OAuth 2.0 for FSM APIs
OAuth 2.0 is an industry-standard protocol for authorization. It allows external applications (clients) to gain access to Zoho FSM's resources, via APIs. A token- based authorization is used which involves the exchange of user approved access tokens between the Client and an Authorization server.
Why use OAuth2?
- Zoho FSM's credentials need not be exposed to the Client.
- The access to user resources is regulated by set of defined scopes.
- The access token expires within a limited period and thus reducing the chance of the user data getting hacked.
How OAuth2.0 works?
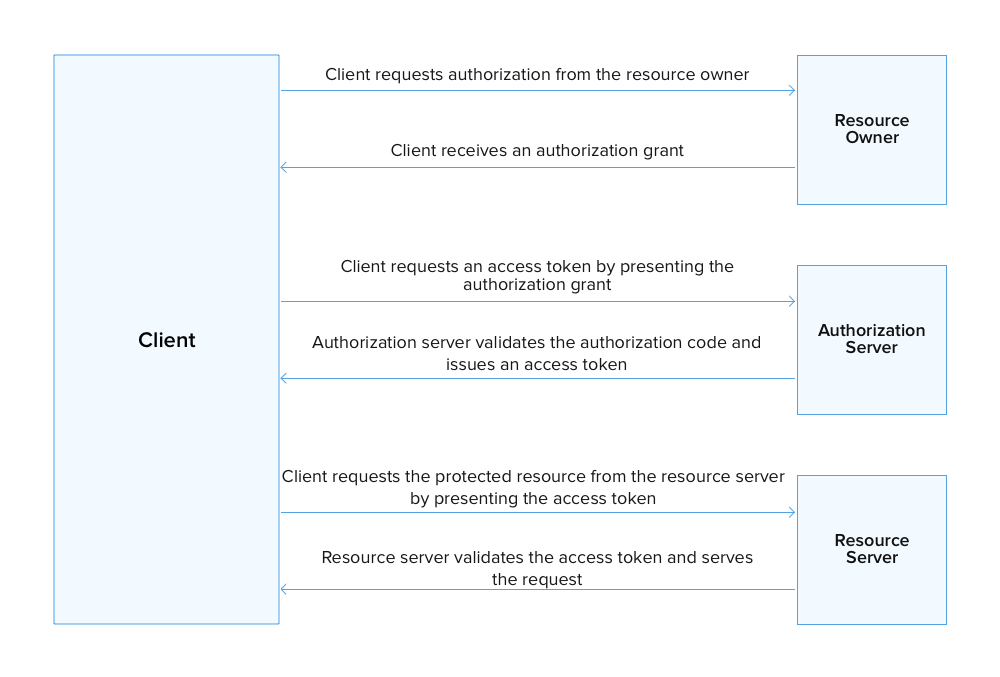
Terminologies
Following are some terms you need to know before you start using the Zoho FSM APIs.
Protected resources
The Zoho FSM resources, such as Requests, Estimates, Work Orders, etc.
Resource server
The server that hosts the OAuth2-protected resources owned by the user. In our case, it is the Zoho FSM server.
Resource owner
The end users of Zoho FSM who have the authority to grant access to the resources hosted on the resource server.
Client
The application, which on behalf of the resource owner sends API requests to the resource server to access the protected resources.
Client ID
The consumer key generated from the connected application.
Client Secret
The consumer secret generated from the connected application.
Authentication server
Authorization server provides the necessary credentials (such as Access and Refresh tokens) to the client. In this case, it will be the Zoho FSM authorization server.
Authentication code
The temporary code that is generated by authorization server and passed on to the client via a browser. This temporary token is used by the client to obtain the access and refresh tokens from the authorization server.
Tokens
Access Token
A token that is sent to the resource server to access the protected resources of the user. The Access token provides a secure and temporary access to Zoho FSM APIs and is used by the applications to make requests to the connected app. Each access token will be valid only for an hour, and can be used only for the set of operations that is described in the scope.
Refresh Token
A token that can be used to obtain new access tokens. This token has an unlimited lifetime until it is revoked by the end user.