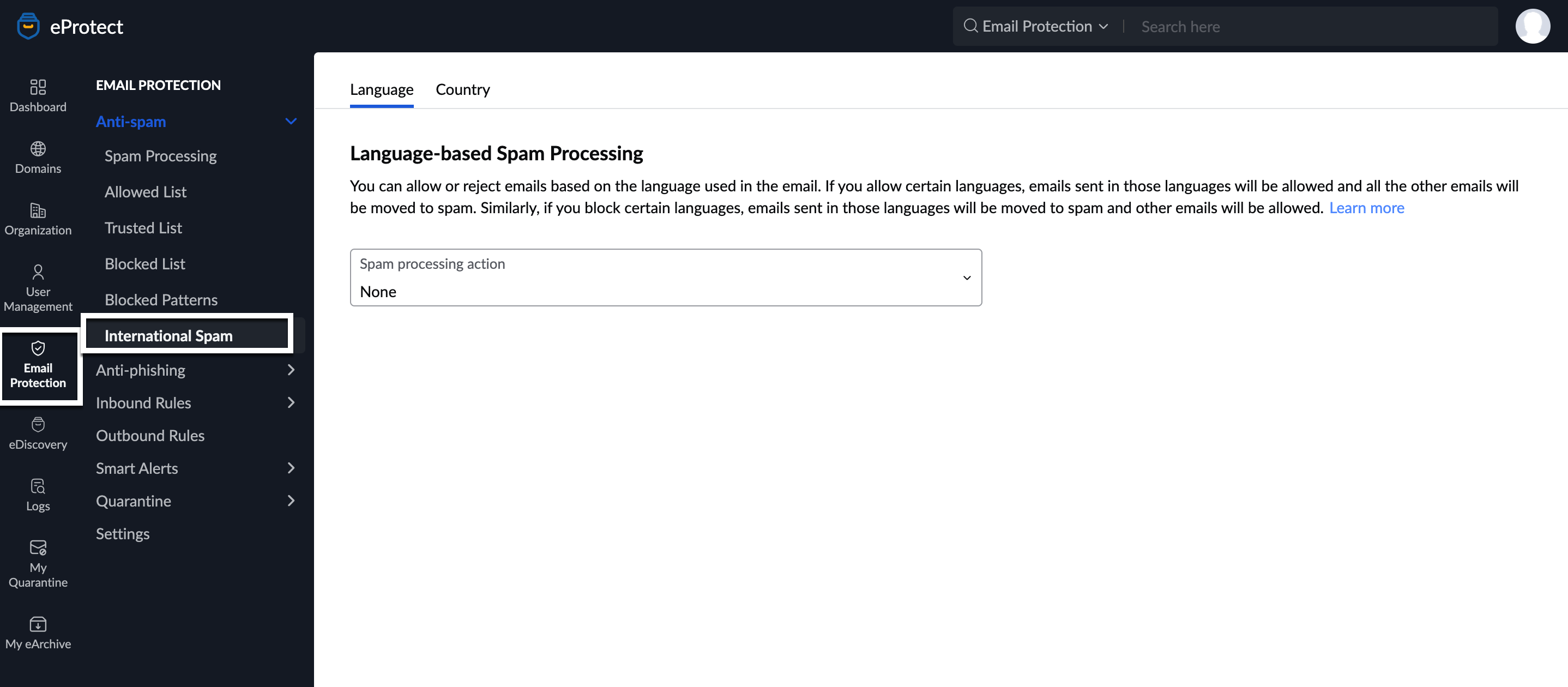
- Select the action that you'd like to take in the Spam processing action drop-down.
- Select either Allowed languages only or Block chosen languages.
- Select the languages, and finally click Apply.
Based on the preferences set, emails in the languages that you've entered will either be blocked or allowed.
Country-based spam processing
Based on the location of the origin of emails, you can either reject the email, mark it as spam or move it to the quarantine list.
Follow the below steps to add locations:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Select Anti-spam, select International Spam, and select the Country tab.
- Click on Add.
- Select the countries, and choose the respective action that you'd like to take on emails from these countries.
- You can either mark the emails as spam, move it to quarantine or reject it.
Emails from the respective countries will be processed according to the preferences that you have set.
Anti-Phishing
Zoho eProtect lets you customize the actions that need to be taken when certain emails fail verification of protocols such as SPF, DKIM, DMARC, etc. You can choose an action that best suits your organization's requirements from the actions permitted.
Spoof Protection
The Spoof Protection section in Zoho eProtect contains multiple settings with which you can configure your organization's spoof protection. Listed below are the spoof control settings available in eProtect:
SPF Verification
SPF or Sender Policy Framework is the DNS record that defines the email servers that are allowed to send emails based on the particular domain. For incoming emails, the SPF validation is based on the sending domain's published SPF Record and the IP from which the emails are received. In case of a conflict, the SPF validation returns soft fail or fail for the emails. The administrator can choose to 'Temporary Reject' or 'Reject' or 'Allow (Process further)' or 'Move the emails to Quarantine' for the SPF Soft Fail and Fail cases.
To customize the action on emails that have failed SPF validation, follow the below instructions:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Spoof Protection under Anti-Phishing.
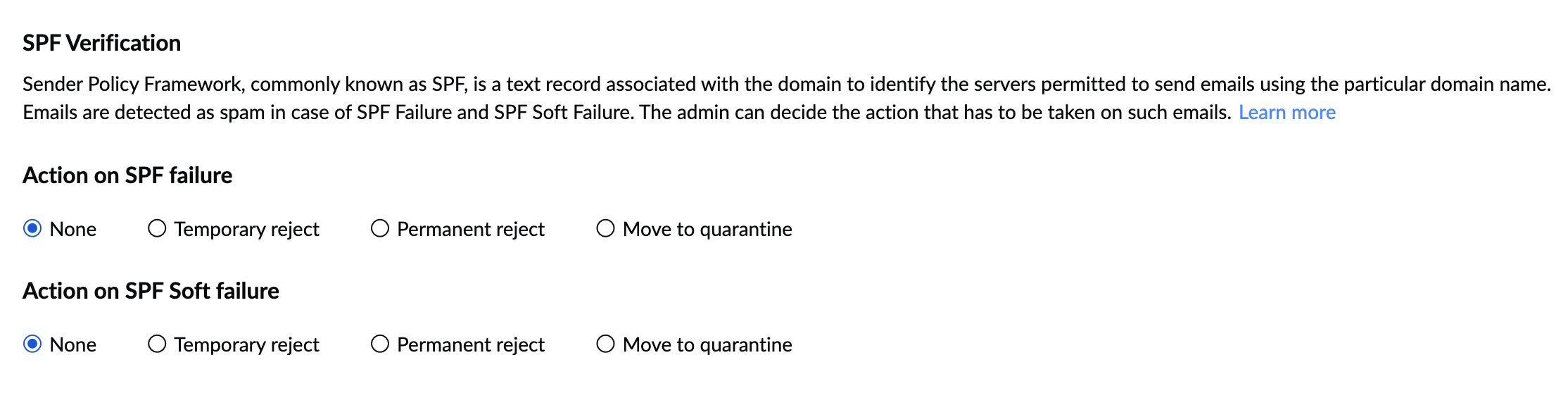
- Under SPF Verification, select the actions for SPF failure and SPF soft failure.
- Permanent reject: To directly bounce back the emails, if the SPF fails/ soft fails based on the option chosen.
- Temporary reject: To temporarily reject emails with 4xx errors. The retries will be checked for SPF Again and will be accepted if the sender has corrected or updated the SPF records.
- Move to quarantine: To move the email to the spam quarantine, for review by the administrator.
- None: To move the email to further spam processing, without rejecting the email.
DKIM Verification
When an incoming email has a DKIM signature in the header, the DKIM validation happens for the email. In case the DKIM is found not valid, then the administrator can choose one of the available actions for such emails.
To customize the action on emails that have failed DKIM validation, follow the below instructions:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Spoof Protection under Anti-Phishing.
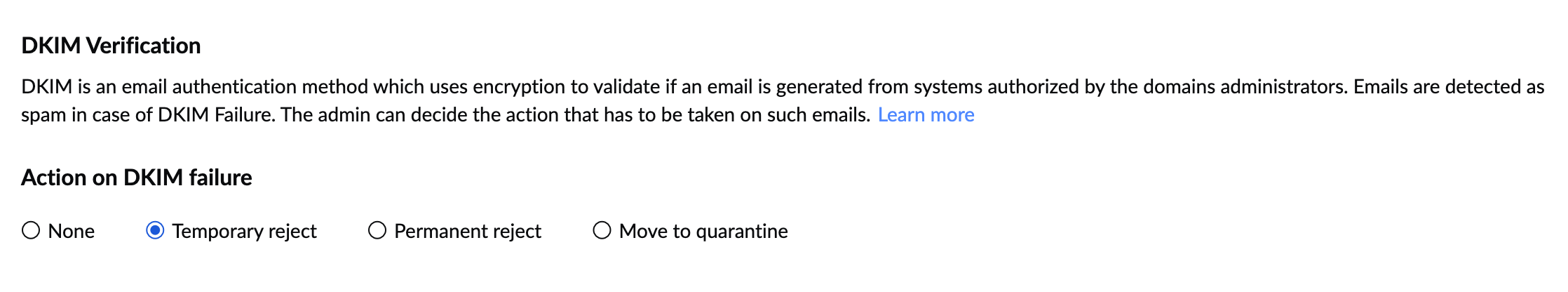
- Under DKIM Verification, select the desired action.
- Permanent reject: To directly bounce back the emails, if the DKIM validation fails based on the option chosen.
- Temporary reject: To temporarily reject emails with 4xx errors. The retries will be checked for DKIM again and will be accepted if the sender has corrected or updated the DKIM records.
- Move to quarantine: To move the email to the spam quarantine, for review by the administrator.
- None: To move the email to further spam processing, without rejecting the email.
DMARC Verification
DMARC policy is an email authentication protocol built on the widely deployed SPF and DKIM protocols. If there is an authentication failure, and the DMARC policy is set to quarantine, the administrator of the recipient domain can choose one of the available actions to perform on the emails.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Spoof Protection under Anti-Phishing.

- Under DMARC Verification, select the desired action.
- None: To move the email to further spam processing, without rejecting the email.
- Move to spam: To mark the email as spam, without any further checks.
- Move to quarantine: To move the email to the spam quarantine, for review by the administrator.
DNSBL Verification
Zoho maintains a consolidated Blocklist based on User Spam Marking, Abuse patterns, and certain third-party Blocklists subscribed by us. Similar to SPF and DKIM, the organization administrator can add rules to control the execution of the Zoho Blocklist. The administrator can control the delivery of emails based on his organization's requirements.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Spoof Protection under Anti-Phishing.
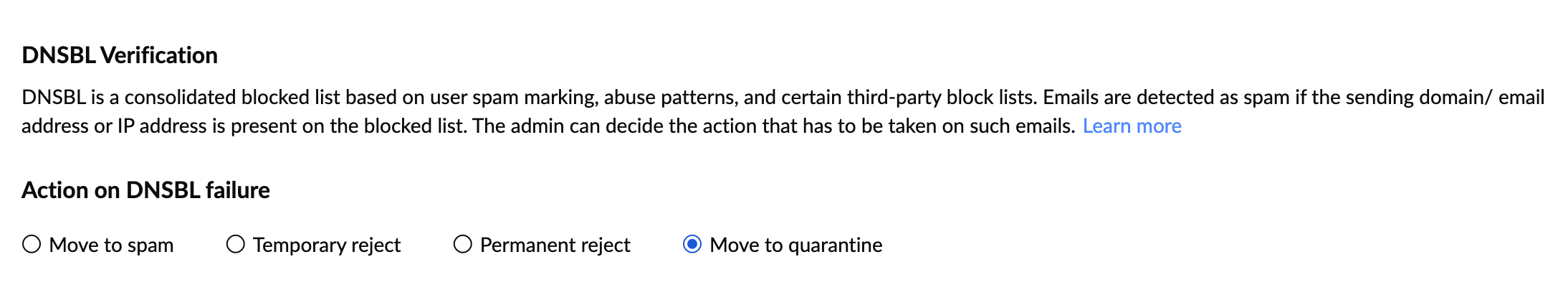
- Under DNSBL Verification, select the desired action.
- Permanent reject: To directly bounce back the emails, if the sending domain/ email address or IP address is present in the Zoho Blocklist.
- Temporary reject: To temporarily defer the emails, if the sending domain/ email address or IP address is present in the Zoho Blocklist.
- Move to spam: To mark the email as spam, without any further checks.
- Move to quarantine: To move the email to the Spam Quarantine, for review by the administrator.
Cousin Domains
Cousin Domains are domain names that are very similar to any other valid domain name. If you expect a domain to send genuine emails, but want to mark an email from any other variations of the domain name as spam, you can add it in this section.
For example, if 'zylker.com' sends genuine emails, but emails from 'zylker1.com' need to be processed for spam, you can add zylker.com here. Follow these steps to add Cousin Domains:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Cousin Domains under Anti-Phishing and enable Cousin Domain Verification.
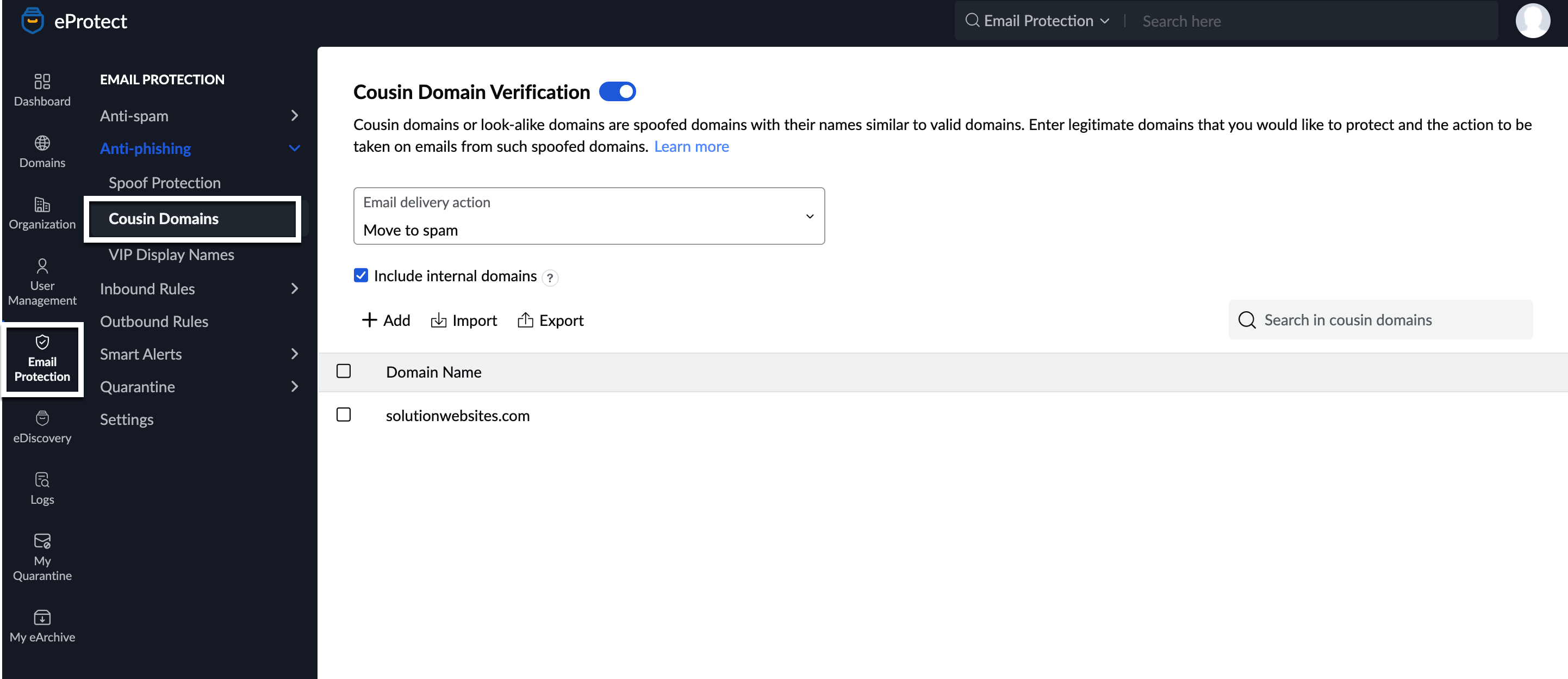
- In the Email Delivery Action dropdown, select the actions for emails that have look-alike domain names.
- If you select None, no action will be taken.
- If you select Move to spam, the email will be moved to the spam folder of the email recipient.
- If you select Move to quarantine, the email will be moved to the quarantine list, from where the admin will have to process it further.
- You can also choose to Include Internal Domains, which means that all of your organization's domains will undergo the cousin domains check by default. So, any domain name that is similar to yours will undergo the specified action.
- Click Add, enter the domain names for which the cousin domain check has to be done and click Add domain.
- You can also choose to include the domain names by clicking on Import, and selecting a CSV file which has all the domain names.
- In the Email Delivery section, select the action for emails that have similar domain names.
- In the Domain List, enter the names of domains for which the cousin domain check has to be done.
The Cousin Domains feature is especially useful in cases where an email sender might try to trick recipients with a valid domain name.
For example, you might expect the domain webhosting.com to send valid emails to your org users. So, when an email arrives from user@vvebhosting.com, your org members might consider it legitimate, but the email sender has tricked the recipient by replacing the 'w' in webhosting.com with 'vv'. In cases like these, the Cousin Domains feature comes into play.
VIP Display Names
Administrators can control the fraudulent usage of display names by setting up the respective conditions for emails that violate your customization. You can set up a display name and associate one or more email addresses with this display name in the Zoho eProtect.
For example, consider the email address ceo@mydomain.com, you can ensure that if an email with the display name 'CEO' arrives from any other email address, the action defined by you is taken on this email address.
Follow the below steps to add a policy to prevent display name fraud:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to VIP Display Names under Anti-Phishing.
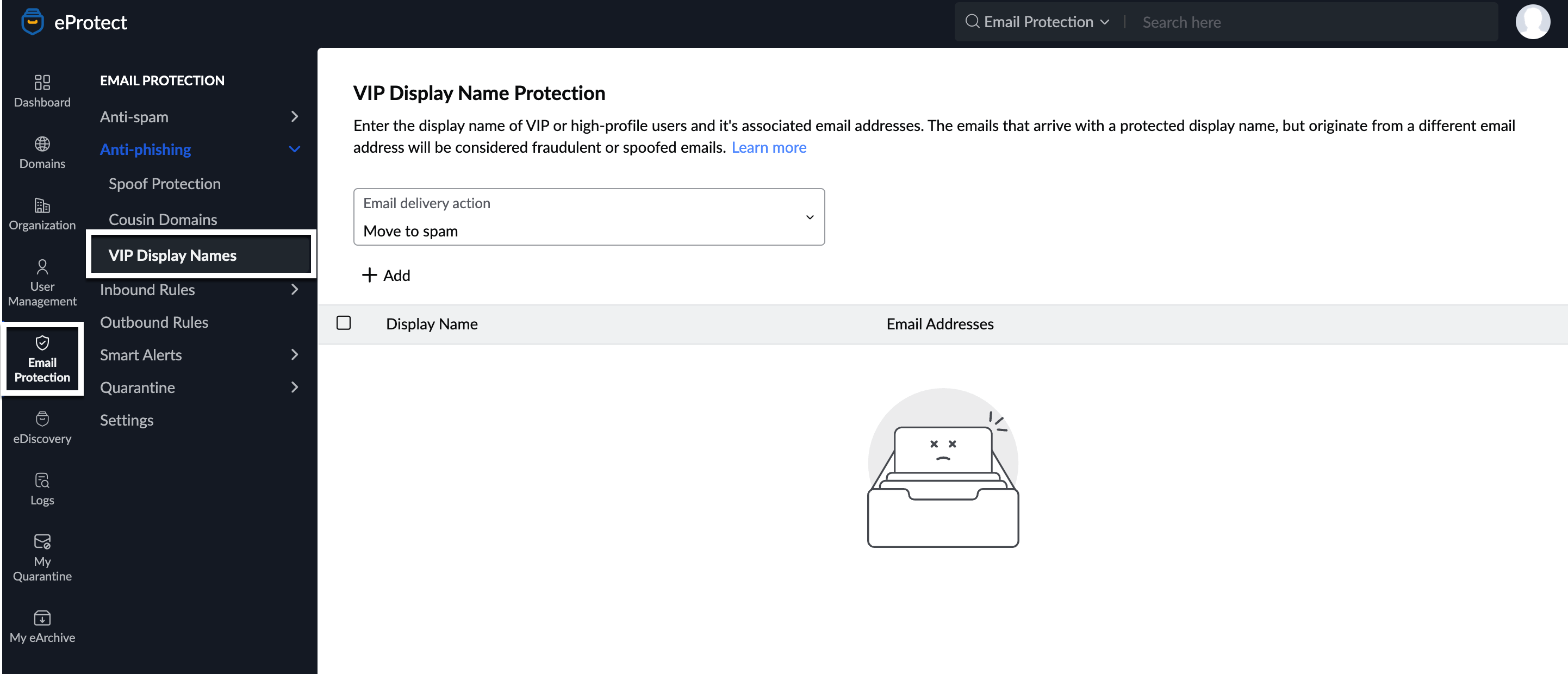
- In the Email Delivery Action drop-down, select the action for emails that have spoofed display names.
- If you select None, no action will be taken.
- If you select Move to spam, the email will be moved to the spam folder of the email recipient.
- If you select Move to quarantine, the email will be moved to the quarantine list, from where the admin will have to process it further.
- Click Add, enter the display name, and the email addresses that can be associated with this name, and click Add users.
You will be able to see a list of the Display Names and the respective Email Addresses that you have added to the list.
URL Protection
Zoho eProtect's URL Protection prevents phishing, malware, and data breaches by scanning, analyzing, and restricting access to unsafe URLs in emails. It includes three security features:
URL Rewriting and Time-of-click Protection
URL rewriting is a security feature that rewrites all URLs within email content into safe, controlled versions. This process also removes any tracking parameters that may be embedded in the original links, thereby protecting user's personal data from third-party trackers.
Time-of-Click Protection works alongside URL rewriting to provide real-time threat detection. When a user clicks a rewritten link, they are redirected to a security checkpoint. If the URL is safe, they’re forwarded to the intended destination. If the link is identified as malicious or suspicious, access is blocked, and the user is shown an alert. This ensures dynamic, real-time protection against phishing, spoofing, and malware threats.
Follow these steps to enable URL rewriting:
- Log in to Zoho eProtect.
- From the left pane, select Email Protection.
- Navigate to URL Protection under the Anti-Phishing section.
- Enable the URL Rewriting option by toggling it on.
- Optionally, turn on toggle to enable URL rewriting for outgoing emails sent by your organization's users.
- To enable Time-of-Click Protection, turn on the toggle.
- Select the types of URLs to monitor:
- Fraudulent URLs (Spoofing links)
- Malicious URLs (Phishing links)
- URLs in which the actual link is different from the displayed link (Redirected URLs).
- Alert user upon clicking a link that triggers a malware file download.
- URLs in which the domain displayed is different from the actual one
- URLs in emails classified as spam based on organizations' spam settings
- Unencrypted URLs or unsafe URLs with possible trackers
Note:
- Time-of-Click Protection functions only on rewritten URLs. It is strongly recommended to keep URL rewriting enabled once Time-of-Click Protection is enabled.
- For most unsafe links, users will see a warning alert with an option to proceed.
- For high-risk threats (like malware or blocked URLs based on organization's policy), users will be fully restricted from accessing the destination.
- If you want to block users from proceeding with any unsafe URL, you can enable the Restrict Unsafe URL. When this setting is enabled, all unsafe URLs will be blocked, and users will not have an option to bypass the warning.
Restrict Unsafe URL
URL Restriction is a security feature that prevents users from accessing harmful links in emails. When enabled, it automatically blocks any URL that has been identified as potentially unsafe by Zoho eProtect.
Follow these steps to enable Restrict Unsafe URL:
- Log in to Zoho eProtect.
- From the left pane, select Email Protection.
- Navigate to URL Protection under the Anti-Phishing section.
- Enable the Restrict Unsafe URL option by toggling it on.
Inbound Rules
Connection Filtering for Inbound Rules
With the help of connection filtering rules, you can decide which emails get to reach your inbox and filter out unnecessary emails right at the authentication level. In order to filter out emails, you have to establish a set of conditions against which the incoming emails of your organization will be validated before transferring them to the respective inboxes.
Create a Connection Filtering Rule
To create a connection filtering rule,
- Log in to the Zoho eProtect and select Email Protection on the left pane.
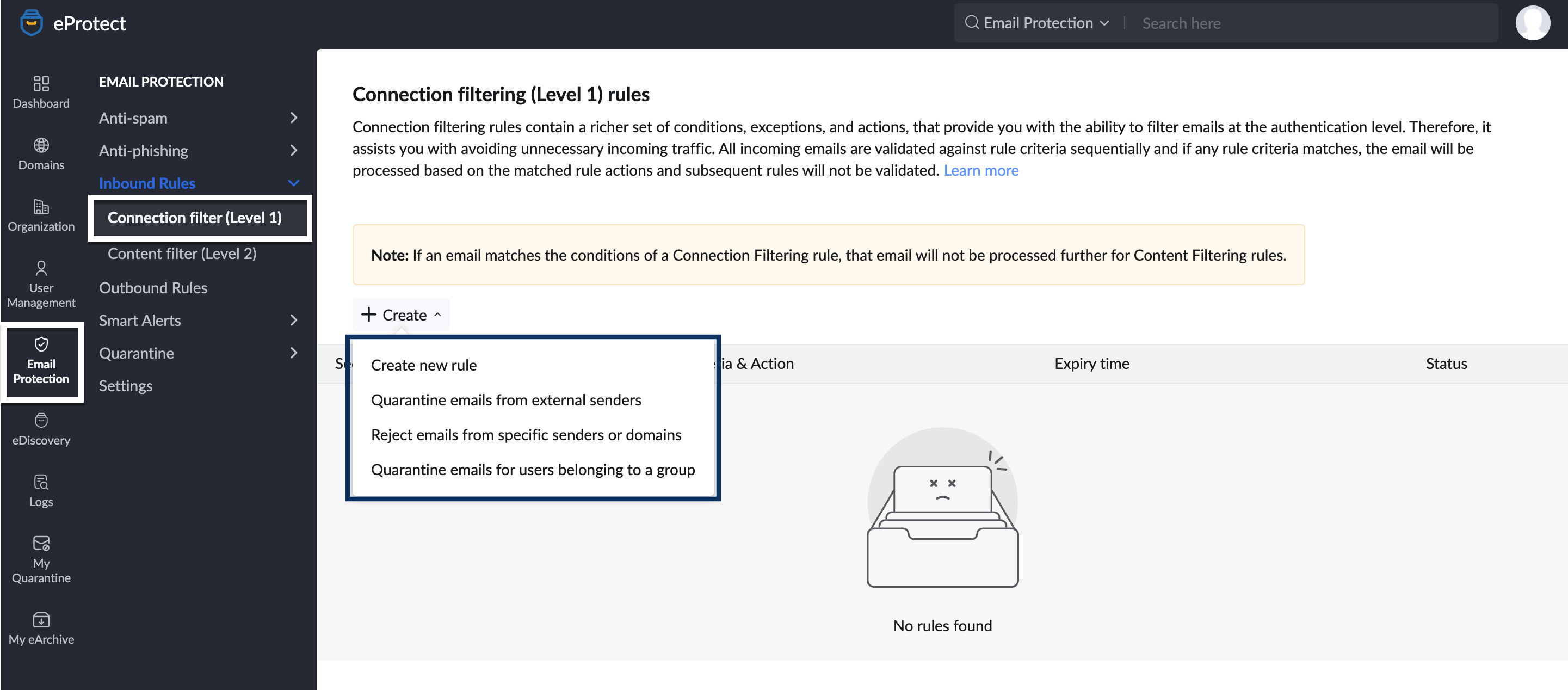
- Navigate to Inbound Rules and click Connection filter (Level 1).
- Click the Create button and select the preferred option:
- Create new rule
- Quarantine emails from external senders
- Reject emails from specific senders or domains
- Quarantine emails for users belonging to a group
- Enter the rule name, provide an optional description and click Proceed.
- Choose the Condition type.
- AND - Only if the incoming emails satisfy all the conditions you provided, the preferred action will be performed.
- OR - Even if the incoming emails satisfy one of the conditions you provided, the preferred action will be performed.
- Advanced - You can combine both AND & OR condition types, within a single condition, for the preferred action.
- No Condition - When chosen, all the emails you receive will go through the preferred action.
- Select your condition, operating parameter and enter the appropriate value in the Add values field.
- Click the + icon to add multiple Conditions.
Select the desired action and click Proceed.
Action Description Move to spam All the emails that satisfy the given condition/s will be moved to the spam folder of the recipient's inbox. Permanent Reject All the emails that satisfy the given condition/s will not be accepted by our servers and will be rejected permanently removing the chances of delivery retries. Move to quarantine The emails that satisfy the given condition/s will be moved to quarantine for the administrator's approval. None (Allow email) No action will be taken for emails that satisfy the given condition/s. - In the APPLY TO page, you can choose to which users you want the rule to be applied. You can select one of the options below:
- All Users - The rule will be applied to all the users in your organization.
- Selected Users - The rule will be applied to the specific set of users you add.
- All users except selected users - The rule will be applied to all the users except the ones added to the list.
- To add users to the Selected Users or Excluded users list, simply select the respective option, and click the Add button. Select the users you want to add to the list and click Proceed. You can also remove a user from the list by clicking the Delete icon next to the user.
- Once done, click Proceed. On the preview page, you can review your rule and set an expiry date if needed.
- After reviewing your rule, you can,
- Create & Enable Rule - Your rule will not only be created but also be activated automatically to start processing emails with respect to its conditions and actions.
- Create Rule - Your rule will only be created and not activated. That means if you want the rule to be applied to the emails you receive, you will have to manually activate it.
Available Conditions
You can set up more than one condition in a single rule depending on your requirement.
| Parameter | Description |
| Subject | The subject of the email |
| Sender email address | The 'from' address of the email sender |
| Sender domain | The domain address of the email sender |
| Return path email address | The reverse-path/ bounce address of an incoming email |
| Return path domain | The reverse-path/ bounce address's domain |
| Sender IP address | The IP address of the email sender |
| Is external sender | Checks if the sender is not part of the organisation |
| Originating country | The country from which the email was sent |
| Sender DNS | The DNS address of the sender |
| Sender display name | The display name of the sender. |
| SPF verification result | The result of SPF verification |
| DKIM verification result | The result of DKIM verification |
| DMARC verification result | The result of DMARC verification |
| MIME message ID* | The ID that can be gathered from a MIME email's header |
| X Mailer** | The desktop client from which the email was sent |
| Sender not previously contacted | Checks if the recipient has previously sent any emails to the sender |
| To email address | The 'to' email address of the incoming email |
| MIME size in Mb | The size of the non-text attachment is greater than the specified MB |
| Add header criteria | The type of email header criteria that needs to be verified for the provided values |
Note:
- *MIME message - Multipurpose Internet Mail Extensions supports non-text email attachments. A MIME header is added to the original email header from where you can gather the unique content ID/message ID used to identify the message.
- **X-Mailer - Specifies which desktop client (For example, Apple client, Thunderbird, etc) was used to draft or send the email. Can be found in the email header.
Operating Parameters
| Operators | Description |
| is | The respective parameter in the incoming email should exactly match the given criteria value. |
| is not | The respective parameter in the incoming email should not match the given criteria value. |
| contains | The respective parameter in the incoming email doesn't have to be an exact match but will pass even if it contains the given criteria value. |
| does not contain | The respective parameter in the incoming email doesn't have to be an exact match but will pass if it does not contain the given criteria value. |
| begins with | The respective parameter in the incoming email should begin with the given criteria value. |
| ends with | The respective parameter in the incoming email should end with the given criteria value. |
| is empty | The respective parameter in the incoming email should be empty. |
| is not empty | The respective parameter in the incoming email should not be empty. |
| matches | The respective parameter in the incoming email should match the regular expression pattern |
| Does not match | The respective parameter in the incoming email should not match the regular expression pattern |
| true | The given condition should be true. |
| false | The given condition should be false. |
| is greater than | The respective parameter in the incoming email should only be greater than the given criteria value. |
| is lesser than | The respective parameter in the incoming email should only be lesser than the given criteria value. |
| is greater than or equal to | The respective parameter in the incoming email can be greater than or equal to the given criteria value. |
| is lesser than or equal to | The respective parameter in the incoming email can be lesser than or equal to the given criteria value. |
After selecting the Conditions and the Operating parameters, provide the values with respect to the chosen conditions that need to be verified against. Upon providing these proceed to select the Actions that need to be performed for the emails with the chosen conditions.
Rule processing and priority
You can add any number of connection filters to process different types of incoming emails. In the case of multiple filters, the sequence of processing will be based on the priority of filters. The filter with the highest priority (1) will take precedence over the filters with lower priority (2). To change the sequence or priority of the filters,
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Connection filter (Level 1).
- On the connection filtering page, you will find the list of all filters you have already added.
- Simply rearrange the filters by dragging and dropping them in the order of your preference.
Enable or Disable a rule
You can enable or disable a rule to start or stop filtering.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Connection filter (Level 1).
- On the connection filtering page, you will find the list of all filters you have already added.
- Toggle the Status key to ON/OFF in order to Enable or Disable a rule.
Remove expired rules from the list
In case you set an expiry date for the rules, you will find a number of expired conditions in your list. You can remove them by using the Delete option.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Connection filter (Level 1).
- On the connection filtering page, click Delete.
This will remove all the filters that have already expired from your list.
Content filtering for incoming emails
With the help of content filtering rules, you can decide which emails get to reach your inbox and filter out unnecessary emails based on the content of the email. In order to filter out emails, you have to establish a set of conditions against which the incoming emails of your organization will be validated before transferring them to the respective inboxes. Content filtering will also support all the connection filtering criteria.
Table of Contents
- Create a new content filtering rule
- Rule processing and priority
- Enable or Disable a rule
- Remove expired rules from the list
Create a Content Filtering Rule
To create a content filtering rule,
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and select Content filter (Level 2).
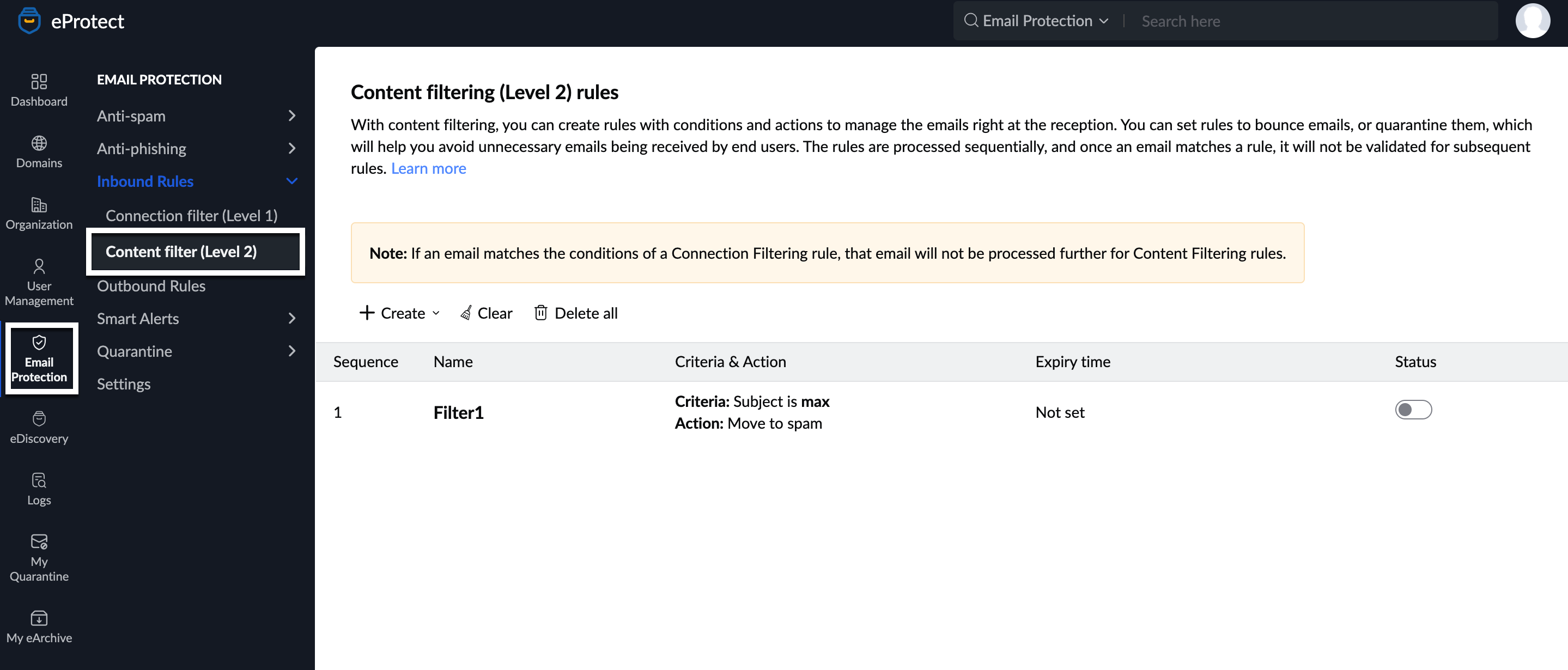
- Click Create and select the preferred option:
- Create new rule
- Quarantine emails from external senders
- Mark blank emails as spam
- Move emails with .exe attachments to spam
- Quarantine emails for users belonging to a group
- Enter a rule name, provide a description and click Proceed.
- Before providing the Conditions, based on which the processing of emails would take place, you can choose a condition type.
- AND - Only if the incoming emails satisfy all the conditions you provided, the preferred action will be performed.
- OR - Even if the incoming emails satisfy one of the conditions you provided, the preferred action will be performed.
- Advanced - You can combine both AND & OR condition types, within a single condition, for the preferred action.
- No Condition - When chosen, all the emails you receive will go through the preferred action.
- Choose the condition for the rule, operating parameter and enter the appropriate value.
- Click the + icon to add multiple conditions.
Select the preferred action:
Action Description Move to spam All the emails that satisfy the given condition/s will be moved to the spam folder of the recipient's inbox. Move to spam & Append text to subject Emails that satisfy the given condition/s will be moved to the recipient's spam folder & a prefix configured in this rule will be added to the subject of the received mail. Move to spam & Add custom header Emails that satisfy the given condition/s will be moved to the recipient's spam folder & a custom header with name and value will be added to those emails Move to quarantine The emails that satisfy the given condition/s will be moved to quarantine for the administrator's approval. Append text to subject A prefix configured in this rule will be added to the subject of the received mail Add custom header A custom header with name and value will be added to the emails. None (Allow email) No action will be taken for the emails that satisfy the given condition/s. - After creating the filter, you can choose to which users you want the rule to be applied. You can select one of the options below.
- All Users - The rule will be applied to all the users in your organization.
- Selected Users - The rule will be applied to the specific set of users you add.
- All users excluding selected users - The rule will be applied to all the users except the ones added to the list.
- To add users to the Selected Users or Excluded users list, simply select the respective option, and click the Add button. Select the users you want to add to the list and click Proceed. You can also remove a user from the list by clicking the Delete icon next to the user.
- Once done, click Proceed. On the preview page, you can review your rule and set an expiry date if needed.
- After reviewing your rule, you can,
- Create & Enable Rule - Your rule will not only be created but also be activated automatically to start processing emails with respect to its conditions and actions.
- Create Rule - Your rule will only be created and not activated. That means if you want the rule to be applied to the emails you receive, you will have to manually activate it.
Note:
If an email falls under the conditions set under Connection filtering, the conditions for Content filtering will not be processed for that email
Available Conditions
You can set up more than one condition in a single rule depending on your requirement.
| Parameter | Description |
| Subject | The subject of the email |
| Sender email address | The 'from' address of the email sender |
| Sender domain | The domain address of the email sender |
| Return path email address | The reverse-path/ bounce address of an incoming email |
| Return path domain | The reverse-path/ bounce address's domain |
| Sender IP address | The IP address of the email sender |
| Originating country | The country from which the email was sent |
| Sender DNS | The DNS address of the sender |
| Sender display name | The display name of the sender. |
| SPF verification result | The result of SPF verification |
| DKIM verification result | The result of DKIM verification |
| DMARC verification result | The result of DMARC verification |
| MIME message ID | The ID that can be gathered from a MIME email's header |
| X Mailer | The desktop client from which the email was sent |
| Sender not previously contacted | The sender is not on the contact list of the recipient |
| To email address | The 'to' email address of the incoming email |
| MIME size in Mb | The size of the non-text attachment is greater than the specified Mb |
| Add header criteria | The type of email header criteria that needs to be verified for the provided values |
| Is external sender | The sender is not a member of the organisation |
| To/cc email address | The 'to' or 'cc' email address of the incoming mail |
| Recipient (group) | Checks if the recipient belongs to the organisation group |
| Recipient's email policy | The email policy applied to the recipient |
| Recipient domain | The domain name of email recipients |
| Content | The content of the email |
| Attachment type | The type of attachments present in the email |
| Attachment size | Attachments that exceed the specified size |
| Email language | The language in which the email was composed |
| Has attachment | The existence of an attachment in an email content |
| Has web bugs | The existence of web bugs in an incoming email content |
| Has JavaScript content | The existence of javascript content in the email content |
| Has macros | The existence of macros in the email content |
| Has frame tags | The existence of iframe tags in the email content |
| Is bulk email | Checks if the email received is a bulk email |
| Has object tags | The existence of object tags in the email content |
| Has embed tags | The existence of embed tags in the email content |
| Has form tags | The existence of form tags in the email content |
| Has shortened URL | The existence of shortened URLs in the email content |
| Has suspicious macros | The existence of suspicious macros in the email content |
| URL domain | The domain names of the URLs available in email content |
| URL | The existence of specified URLs in the email content |
Note:
- MIME message - Multipurpose Internet Mail Extensions supports non-text email attachments. A MIME header is added to the original email header from where you can gather the unique content ID/message ID used to identify the message.
- X-Mailer - Specifies which desktop client (For example, Apple client, Thunderbird, etc) was used to draft or send the email. Can be found in the email header.
Operating parameters
| Operators | Description |
| is | The respective parameter in the incoming email should exactly match the given criteria value. |
| is not | The respective parameter in the incoming email should not match the given criteria value. |
| contains | The respective parameter in the incoming email doesn't have to be an exact match but will pass even if it contains the given criteria value. |
| does not contain | The respective parameter in the incoming email doesn't have to be an exact match but will pass if it does not contain the given criteria value. |
| begins with | The respective parameter in the incoming email should begin with the given criteria value. |
| ends with | The respective parameter in the incoming email should end with the given criteria value. |
| is empty | The respective parameter in the incoming email should be empty. |
| matches | The respective parameter in the incoming email should match the regular expression pattern |
| Does not match | The respective parameter in the incoming email should not match the regular expression pattern |
| true | The given condition should be true. |
| false | The given condition should be false. |
| is greater than | The respective parameter in the incoming email should only be greater than the given criteria value. |
| is lesser than | The respective parameter in the incoming email should only be lesser than the given criteria value. |
| is greater than or equal to | The respective parameter in the incoming email can be greater than or equal to the given criteria value. |
| is lesser than or equal to | The respective parameter in the incoming email can be lesser than or equal to the given criteria value. |
Rule processing and priority
You can add any number of content filters to process different types of incoming emails. In the case of multiple filters, the sequence of processing will be based on the priority of filters. The filter with the highest priority (1) will take precedence over the filters with lower priority (2). To change the sequence or priority of the filters,
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Content filter.
- On the content filter page, you will find the list of all filters you have already added.
- Simply rearrange the filters by dragging and dropping them in the order of your preference.
Enable or Disable a rule
You can enable or disable a rule to start or stop filtering.
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Content filter.
- On the content filter page, you will find the list of all filters you have already added.
- Toggle the Status key to ON/OFF in order to Enable or Disable a rule.
Remove expired rules from the list
In case you set an expiry date for the rules, you will find a number of expired conditions in your list. You can remove them by using the Delete option.
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Navigate to Inbound Rules and click Content filter.
- On the connection filtering page, click Delete.
This will remove all the filters that have already expired from your list.
Outbound Rules
With the help of Outbound Rules, you can decide which emails can be sent by the users and filter out unnecessary emails based on the entire content of the email including the email header, email content and attachment content. In order to filter the outgoing emails, you have to establish a set of conditions against which all the outgoing emails of your organisation will be validated. The rules are processed sequentially, and once a particular rule is processed, subsequent rules will not be processed.
Table of Contents
- Create a new outbound rule
- Rule processing and priority
- Enable or Disable a rule
- Remove expired rules from the list
Create an Outbound Rule
To create a new Outgoing rule,
- Log in to the Zoho eProtect and select Email Protection on the left pane.
- Navigate to Outbound Rules and click Create.
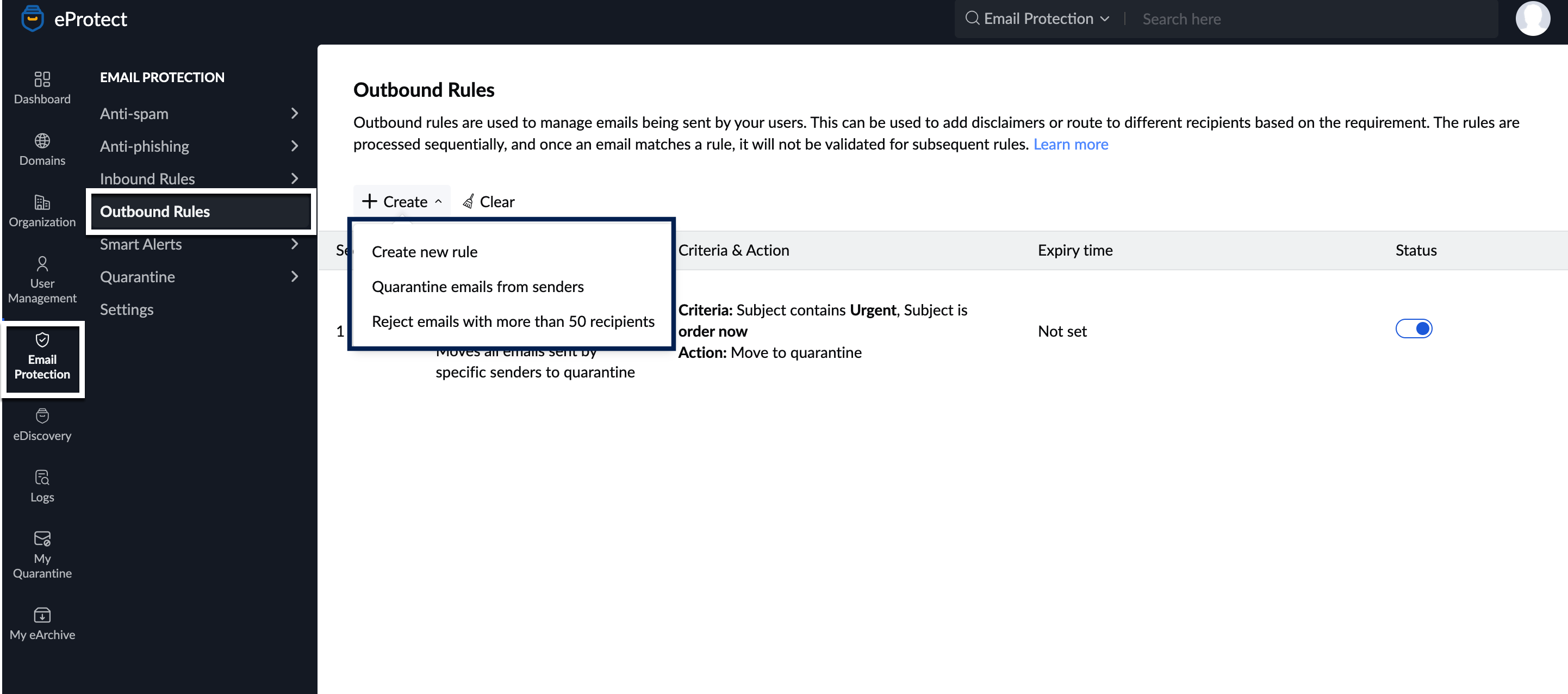
- Select the preferred option:
- Create new rule
- Quarantine emails from senders
- Reject emails with more than 50 recipients
- Enter a rule name, provide a description and click Proceed.
- Select a condition type for the rule from the below options:
- AND - Only if the incoming emails satisfy all the conditions you provided, the preferred action will be performed.
- OR - Even if the incoming emails satisfy one of the conditions you provided, the preferred action will be performed.
- Advanced - You can combine both AND & OR condition types, within a single condition, for the preferred action.
- No Condition - When chosen, all the emails you receive will go through the preferred action.
- Set the condition for the rule, choose the operating parameter.
- Click the + icon to add multiple conditions.
Select the desired action and click Proceed.
Action Description Block sender All the emails that satisfy the given condition/s will not be delivered by our servers and email outgoing will be blocked permanently for the sender. Reject All the emails that satisfy the given condition/s will not be delivered by our servers and a default warning message will be sent upon rejection. Reject with a custom message All the emails that satisfy the given condition/s will not be delivered by our servers and a custom warning message will be sent upon rejection Move to quarantine The emails that satisfy the given condition/s will be moved to quarantine for the administrator's approval. - After creating the filter, you can choose to which users you want the rule to be applied from Choose user dropdown. You can select one of the options below.
- All Users - The rule will be applied to all the users in your organization.
- Selected Users - The rule will be applied to the specific set of users you add.
- All users excluding selected users - The rule will be applied to all the users except the ones added to the list.
- To add users to the Selected Users or Excluded users list, simply select the respective option, and click the Add button. Select the users you want to add to the list and click Proceed. You can also remove a user from the list by clicking the Delete icon next to the user.
- Once done, click Proceed. On the preview page, you can review your rule and set an expiry date if needed.
- After reviewing your rule, you can,
- Create & Enable Rule - Your rule will not only be created but also be activated automatically to start processing emails with respect to its conditions and actions.
- Create Rule - Your rule will only be created and not activated. That means if you want the rule to be applied to the emails you receive, you will have to manually activate it.
Available Conditions
You can set up more than one condition in a single rule depending on your requirement.
| Parameter | Description |
| Subject | The subject of the email |
| From email address | The sender email address of the outgoing mail. |
| Display Name | The display name of the sender |
| Sender (group) | Checks if the sender belongs to an organisation group |
| Original sender's email address | Email address of the actual sender of the outgoing mail |
| Sender's email policy | The email policy applied to the sender |
| Reply-to- email address | The reverse-path/ bounce address of an outgoing email. |
| Originating country | The country from which the email was sent |
| To/Cc email address | The 'To' or 'cc' email address of the outgoing mail. |
| Recipient domain | The domain name of the email recipient. |
| Recipient count in the email | The maximum number of recipients permitted in an outgoing email. |
| Email language | The language in which the email was composed. |
| Sender IP address | The IP address of the email sender. |
| MIME message ID* | The ID present in the MIME email's header. |
| X-Mailer** | The desktop client from which the email was sent. |
| User-agent | The software/ Client used to send the emails. |
| URL domain | The domain names of the URLs available in the email content. |
| MIME size (in MB) | The non-text attachment exceeds the specified size. |
| Attachment type | The type of attachments present in the email |
| Suspicious login activity | Checks for any suspicious login activity of the sender |
| Has macros | The existence of macros in the email content. |
| Has suspicious macros | The existence of suspicious macros in the email content. |
| Has attachment | The existence of attachments in the email content. |
| Attachment size (in MB) | Attachment that exceeds the specified size. |
Note:
- *MIME message - Multipurpose Internet Mail Extensions supports non-text email attachments. A MIME header is added to the original email header from where you can gather the unique content ID/message ID used to identify the message.
- **X-Mailer - Specifies which desktop client (For example, Apple client, Thunderbird, etc) was used to draft or send the email. Can be found in the email header.
Operating parameters
| Operators | Description |
| is | The respective parameter in the outcoming email should exactly match the given criteria value. |
| is not | The respective parameter in the outgoing email should not match the given criteria value. |
| contains | The respective parameter in the outgoing email doesn't have to be an exact match but will pass even if it contains the given criteria value. |
| does not contain | The respective parameter in the outgoing email doesn't have to be an exact match but will pass if it does not contain the given criteria value. |
| begins with | The respective parameter in the outgoing email should begin with the given criteria value. |
| ends with | The respective parameter in the outgoing email should end with the given criteria value. |
| is empty | The respective parameter in the outgoing email should be empty. |
| is not empty | The respective parameter in the outgoing email should not be empty. |
| matches | The respective parameter in the outgoing email should match the given criteria value. |
| true | The given condition should be true. |
| false | The given condition should be false. |
| is greater than | The respective parameter in the outgoing email should only be greater than the given criteria value. |
| is lesser than | The respective parameter in the outgoing email should only be lesser than the given criteria value. |
| is greater than or equal to | The respective parameter in the outgoing email can be greater than or equal to the given criteria value. |
| is lesser than or equal to | The respective parameter in the outgoing email can be lesser than or equal to the given criteria value. |
After selecting the Conditions and the Operating parameters, provide the values with respect to the chosen conditions that need to be verified against. Upon providing these proceed to select the Actions that need to be performed for the emails with the chosen conditions.
Rule processing and priority
You can add any number of outbound rules to process different types of outgoing emails. In the case of multiple filters, the sequence of processing will be based on the priority of filters. The filter with the highest priority (1) will take precedence over the filters with lower priority (2). To change the sequence or priority of the filters,
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Outbound Rules.
- On the Outbound Rules page, you will find the list of all filters you have already added.
- Simply rearrange the filters by dragging and dropping them in the order of your preference.
Enable or Disable a rule
You can enable or disable a rule to start or stop filtering.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Outbound Rules.
- On the Outbound Rules page, you will find the list of all filters you have already added.
- Toggle the Status key to ON/OFF in order to Enable or Disable a rule.
Remove expired rules from the list
In case you set an expiry date for the rules, you will find a number of expired conditions in your list. You can remove them by using the Delete option.
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to Outbound Rules.
- On the Outbound Rules page, click the Delete icon
This will remove all the filters that have already expired from your list.
Quarantine
In the quarantine section of Zoho eProtect, you can decide how to process emails that have been quarantined as a result of your Email Protection settings. Both incoming and outgoing quarantined emails can be processed from the respective sections. Further, you can also set up notifications for quarantined emails, and assign certain users to process their quarantined emails.
The Quarantine section in Zoho eProtect lists all the emails that have been quarantined as a result of the spam processing configured. From the Quarantine section, admins can choose to deliver or deny the emails. Further, notifications can also be configured for the quarantined emails to ensure that they are not missed.
Table of Contents
Quarantined Emails
The emails that are considered spam due to any validation errors, organization blocklists, or Zoho blocklists are listed in the Quarantine section. As an administrator, you can optionally move such emails for review based on the spam processing settings.
Incoming Quarantine
To access and moderate the incoming quarantined emails, follow these steps:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Select Quarantine. The Quarantined Emails tab under the Incoming section, displays the emails awaiting moderation.
- Click on an email to review its contents and the email headers in detail.
- Select the Deliver or Deny options as per your requirement.
To know more about the options available refer to the Delivering emails and Denying emails sections.
Outgoing Quarantine
To access and moderate the outgoing quarantined emails, follow these steps:
- Log in to Zoho eProtect and select Email Protection on the left pane.
- Navigate to the Outgoing section under Quarantine. The Quarantined Emails tab displays the outgoing emails awaiting moderation.
- Click on an email to review its contents and the email headers in detail.
- Select the Deliver or Deny options as per your requirement.
To know more about the options available refer to the Delivering emails and Denying emails sections.
Delivered emails
When you select one or more emails to deliver, you can choose how you want to deliver them.
- Deliver selected - Only those quarantined emails you selected will be delivered.
- Deliver & Add - Select this option if you wish to add an email address/ domain to the Allowed/Trusted list simultaneously while delivering a quarantined email. After the email is delivered, the email address/domain will be added to the Allowed/Trusted list depending on the quarantine reason.
A dialog box will be displayed asking you to confirm if you wish to add the email address/domain to the Allowed/Trusted list (Refer to the table below for more details). - Deliver partially - Emails which has multiple recipients can be sent to specific users using the Deliver partially option. Select an email which has multiple recipients and select Deliver partially from the drop-down. In the Deliver partially dialog, search for recipients and click Add. After you finish the selection, click Proceed.
The email will be delivered only to the users you selected, after which it will move to the Denied Emails tab. To view the list of delivered and denied recipients, refer here. - Deliver All - All the quarantined emails will be delivered.
Note:
The Deliver partially option appears only if there are multiple recipients for an email. It does not appear if you select more than one email.
Denied emails
While denying quarantined emails, you can choose from one of the four options.
- Deny selected- Only those quarantined emails you selected will be denied.
- Deny & Add- Select this option if you wish to add an email address/ domain to the blocked list simultaneously while denying a quarantined email. After the email is denied, the email address/domain will be added to the blocked list depending on the quarantine reason. A dialog box will be displayed asking you to confirm if you wish to add the email address/domain to the blocked list (Refer to the table below for more details).
- Deny & Notify- Selecting this option will notify the sender of the email that you have denied their email. A dialog box will be displayed asking you to confirm if you wish to send en email notification to the sender that their emails have been denied.
- Deny All- All the quarantined emails will be denied.
Note:
You should select only one email at a time for the Deny & Notify option to appear. The option won't appear if you select multiple emails.
The table lists the different reasons an email can be quarantined and how the sender email/domain to the allowed/blocked list based on the quarantined reason.
| Quarantined reason | On Deliver action | On Deny action |
| SPF Fail | The domain gets added to the Trusted Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| SPF Soft Fail | The domain gets added to the Trusted Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| DKIM Fail | The domain gets added to the Trusted Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| DMARC Fail | The domain gets added to the Trusted Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| DNSBL | The domain gets added to the Trusted Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| Blocked Email | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Blocked Domain | The domain gets added to the Allowed Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| Blocked TLD | The domain gets added to the Allowed Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| Blocked IP | The email address gets added to the Allowed emails list. | The domain gets added to the Blocked Domains list with Reject action. |
| Cousin Domain Spam | The domain gets added to the Allowed Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| Blocked sender pattern | The domain gets added to the Allowed Domains list. | The domain gets added to the Blocked Domains list with Reject action. |
| Blocked subject pattern | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Blocked content pattern | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Display Name Spoofing | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Quarantined Country | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Blocked recipient | The email address gets added to the Allowed emails list. | The email address gets added to the Blocked emails list with Reject action. |
| Org spam settings | The email address gets added to the Trusted emails list. | The email address gets added to the Blocked emails list with Reject action. |
You can also search for specific quarantined emails based on the available criteria. The search can be performed based on criteria such as Subject, Sender, To or Cc, Email Content, Attachment Name, Attachment Content or Date. By default, the entire message will be searched.
Further, you can also use the Filter option to select the particular validation failure of quarantined emails and filter out those emails which match the criteria.
A notification email can be sent to the recipient of the quarantined email and a selected admin each time an email is quarantined. The quarantine section should be monitored regularly, and if there is a particular pattern in legitimate emails being quarantined, the spam processing settings of the organization can be adjusted accordingly.
Delivered and Denied Emails
In Zoho eProtect, the quarantined emails that have been approved or rejected can be viewed under the Delivered Emails and Denied Emails tabs respectively in the Quarantine section. All the information including the reason for quarantine and the date the emails were quarantined gets listed so that you can always have a complete record of those emails you had quarantined. You can export the list of delivered and denied emails by clicking on the Export icon placed on top of the list.
If you wish to deliver any email under Denied Emails, you can do so by selecting that email and clicking the Deliver button placed above the list or the Deliver icon which appears when you hover over any user. To deliver multiple denied emails, select the emails and click on the Deliver button. To deliver all the denied emails, simply select all the emails, click the Deliver drop-down and select the Deliver all option.
Emails that were delivered partially will have an info icon adjacent to the recipients list. When you click the info icon, the Email delivery/denial status dialog appears with the details of delivered and denied recipients.
Quarantine Settings
Quarantine Notifications
When an email is quarantined due to the failure of any of the spam checks, the admin can choose to trigger a notification email. This email will be sent to all the selected admins. You can control whether you want to send the notification email to the corresponding recipients by enabling/disabling email notifications for the recipients.
Similarly, when an email that is sent to a group is quarantined, the notification email will be sent to the group moderator. If the group does not have a moderator, it will be sent to the organization admin.
The notification email will contain details such as the sender of the quarantined email, the email subject, the date and time at which the email was sent and the reason why it was quarantined.
Follow these steps to set up quarantine notifications:
- Log in to Zoho eProtect and select Email Protection in the left pane.
- Select Quarantine Settings under the Quarantine section.
- Switch the toggle across Incoming Email Notification to ON in the Notifications tab.
- Select how often you'd like to receive notifications from the Notification email frequency drop-down.
- If you want to send an email to the corresponding recipients, check the box which says, Send quarantine notification email to recipients. If you wish to send the email only to the selected admins, uncheck the box.
- Click the plus icon and add the admins you'd like to notify about quarantined emails.
Based on the frequency set, an email containing the details of all the quarantined emails in that duration will be sent to the selected admins. If you have enabled email notification for the recipients, the corresponding details will be sent to the recipients to whom the quarantined email is addressed.
Self Moderators
Aside from administrators being able to manage the quarantined emails, you can also assign your organization users as Self Moderators to approve the quarantined emails. However, the self-moderators will only be able to approve those quarantined emails that are addressed to them. If a particular quarantined email contains multiple recipients, the email will be delivered only to the user who approves it.
For example, say there are two users named Rebecca and Paula, and Rebecca has been assigned as a moderator. There's a quarantined email from a sender id name@company1.com addressed to them both. If Rebecca approves the email, the email will be delivered only to her. You can view your corresponding archived emails in the My eArchive section.
To add a self-moderator, follow these steps:
- Log in to Zoho eProtect and select Email Protection in the left pane.
- Select Quarantine Settings under the Quarantine section.
- Select the Self Moderators tab.
- Click on the Add button (+). The Self Moderators pop-up window opens with a list of all the organization users.
- Click the Add button to add a user to the Selected users portion of the window. You can also search for users using the search bar in the pop-up window.
- After selecting the users, click Add.
Users can now view the quarantined emails from the My Quarantine section.
You can also remove users from the self-moderator role if you wish. To remove a self-moderator, follow these steps:
- Navigate to the Self moderators tab, hover over the user who you wish to remove, and click on the Delete icon next to the user.
- To remove multiple users, select the desired users.
- Click on the Delete button displayed above the list.
- You can also delete individual users by clicking on the Delete icon appearing next to each user when you hover over them
eProtect Settings
If you haven't enabled email protection for your emails, you can do so by turning on email protection in the Email Protection's Settings section. Turn on the Email protection toggle button to enable email protection for your emails.

Note:
If the admin denies an email before the self-moderator could approve and deliver it to their inbox, the self-moderator can't approve the email later.
























