What are digital signatures?
Digital signatures are the modern day alternatives to physical signatures and seals. They make the signing process secure and documents unforgeable. Digital signatures attach a digital fingerprint onto your document and checks for alterations throughout the document's life-cycle. In this process, any unauthorized alterations made to the documents are detected and the recipients are notified. Digital signatures have proven to make the process of signing documents extremely secure, authentic, and non-repudiable. They are also legally binding and accepted globally.
How do digital signatures work?
This is how the process works:
SENDER SIDE
- The sender uploads a document, fills in the document details, adds recipients, and sends it out for signatures.
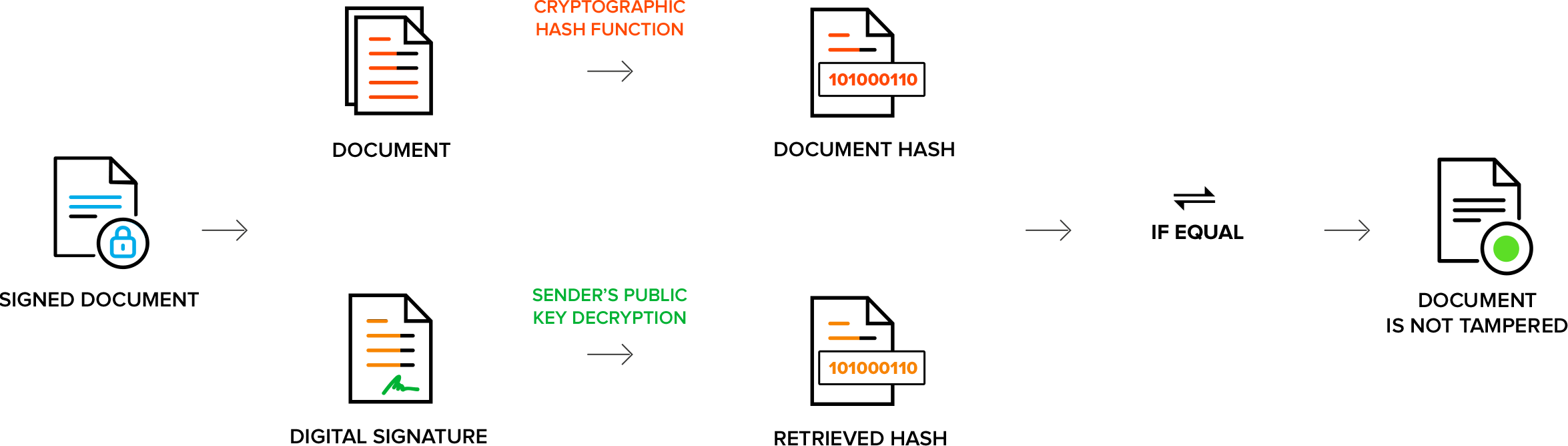
- A cryptographic hash is then generated for the document.
- The generated hash is encrypted using the sender's private key. (the private key is stored in a secure HSM box).
- The encrypted hash is then appended to the document.
- The encrypted document is sent to recipients along with the sender's public key certificate.

RECIPIENT SIDE
- The recipient receives the document with the sender's public key certificate attached.
- The recipient then decrypts the encrypted hash using the sender's public key certificate.
- The hash generated by the sender is obtained upon decryption.
- A cryptographic hash is again generated for the document on the recipient's end.
- Both cryptographic hashes are compared with each other. If both are the same, then the document hasn't been tampered with.
Why use digital signatures?
Digital signatures makes the whole process of document signing extremely secure. There are many advantages to this method.
Digital signatures provide authenticity, integrity, and are non-repudiative.
Authenticity.
Digital signatures ensure active participation by the signatories by securely storing their private keys while sharing the public key with other recipients. Some digital signature services, such as Zoho Sign, store their private keys in a highly secure hardware security module (HSM box) to ensure authenticity.


Integrity.
The cryptographic hash functions added on top of each document depend on that document's content. Any small change to the document will affect the hash, indicating that the document has been tampered with. In this way, it is impossible to modify the contents of a document without being detected.
Non-Repudiation.
Documents signed using digital signatures leave a digital fingerprint. Once an user signs a document, they cannot claim its illegitimacy. Zoho Sign provides a complete audit trail of all signatories and their activities along with timestamps and IP addresses.