Elevate to Admin Mode on Windows OS
During a remote session, attempting to perform admin-level operations such as using Run as administrator or accessing secure desktops like Windows UAC may cause screen freezing for technicians. To perform these tasks and gain admin privileges, the Assist application must be elevated using the Elevate to Admin Mode option.
Session Elevation Methods
There are two primary methods to elevate a session to Admin Mode:
- Technician-Side Elevation: The technician initiates the elevation process and enters admin credentials.
- End User Elevation: The customer is prompted to enter admin credentials from their end.
Technician-Side Elevation
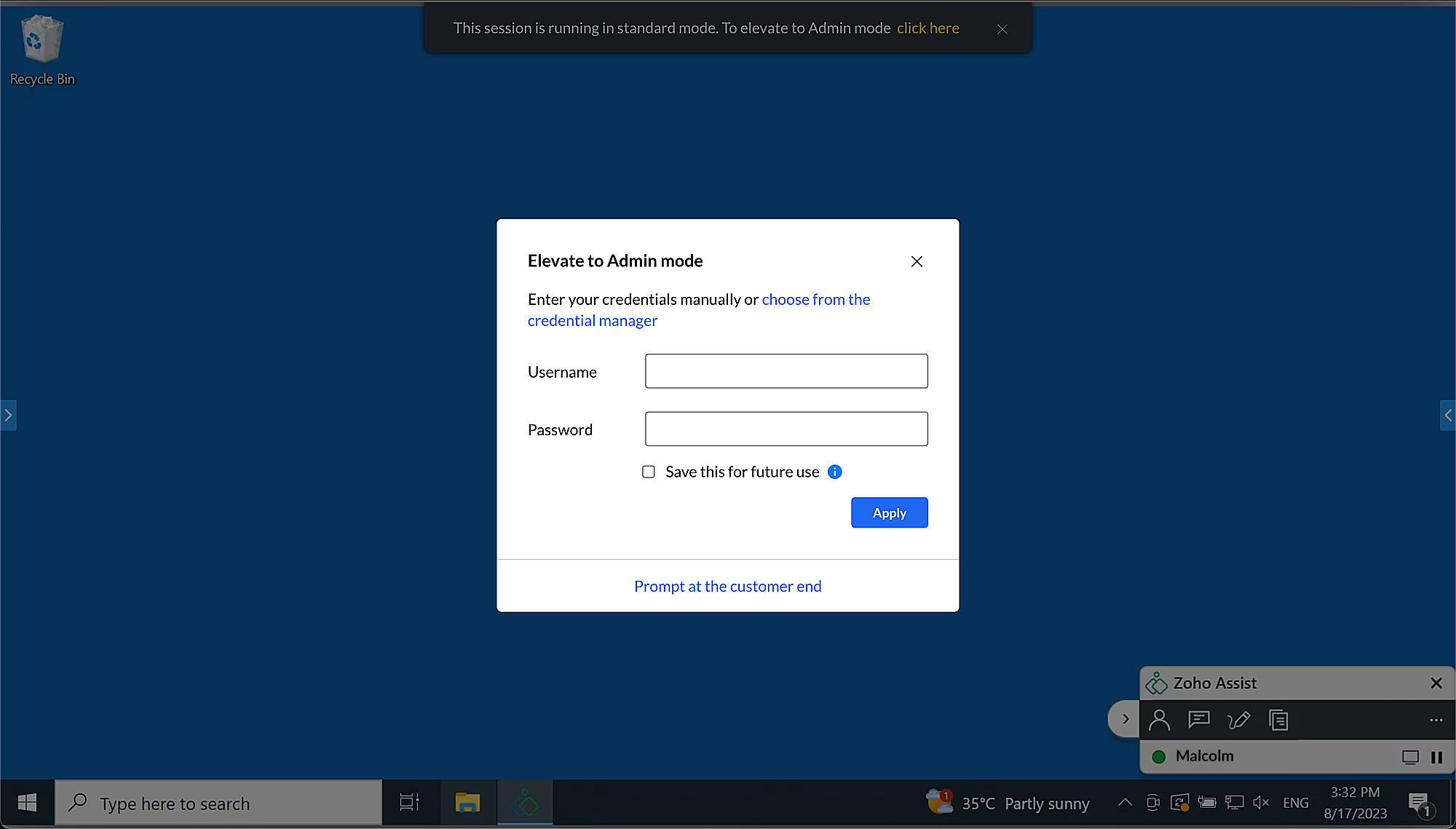
Elevate to Admin Mode by entering credentials manually
Navigate to Session > Elevate to Admin Mode.
Enter the credentials manually in the prompt and click Apply.
- The entered admin credentials should be in one of the following formats:
- <domain>\username
- <machine_name>\username
- username@domain
Note: Credentials will only be saved if they’re successfully validated on the customer’s device.

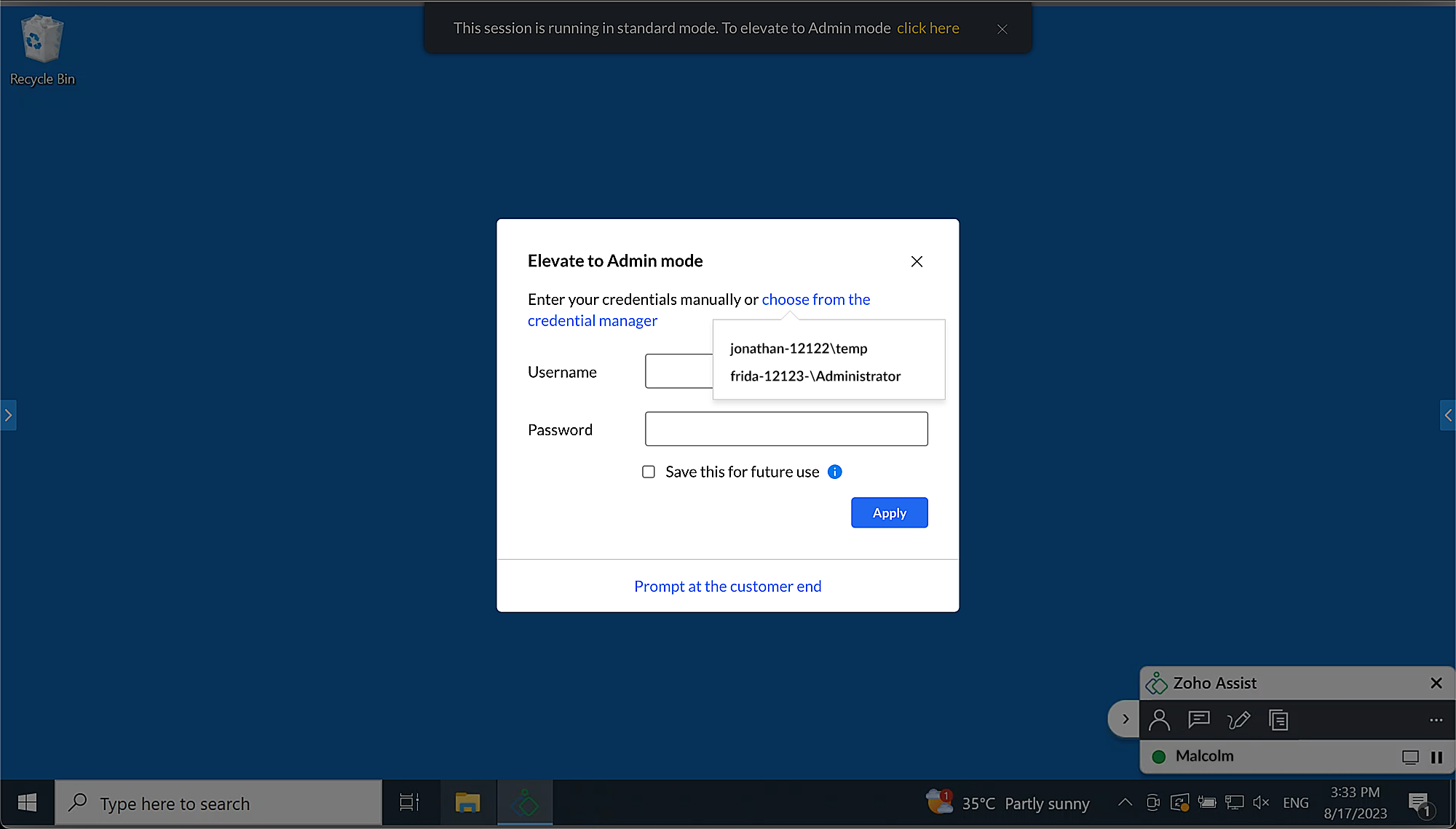
Elevate to Admin Mode using the Credential Manager
Alternatively, you can use saved credentials from the Credential Manager.
- Navigate to Session > Elevate to Admin Mode.
- Click Choose from the Credential Manager to select saved credentials.
Select the appropriate credentials from the Credential Manager and click Apply.
Learn more about the Credential Manager
End User Elevation
The elevation API supports the following authentication mechanisms:
- Local Admin User Authentication
- Physical/Virtual Smartcard Admin User Authentication (on the remote machine)
Note: Operating systems prior to Windows Vista support only Local Admin User Authentication.
Things to note before elevation
- The user credential provided in the Assist UAC dialog must be a member of the Windows Administrator group.
- You must have access to
%localappdata%,%programdata%, and%programfiles (x86)%folder paths with Read/Write/Execute/Modify permissions. Learn more about troubleshooting steps.
Local Admin User Authentication
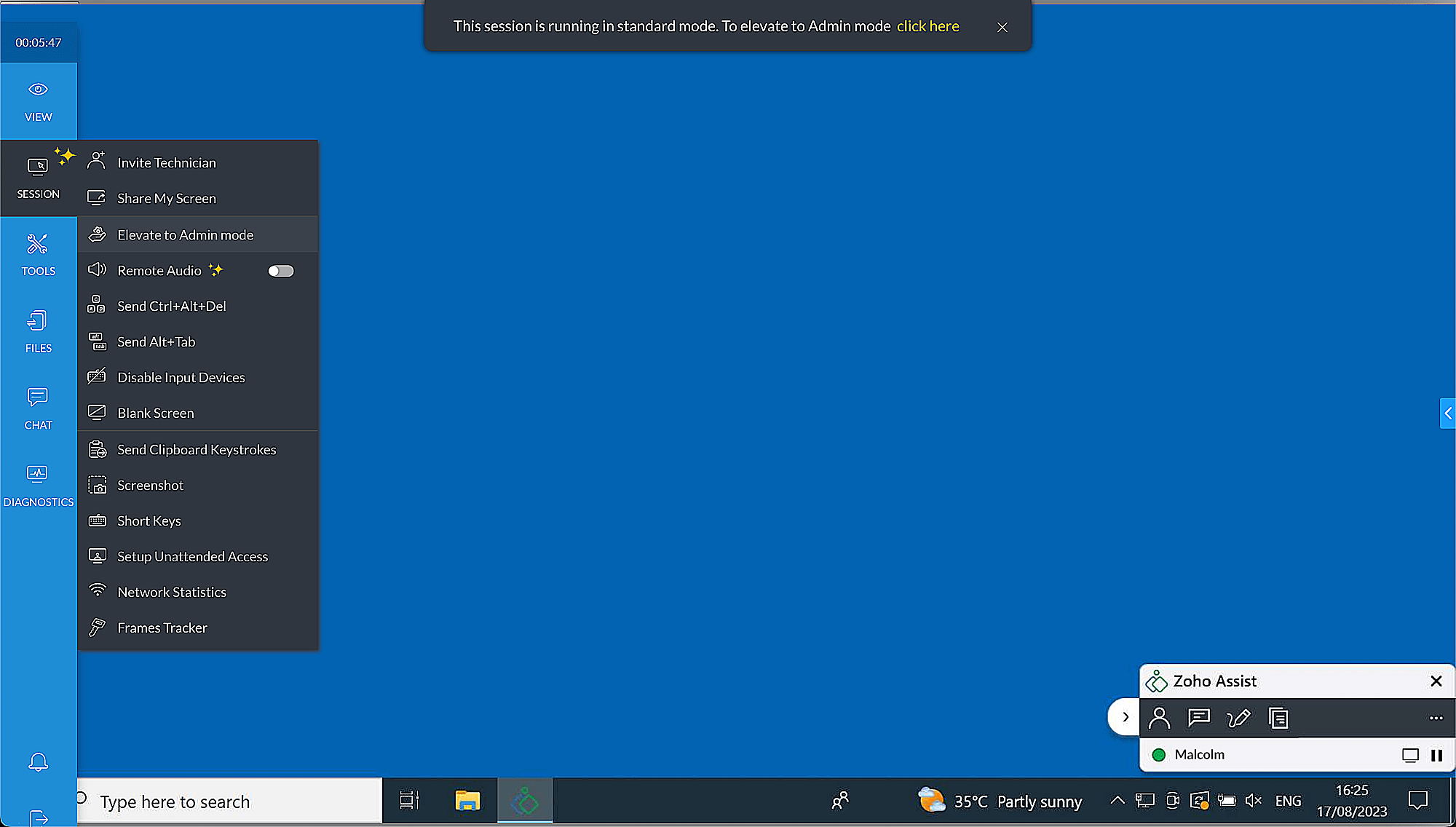
- Once the Technician Console opens, go to Session > Elevate to Admin Mode.
Click Prompt at the customer end to request credentials.
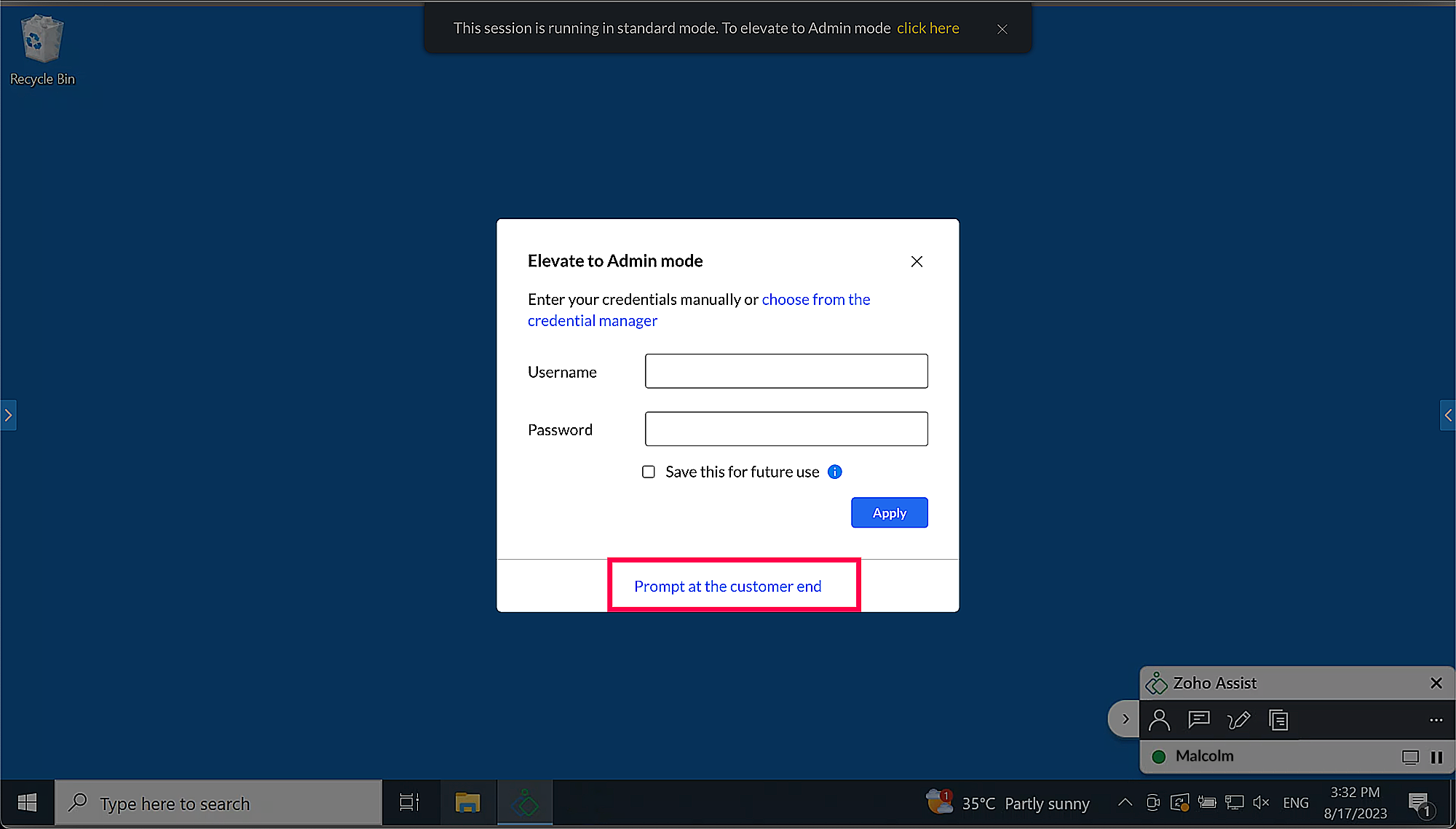
A prompt will open on the remote device. The customer or technician can enter the credentials in the Assist UAC.
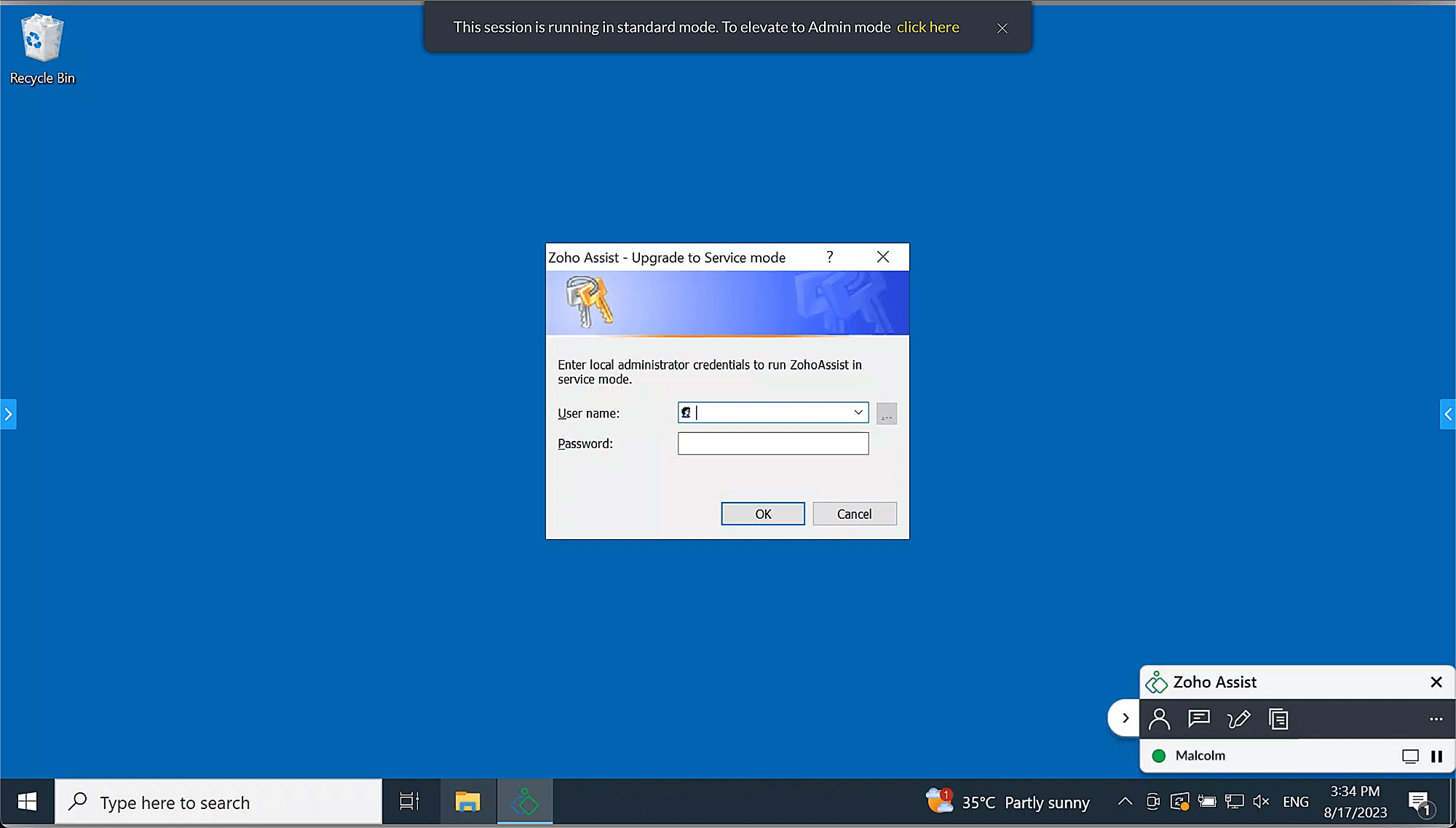
- Choose from pre-populated admin names or enter credentials manually in the following format:
- <domain>\username
- <machine_name>\username
- username@domain
Once credentials are validated, the Windows UAC consent popup will appear at the remote end. The customer must select Yes to proceed.
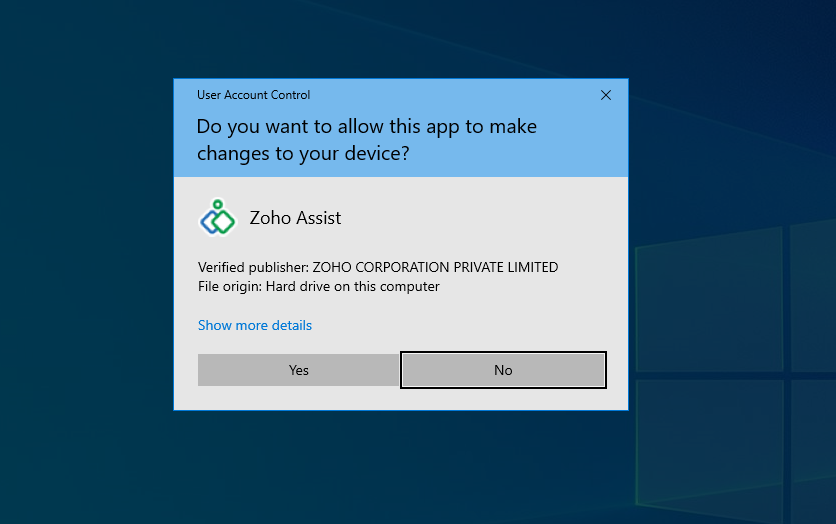
The technician’s screen will display the elevation status as shown below.

Once elevation is successful, a notification will appear on the technician’s end.

Note: If the customer joins using an admin account, there’s no need to enter credentials. The UAC window will prompt for approval—clicking Yes starts the session in Admin Mode, while No starts it in standard mode.
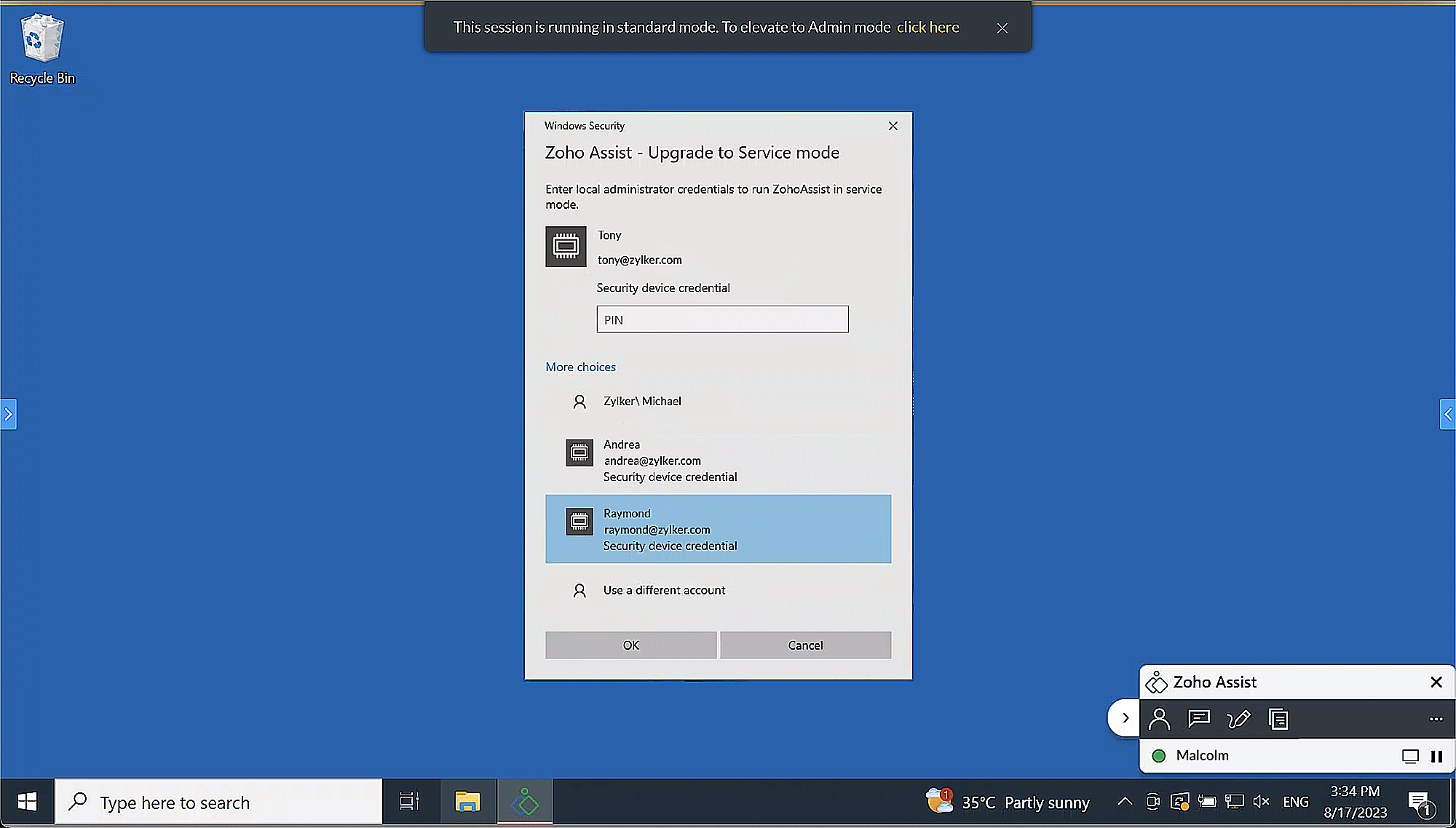
Smart Card
Smart cards are portable storage devices that enhance security by authenticating clients, signing code, securing emails, and allowing Windows domain login. They protect private keys and personal data through tamper-resistant storage.
Physical Smart Card vs Virtual Smart Card
| Physical Smart Card | Virtual Smart Card |
| Protects private keys using smart card media. | Protects private keys using the TPM of the computer. |
| The smart card must be configured on the remote device and inserted into the reader. | Virtual configuration must be done on the remote device via TPM. |
Smart Card Authentication
To elevate Assist using smart card admin credentials, select Prompt at the customer end on the technician side.
Select the smart card username option and enter the respective PIN.